-
Notifications
You must be signed in to change notification settings - Fork 496
[DISCUSSION] Solution without closed source dependencys #75
Comments
|
I agree, there should maybe some abstract wrapper class or interface that encapsulates the Google Play Services stuff. Especially as Google already mentioned that the play services stuff may move to core Android (maybe AOSP). Also Huawei may have another variant of the same API without play services on their newer phones. |
|
Here is a good example of a GSM free fork: https://f-droid.org/de/packages/org.telegram.messenger/ While the original Telegram app uses GSM, in example for location sharing, the fork is 100% GSM free, without losing any functionality (in this case they use Open Street Maps iirc). Removing the Google dependency could also improve the user acceptance by wiping concerns against US big data companies. |
|
Personally, I can only encourage you to build a libre version of the ENA API for Android. My personal advice to you: Fork this repo, give it a new name (e.g. CoraLibre or CoronaLibre) and integrate it with your libre ENA API. Try to change as few as possible of the upstream code so you can stay really close to this upstream repository. If you have a working fork, completely libre, and some minor changes in the upstream code base would help you to integrate the upstream commits (e.g. by doing some Dependency Injection here and there) feel free to create PRs. We will definitely accept no code changes that have impact on the UX (e.g. the mentioned Android notification hack). All the best, PS: Please be careful when publishing your app: Afaik you may not use the Corona-Warn-App name, brand, logo and designs. |
Then in the foreseeable future, it will not be possible for everyone to use the app. I'm using a Fairphone 2 with their Google free Fairphone Open OS, no GSM available. So the question is: Why is it necessary to use the Google APIs for this app? Are there any technical reasons? I think the most important feature for such an app is, to make it available to the biggest user spectrum possible. But when using Google APIs this target can't be reached. :-( |
|
@MalteJ That is great! Thank you for the reply. So I guess the next thing is to somehow be able to write a libre ENA API that is compatible to Privacy-Preserving Contact Tracing. The question was can it be pulled off and has someone experiment with it already? |
I think using Googles / Apples solution is the only option for now, since the development of an own "Google free" solution would cost time and money. |
I do not know any project that is trying to create a compatible API. But I know a few folks that would be very interested in such a project and maybe could also help. @theScrabi Are you an Android developer? Can you start developing such an API? |
|
I am an android developer, however I am not sure if I could write such an API as I have little experience with bluetooth and that API (yet). I started to read my self into the documentation and prestandard DP-3T and I think to see some parallels, so maybe by modifying prestandard DP-3T android sdk it might be possible to create a compatible API, but I don't know for certain right now. |
|
@theScrabi you will find most of the documentation here: I think when you start developing a lib there will appear some helping hands from the community 🙂 Feel free to post a link to your project in this thread! |
|
So I've been researching a bit more, as I try to persue the idea of modifying the prestandart dp-3t android sdk. So here is a comparison of both based on what I found out so far (no assurance for accuracy, please correct me if I am wrong): The Broadcasting in both cases is send as Payload of the BLE Advertising packages. One thing that concerned me a little is that the App apparently can not see the received The next thing I will do is frok the prestandard DP-3T android sdk and try to get it working so we can start modifying it :) |
|
Here is the repository of the CoraLibre-android-sdk. So far it still contains the prestandard DP-3T android sdk. |
|
@MalteJ you said we can not use the name or the package name of "Corona-Warn-App" which is ok. We will not, but can we leave the paths of the package names of the java files? If not pulling changes from this repo will get harder as files are going to be stored in different locations. |
|
You just shouldn't use the name for any marketing stuff. I don't care about path names. :) |
|
We are making progress. The prototype of the encryption core for the Apple/Google is done. It needs to be verified by a security expert: @MalteJ According to this file, page 11, Apple/Google hand out test vectors if you kindly ask them. Do you know if these testvectors are public available or who I can kindly ask to get them? |
|
Great project and amazing work so far, thanks for the effort @theScrabi. One question: Does the work need to have location services on all the time to ensure the background scanning? |
|
Good question. I'd guess if the app uses a "priviliged extention" then no, if you install it on a phone without root access that probably yes. |
|
@theScrabi Unfortunately I cannot provide you any data that we got under NDA. |
The Apple documentation on ENExposureConfiguration explains that algorithm. |
I don't have official test vectors either, but when I wanted to verify that this implementation is correct, I used a "live" Android device (Android 9, GMS 20.18.17) to generate TEKs, RPIs and AEM (and the Raspberry Pi setup to receive RPIs and AEM). Another valid combination is this Hope this helps - any questions, let me know :) |
I found the answer. Seems like you have to enable location mode in order to get Android to locate the Bluetooth device. It is a privacy orientated feature. if its disabled, every Android device will send the same Bluetooth-ID |
You are right, it's a privacy oriented feature. What Google wants to prevent is this scenario: An app does not get permission from the user to access location, and then still tracks the user's location by BLE-scanning for fixed-position BLE beacons (iBeacons in stores, museums, etc). Totally different use case, but leads to the requirement to ask the user for location permission, even though the location isn't used within the app. Regarding the BDADDR: I found that my Android device (MTK chipset) advertises random BDADDR like 4f:31:14:1c:d7:20, 59:7b:48:03:e7:c9, 60:a5:86:6f:9a:d3, 77:11:8d:93:f9:d4, ... |
That's unfortunately also different to the "official" Google Play Services: There your app is NOT allowed to have location services. This is one reason why the official CWA app can't implement both things at same time:
Both at same time wont work as you app would not be accepted for Play Store. Actually the approach with Google Play Services is in my opion better for privacy! It sounds strange, but actually the app itsself can't track the location of users if you separate the BLE tracking from the COVID19 app (what Apple and Google do). The play services are a separate service implemented on a lower level in the operating system. Those have all required permissions to do the BLE scanning, but don't expose any privacy critical information to the COVID19 app. That's well thought! |
|
@uschindler While I think you are right regarding the standard approach "Corona-Warn-App on a GMS Android Device", |
|
I think it may be good to consider possible consequences of publishing open implementations of EN, normally I'm on board with fully open-source solutions, but it seems that in this particular case (distributed approach) it will enable easy "nerd attack":
It's already easy to build an app on e.g. Raspberry PI zero W which collects RPIs together with exact timestamp and GPS location, and then matches these RPIs with published TEKs (which can be continuously fetched with simple curl cron job since it seems that there will be no safeguards like Device Attestation). Then adversary will be able to determine exact time and location of contact with infected person, which in turn may result in easy identification of this person. This capability could be limited to developers who can implement this from scratch, but with open implementation I guess this attack vector may be much more popular. Keep in mind that users of official app are told that:
and right before turning on broadcasting of RPIs further assured that:
This is true if only official apps will be in use, but once we have enriched apps (developed based on open EN implementation) which provide fine-grained information about the encounters then above statement no longer holds. I'm a big supporter on fully open-source / libre software and I think a solution where users don't have to create Google account in order to participate in contact tracing would be much better, but unfortunately current approach does not ensure full privacy by design and open implementation may enable more adversaries to violate privacy of others. For those who don't want to use Google products one possible solution is to get cheap used Android phone from eBay, create fake Google account and carry it in another pocket (e.g. Motorola G2 which is capable of running EN costs 25-30 EUR). If you decide to go forward with publishing EN implementation just make sure that it does not violate any licenses from Google / Apple (e.g. Beacon Simulator app developer had to remove iBeacon format implementation from public source code, despite the fact that iBeacon specification is open) |
|
@kbobrowski One opposing view would be "Theoretically, it would be possible to follow a user, collect the user's RPIs, connect them with person-identifying data, and then check if the person is ever marked as infected. Yet, in practice, this attack vector to deanonymize a user requires a high amount of effort just to gain little additional information compared to the one already gathered while following the user." (quoted from here) Also we should consider that the CoraLibre-android-sdk discussed above aims at replacing the GMS EN API, not the corona-warn-app. A "nerd attacker" could already today use either GMS EN, or other cheap hardware like you mentioned, and doesn't need to wait for this open/libre implementation of the API. |
|
@mh- I don't fully agree with this quote from documentation, adversary just need to get a single RPI to determine if person who broadcast this RPI was within infectious period during encounter, there is no need to follow this person with "high amount of effort", couple of seconds in the same room is enough. You are of course right that already today "nerd hacker" could use custom implementation of EN, but as long as there is no popular open EN implementation this attacker would at least need to know how to implement it from scratch. This is not black or white situation, I'm sure some people would be doing these "nerd attacks" anyway, but with easily accessible open implementations of EN the situation may have a bit darker shade of grey. I just wonder about risk-reward ratio of developing alternative EN implementation as open-source, it's fine if someone who can do it does it for own responsible use, it's simple enough that it does not require community effort to develop. Developing it in open will enable more Google-free users to participate in contact tracing effort but at the same time will increase number of adversaries who otherwise would not have enough coding skills to perform "nerd attacks", potentially undermining trust in this system. Difficult to judge net outcome. |
|
@kbobrowski "nerd attacker" could already today use the original Google EN implementation, once an official app is installed and activated, it will start collecting RPIs. |
|
@mh- I don't exactly see how attacker could use official app for "nerd attacks", maybe by turning Bluetooth only next to the person whose infectious status attacker wants to determine but it would be very error-prone and require "high amount of effort" due to longer time required to stay in close contact. With custom EN implementation it's much more precise and require much less effort. Or do you mean reverse-engineering like using Frida to hijack some functions which interact with Google's EN? Or disabling signature check such that custom app can interact with Google's EN? But then again it requires higher level of skill which limits potential attackers. |
|
Just as a heads-up: the fork from https://codeberg.org/corona-contact-tracing-germany/cwa-android seems to work fine, and will hit the F-Droid repo this week (hopefully) 😃 |
|
CWA: 0 CCTG: 1 Did my second PCR test today and reinstalled CWA to track it, fully knowing the main functionality wouldn't work. The test tracking worked last october or november, not so today - same hardware, same major LineageOS version (Mi8 "dipper", 16.0). The people on the 0800754* hotline have zero concept about the issues involved and could not even hint that there is indeed a better alternative. CCTG (as linked by Izzy, installed via FDroid) works without a hitch, clean information flow, clean granting of permissions, scanned my QR on the first try (back then I had to use an external app for that, but at least CWA allowed manual entry back then).... IMHO if the CWA developers really respect their users (and I do believe they do), they should consider detecting a no-gapps / LOS configuration and pointing users to CCTG! Big thanks to all involved, and especially to the CWA devs for laying the groundwork for CCTG! |
|
@SomeTroglodyte
Is this correct? |
CWA is unable to even start the scanner API with only microG but without genuine g00gle play services. You get a toast to update google services, that's all. I assume tracking tests would probably still work if the option to copy/paste the code from a separate scan app were still there. I only learned about CCTG after observing that CWA wouldn't serve. And yes, CCTG has no issues with the scanning API. CCTG isn't running perfectly (it favours its bundled microg over my preinstalled one) but then I'm running 12 month old OS bits... If CWA works better on microG-LOS-17.1 I'll inform you here, but that will take a while thanks to privacy guard being gone. |
|
@SomeTroglodyte
That's sad, indeed. And I must confess, I do not understand why the scanner module needs that dependency.
Like proposed here? corona-warn-app/cwa-wishlist#227 Probably the upcoming event registration feature that also relies on the scanner api will have similar caveats. Good you can make use of CCTG. All thumbs up to @fynngodau and company. |
And as for the thumbs up - true, but the CWA team also deserves some of that praise as without clean coding practices for the libre portions of CWA the fork wouldn't have its current quality this quickly... |
|
@mtwalli What is the reasoning for closing this issue? |
|
@rugk FYI: #5885 (comment) |
|
@mtwalli is the only person who can say exactly why he closed the issue, but taken in context I'm seeing a lot of issues being closed at this time where no further action is planned. The official website https://www.coronawarn.app/en/faq/results/#ramp_down now has a place-holder for ramp-down topics as the project is being closed down. Going back through the history, the Open Source team wrote almost 3 years ago in #75 (comment) "In the foreseeable future the Corona-Warn-App project will rely on the official Google and Apple APIs!" and there hasn't been any change from the statement since then. My impression is that the issue was left open as a convenience to the community, not because RKI ever had plans to develop a solution without using Google / Apple dependencies. The community-developed CCTG already fulfils the needs. See |
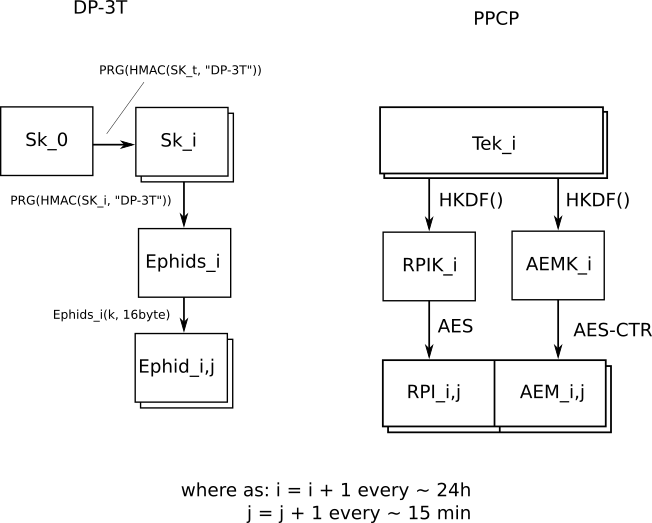
EDIT: tl;dr: We are working an an open implementation of the Google/Apple protocol (I call it PPCP, which may be wrong). You can find and contribute to our repository here: https://github.com/theScrabi/CoraLibre-android-sdk
Dear Corona-Warn-App developpers we have read your code and documentation. We like your effort and your open mind for the community. As there is a small but willing comunity of people who refuse to use closed source Google or Apple dependency and so can not use the Corona-Warn-App, I'd like to discuss the posibility of a Google Free FLOSS solution.
What we know so far is that it's currently hardly possible to create the corona app without the use of the closed source GMS. This comes along with the nearby android exposure notification API, which implements the PPCP protocol. From what we can see in the code so far, the contact points between the android exposure notification API and the Corona-Warn-App are few as for the most common calls to the API a wrapper class is used. That's great! Also there are only about 14 code files that include parts from the GMS library. We therefor think it might be feasible to create a version of the app that does not require GSM services.
As statet in this issue the current maintainer have no plans to implement an own exposure notificatoin API, but might be open to support an alternative if available.
What we understand so far is that the part that runs the actual BLE contact tracing as well as providing a highlevel API for exposure likelihood and key handling would need to be reimplemented. We had several thoughts about how this might be possible.
If a community based solution is possible what would be the next steps to go?
Internal Tracking ID: EXPOSUREAPP-5775
The text was updated successfully, but these errors were encountered: