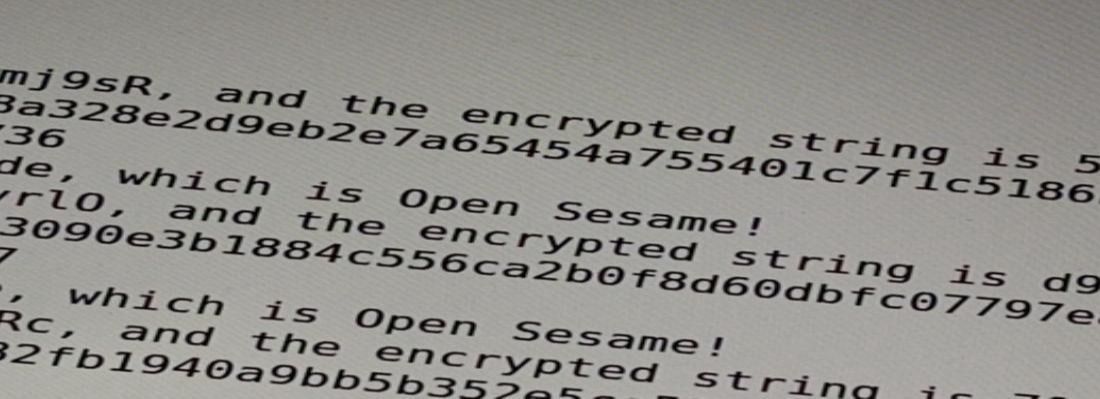
 Here you will learn how to encrypt and decrypt data using a password, also known as symmetrical encryption.
Here you will learn how to encrypt and decrypt data using a password, also known as symmetrical encryption.
 How to keep API secrets and keep peace of mind.
How to keep API secrets and keep peace of mind.
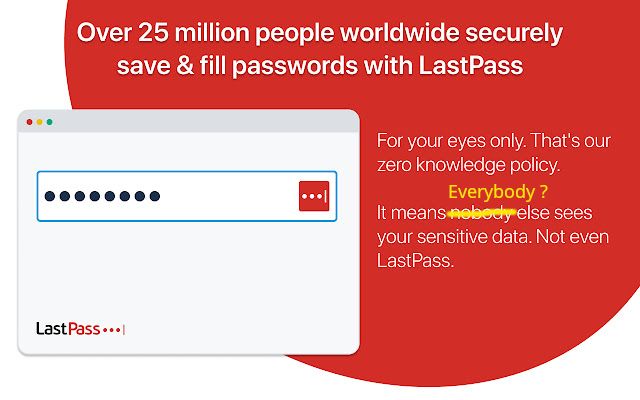
 As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
 Encryption is a way of encoding human-readable data with encrypted code that enables the use of a password to view the source and data stored.
Encryption is a way of encoding human-readable data with encrypted code that enables the use of a password to view the source and data stored.
 How Edgar Allan Poe introduced early cryptography to the masses as a master cipher solver — engaging tech, literary, and crypto communities to this day.
How Edgar Allan Poe introduced early cryptography to the masses as a master cipher solver — engaging tech, literary, and crypto communities to this day.
 TLS/SSL Decryption is a central pillar to the Zero Trust Security Model as it helps prevent the blind spots created by encryption.
TLS/SSL Decryption is a central pillar to the Zero Trust Security Model as it helps prevent the blind spots created by encryption.
 There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
 XOR is a simple bitwise operation that allows cryptographers to create strong encryption systems.
XOR is a simple bitwise operation that allows cryptographers to create strong encryption systems.
 This is a topic that has been talked about quite a bit, but I think it's an important one to reiterate to our users.
This is a topic that has been talked about quite a bit, but I think it's an important one to reiterate to our users.
 FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
 A simple tutorial to learn Encryption in NodeJS.
A simple tutorial to learn Encryption in NodeJS.
 Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
 VPNs has grown in demand in recent years among individuals are using it to secure their information and data to prevent hackers or for other misuses.
VPNs has grown in demand in recent years among individuals are using it to secure their information and data to prevent hackers or for other misuses.
 A new report now claims that Whatsapp messages are not end-to-end encrypted.
A new report now claims that Whatsapp messages are not end-to-end encrypted.
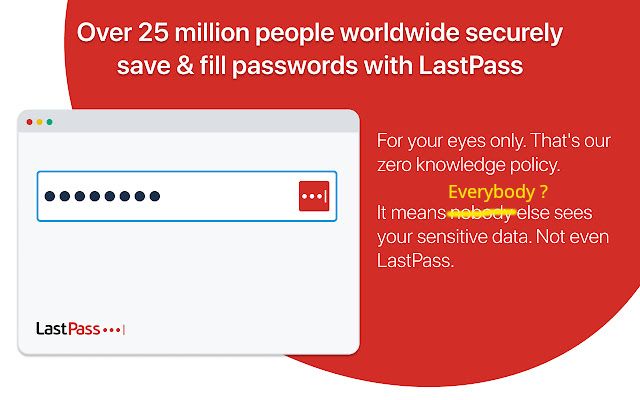 A password vault leak had happened four months ago and LastPass is only telling you that now.
A password vault leak had happened four months ago and LastPass is only telling you that now.
 Organizations nowadays are storing and performing computation of the data on the cloud instead of handling themselves. Cloud Service Providers (CSPs) provide these services at an affordable cost and low maintenance. But to ensure compliance and retain privacy, organizations need to transfer the data in an encrypted format, which does ensure the confidentiality of the data. However, once the data reaches the cloud, the CSP has to decrypt the data to perform operation or computation.
Organizations nowadays are storing and performing computation of the data on the cloud instead of handling themselves. Cloud Service Providers (CSPs) provide these services at an affordable cost and low maintenance. But to ensure compliance and retain privacy, organizations need to transfer the data in an encrypted format, which does ensure the confidentiality of the data. However, once the data reaches the cloud, the CSP has to decrypt the data to perform operation or computation.
 Imagine, you are messaging your business partner about a super secret idea, it is worth $ 1m, will you trust the messaging application not to read your super secret conversation? No, right. No one will, still people across the world use whatsapp for such sensitive messaging (although I prefer telegram for my secret conversations). Well, turns out, it is because most messaging apps(including whatsapp) use a technique called End to End Encryption, which doesn’t allow these messaging services or their employees to read your conversations with your contacts. But how does this works, well, that is what we will try to understand here.
Imagine, you are messaging your business partner about a super secret idea, it is worth $ 1m, will you trust the messaging application not to read your super secret conversation? No, right. No one will, still people across the world use whatsapp for such sensitive messaging (although I prefer telegram for my secret conversations). Well, turns out, it is because most messaging apps(including whatsapp) use a technique called End to End Encryption, which doesn’t allow these messaging services or their employees to read your conversations with your contacts. But how does this works, well, that is what we will try to understand here.
 With two recent vulnerabilities making headlines this month, notably CVE-2019-14899, impacting VPNs running on Linux distros and Atlassian’s zero-day flaw reported by SwiftOnSecurity concerning leak of private keys, it should be no surprise anymore as to why encryption merely breeds a feeling of security rather than guaranteeing it.
With two recent vulnerabilities making headlines this month, notably CVE-2019-14899, impacting VPNs running on Linux distros and Atlassian’s zero-day flaw reported by SwiftOnSecurity concerning leak of private keys, it should be no surprise anymore as to why encryption merely breeds a feeling of security rather than guaranteeing it.
 Our company is called FortKnoxster. We are a cybersecurity company focused on the crypto space.
Our company is called FortKnoxster. We are a cybersecurity company focused on the crypto space.
 The Second World War brought to the front burner the world of espionage, which is the precursor of cybersecurity, as is seen in the modern world. Technological advancements such as the quantum computer necessitate that we take the war against cybercrimes to another level.
The Second World War brought to the front burner the world of espionage, which is the precursor of cybersecurity, as is seen in the modern world. Technological advancements such as the quantum computer necessitate that we take the war against cybercrimes to another level.
 A brief guide on how to create encrypted containers in Linux using Cryptsetup, giving you tools for keeping your most important files and data protected.
A brief guide on how to create encrypted containers in Linux using Cryptsetup, giving you tools for keeping your most important files and data protected.
 TripleBlind has created a new data privacy solution that enables highly-regulated enterprises to share data without ever decrypting it.
TripleBlind has created a new data privacy solution that enables highly-regulated enterprises to share data without ever decrypting it.
 Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
 The reason XOR is so special in cryptography
The reason XOR is so special in cryptography
 Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
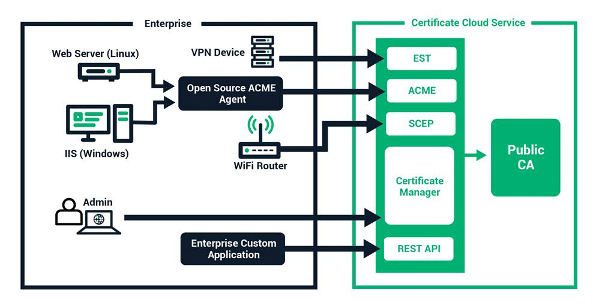
 Don't know what a CA bundle is? Discover how to use its powerful SSL encryption for secure web server-browser communication, why it's important, and more!
Don't know what a CA bundle is? Discover how to use its powerful SSL encryption for secure web server-browser communication, why it's important, and more!
 1/23/2023: Top 5 stories on the Hackernoon homepage!
1/23/2023: Top 5 stories on the Hackernoon homepage!
 A look at updated encryption standards based on strides in quantum cryptography.
A look at updated encryption standards based on strides in quantum cryptography.
 Earlier, we lived in industrial and post-industrial societies, and gas and oil were the only things of value. Now, it’s the age of information society and data has replaced petrol as the economy’s driving force. The reason is that with the help of Big Data, people significantly improve production efficiency and business economics. That’s true.
Earlier, we lived in industrial and post-industrial societies, and gas and oil were the only things of value. Now, it’s the age of information society and data has replaced petrol as the economy’s driving force. The reason is that with the help of Big Data, people significantly improve production efficiency and business economics. That’s true.
 If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
 Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
 By default the aws cli stored key id and secret in plaintext in a well known location. What could go wrong?!?
By default the aws cli stored key id and secret in plaintext in a well known location. What could go wrong?!?
 Is quantum cryptography the next best thing to AES Symmetric Encryption? Let’s find out. Read through a detailed excerpt of how quantum is used in cryptography
Is quantum cryptography the next best thing to AES Symmetric Encryption? Let’s find out. Read through a detailed excerpt of how quantum is used in cryptography
 Today Zoom acquired Keybase. It came as a shock to me at first; but, it shouldn't surprise us.
Today Zoom acquired Keybase. It came as a shock to me at first; but, it shouldn't surprise us.
 Everyone knows it’s a good idea to use strong, unique passwords, and as employees around the world have been forced to work remotely, logging in from multiple devices and multiple locations, the need for strong password security has only grown. But last year’s Verizon Data Breach Investigations Report (DBIR) revealed that weak or compromised credentials still cause 80% of hacking-related breaches. Throughout the current pandemic, attackers have been scouring remote workforce applications to gather and sell user credentials on the dark web, even targeting healthcare organizations such as the National Institutes of Health and the World Health Organization.
Everyone knows it’s a good idea to use strong, unique passwords, and as employees around the world have been forced to work remotely, logging in from multiple devices and multiple locations, the need for strong password security has only grown. But last year’s Verizon Data Breach Investigations Report (DBIR) revealed that weak or compromised credentials still cause 80% of hacking-related breaches. Throughout the current pandemic, attackers have been scouring remote workforce applications to gather and sell user credentials on the dark web, even targeting healthcare organizations such as the National Institutes of Health and the World Health Organization.
 There are several security concepts and techniques, but each one has its purpose and I will introduce their concepts and practices in this article.
There are several security concepts and techniques, but each one has its purpose and I will introduce their concepts and practices in this article.
 We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
 Telegram is not the gold-standard for secure messaging that it paints itself to be. Here are 7 reasons why.
Telegram is not the gold-standard for secure messaging that it paints itself to be. Here are 7 reasons why.
 Cryptography is the core of cryptocurrency, and without it, none of the transactions will be secured, nor the integrity of any information is upheld.
Cryptography is the core of cryptocurrency, and without it, none of the transactions will be secured, nor the integrity of any information is upheld.
 Exploring fully homomorphic encryption which, for a long time been considered one of the holy grails of cryptography.
Exploring fully homomorphic encryption which, for a long time been considered one of the holy grails of cryptography.
 A selection of programs for online privacy. All of them will help you not to fall prey to hackers and keep your data safe.
A selection of programs for online privacy. All of them will help you not to fall prey to hackers and keep your data safe.
 In a world where encryption of our messaging apps is at stake, is there a solution that works? Aside from the traditional WhatsApp and Signal, there's Usecrypt.
In a world where encryption of our messaging apps is at stake, is there a solution that works? Aside from the traditional WhatsApp and Signal, there's Usecrypt.
 One of the biggest challenges we netizens encounter is defending freedom and human rights on the internet.
One of the biggest challenges we netizens encounter is defending freedom and human rights on the internet.
 End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
 Envelope encryption is a good way of maintaining your cybersecurity at scale, without tying up a significant portion of your resources on less efficient methods
Envelope encryption is a good way of maintaining your cybersecurity at scale, without tying up a significant portion of your resources on less efficient methods
 Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
 It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
 In 2019 our devices know us better than close friends and relatives. Browsers, messengers, social media trackers analyse the actions you do online and your interactions with content to expand their manipulation. The history of browsing is used to target ads and create more triggering banners for you exclusively. These technological advancements might look smart and comfortable, but the invasion of privacy has gone too far.
In 2019 our devices know us better than close friends and relatives. Browsers, messengers, social media trackers analyse the actions you do online and your interactions with content to expand their manipulation. The history of browsing is used to target ads and create more triggering banners for you exclusively. These technological advancements might look smart and comfortable, but the invasion of privacy has gone too far.
 The article today explains the email encryption requirement and how correctly adopting email encryption can help achieve and maintain HIPAA Compliance
The article today explains the email encryption requirement and how correctly adopting email encryption can help achieve and maintain HIPAA Compliance
 This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
 With secure messaging apps willing to cease operations, UK's attempt to fight cybercrime with its Online Safety Bill has sparked the encryption debate again.
With secure messaging apps willing to cease operations, UK's attempt to fight cybercrime with its Online Safety Bill has sparked the encryption debate again.
 One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
 How to use a Synology Active Backup to protect your SharePoint Data by using the Active Backup feature from Microsoft 365 alongside DiskStation Manager 7
How to use a Synology Active Backup to protect your SharePoint Data by using the Active Backup feature from Microsoft 365 alongside DiskStation Manager 7
 If you’re like millions around the world getting ready to head back to school this fall, you’re figuring our first, if your campus will even be open, and second, how to adjust to the idea of distance learning.
If you’re like millions around the world getting ready to head back to school this fall, you’re figuring our first, if your campus will even be open, and second, how to adjust to the idea of distance learning.
 An easy guide to getting started with online privacy.
An easy guide to getting started with online privacy.
 Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
 The 21st century is the age of technology and the Internet. Today, the whole world is online. We are increasingly moving all our business to the Internet space. It is the place where we work, communicate, order food, pay for purchases, watch movies and listen to music.
The 21st century is the age of technology and the Internet. Today, the whole world is online. We are increasingly moving all our business to the Internet space. It is the place where we work, communicate, order food, pay for purchases, watch movies and listen to music.
 Updated 01/13/2020
Updated 01/13/2020
 How I encrypted, documented, and unit tested my first REST API using PHP, PHPUnit, GuzzleHttp, Next.js, ReactJS, and more.
How I encrypted, documented, and unit tested my first REST API using PHP, PHPUnit, GuzzleHttp, Next.js, ReactJS, and more.
 Table of Content
Table of Content
 We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
 The hype is dead, long live the hype. After deep learning, a new entry is about ready to go on stage. The usual journalists are warming up their keyboards for blogs, news feeds, tweets, in one word, hype. This time it’s all about privacy and data confidentiality. The new words, homomorphic encryption.
The hype is dead, long live the hype. After deep learning, a new entry is about ready to go on stage. The usual journalists are warming up their keyboards for blogs, news feeds, tweets, in one word, hype. This time it’s all about privacy and data confidentiality. The new words, homomorphic encryption.
 Build your own Wireguard VPN on an Amazon EC2 instance - for next to no cost!
Build your own Wireguard VPN on an Amazon EC2 instance - for next to no cost!
 Encrypted messaging apps are great, but taking it another step, we look at how to create an end-to-end encrypted messaging device.
Encrypted messaging apps are great, but taking it another step, we look at how to create an end-to-end encrypted messaging device.
 79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
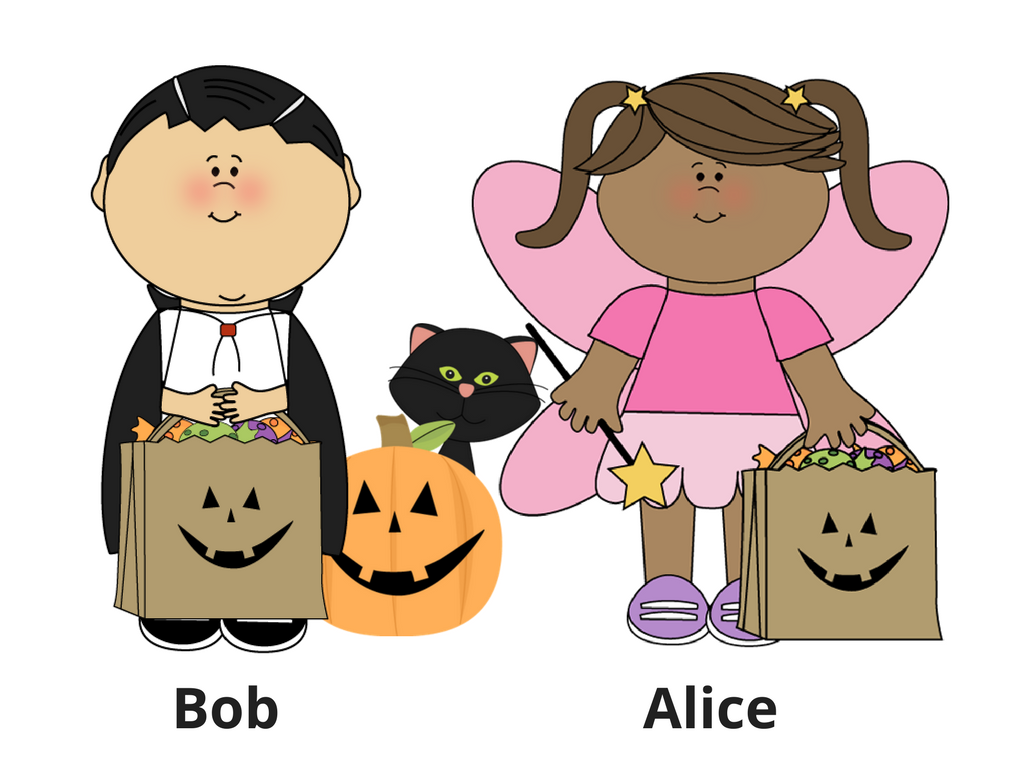 Explaining crypto is hard, explaining crypto in simple words is harder. Explaining Zero Knowledge Proof to a child? Easy! So here you go — ZKP explained with some Halloween candy.
Explaining crypto is hard, explaining crypto in simple words is harder. Explaining Zero Knowledge Proof to a child? Easy! So here you go — ZKP explained with some Halloween candy.
 10 Simple steps on How to Boost Your Digital Security During Remote Work to prevent phishing and hacker attacks.
10 Simple steps on How to Boost Your Digital Security During Remote Work to prevent phishing and hacker attacks.
 Being concerned with the security of online communication and information exchange is absolutely OK. It is a reflection of the fact that you
are aware of global surveillance happening every second of our presence online. Our online activities are monitored, intercepted, collected, and stored. And now imagine that what you know is only the small fraction of what is really happening with our information.
Being concerned with the security of online communication and information exchange is absolutely OK. It is a reflection of the fact that you
are aware of global surveillance happening every second of our presence online. Our online activities are monitored, intercepted, collected, and stored. And now imagine that what you know is only the small fraction of what is really happening with our information.
 Garbled circuits are a quite old, and surprisingly simple, cryptographic primitive and simplest form of general-purpose MPC to wrap your head around.
Garbled circuits are a quite old, and surprisingly simple, cryptographic primitive and simplest form of general-purpose MPC to wrap your head around.
 Here’s what you can do to keep yourself (and your nudes) safe.
Here’s what you can do to keep yourself (and your nudes) safe.
 Trigger warning: authoritarianism, state surveillance, the Holocaust. If you want to avoid these topics, please jump to the last paragraph of this introduction, starting with ‘Enough about the depressing stuff.’
Trigger warning: authoritarianism, state surveillance, the Holocaust. If you want to avoid these topics, please jump to the last paragraph of this introduction, starting with ‘Enough about the depressing stuff.’
 Anyone who has seen the movie The Imitation Game, or studied computer science in school, probably has at least a brief understanding of Enigma, Alan Turing, and some of the other fun cryptography that went on during WWII. During this time and until the 1970's, governments from around the world had near total control of all cryptographic systems.
Anyone who has seen the movie The Imitation Game, or studied computer science in school, probably has at least a brief understanding of Enigma, Alan Turing, and some of the other fun cryptography that went on during WWII. During this time and until the 1970's, governments from around the world had near total control of all cryptographic systems.
 In this article, we will cover how to install a S/MIME i.e., email signing certificate on Outlook, and how to encrypt an email in it.
In this article, we will cover how to install a S/MIME i.e., email signing certificate on Outlook, and how to encrypt an email in it.
 In cryptography, encryption is the conversion of cleartext into a coded text or ciphertext. A ciphertext is intended to be unreadable by unauthorized readers.
In cryptography, encryption is the conversion of cleartext into a coded text or ciphertext. A ciphertext is intended to be unreadable by unauthorized readers.
 Encryption makes the digital world work. It consists of a few elegant math equations that scramble data before being sent over the internet where prying eyes could otherwise intercept it, read it, and manipulate it. Encryption is the reason everything from financial transactions to state secrets get passed around the internet nearly instantaneously, unlocking massive amounts of innovation, wealth, and prosperity as a result.
Encryption makes the digital world work. It consists of a few elegant math equations that scramble data before being sent over the internet where prying eyes could otherwise intercept it, read it, and manipulate it. Encryption is the reason everything from financial transactions to state secrets get passed around the internet nearly instantaneously, unlocking massive amounts of innovation, wealth, and prosperity as a result.
 Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
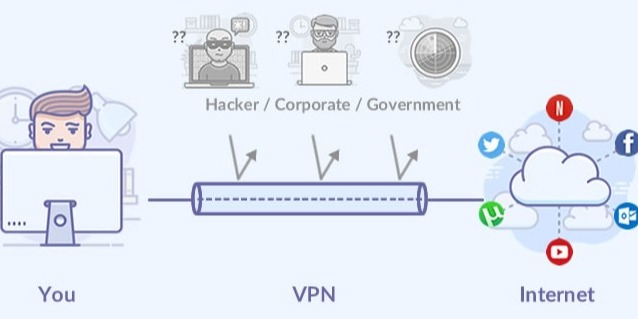
 There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
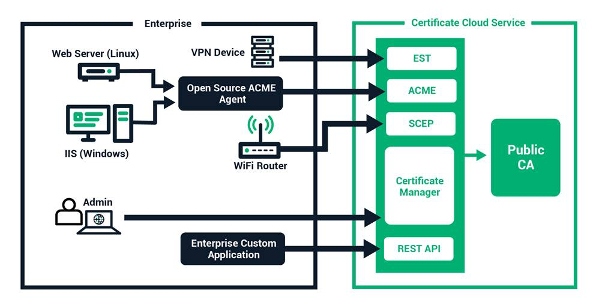 Web certificates are a foundational element of website security, enabling organizations to verify that the web address in question really does belong to them, as well as to keep users secure by encrypting their information. These certificates have become ubiquitous, and most savvy web users now know to look for the telltale indicators of a valid web certificate, which may include a closed padlock or green address bar, depending on the browser used.
Web certificates are a foundational element of website security, enabling organizations to verify that the web address in question really does belong to them, as well as to keep users secure by encrypting their information. These certificates have become ubiquitous, and most savvy web users now know to look for the telltale indicators of a valid web certificate, which may include a closed padlock or green address bar, depending on the browser used.
 As the world finds itself preoccupied with COVID-19, the United States government is trying to pass a law to ban encryption. It's called the EARN IT act, and while it claims to combat the sexual exploitation of children online, it has potentially devastating repercussions for encryption and companies that use it to protect your privacy online.
As the world finds itself preoccupied with COVID-19, the United States government is trying to pass a law to ban encryption. It's called the EARN IT act, and while it claims to combat the sexual exploitation of children online, it has potentially devastating repercussions for encryption and companies that use it to protect your privacy online.
 (Photo by Fanny Rascle on Unsplash)
(Photo by Fanny Rascle on Unsplash)
 This article talks about quantum computing and why it can break encryption in blockchains such as Bitcoin and Ethereum.
This article talks about quantum computing and why it can break encryption in blockchains such as Bitcoin and Ethereum.
 DASH is stated as not a system or a protocol or a demonstration or a codec or interactivity or a client specification
DASH is stated as not a system or a protocol or a demonstration or a codec or interactivity or a client specification
 For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
 “Aren’t all browsers anonymous?”
“Aren’t all browsers anonymous?”
 Add Additional Data Protections to G Suite with the Virtru SDK
Add Additional Data Protections to G Suite with the Virtru SDK
 If you find understanding or explaining the differences between asymmetric and symmetric encryption daunting, then take a relaxing breath — we’ll break it all down into layman’s terms
If you find understanding or explaining the differences between asymmetric and symmetric encryption daunting, then take a relaxing breath — we’ll break it all down into layman’s terms
 Cryptography provides a method for secure communication. It stops unauthorized parties from gaining access to messages between authorized parties.
Cryptography provides a method for secure communication. It stops unauthorized parties from gaining access to messages between authorized parties.
 Where Do I Start?
Where Do I Start?
 It’s Not (Exactly) 1984, but Big Brother Is Certainly Watching!
It’s Not (Exactly) 1984, but Big Brother Is Certainly Watching!
 A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
 This article will be of particular interest to people who are curious about how powerful encryption can be implemented in high performance systems. It is also for people who just want to know a bit more about how strong encryption works and how all the pieces fit together.
This article will be of particular interest to people who are curious about how powerful encryption can be implemented in high performance systems. It is also for people who just want to know a bit more about how strong encryption works and how all the pieces fit together.
 The encryption debate ends now. As a society we simply can’t allow backdoors in encryption. Anyone who tells you otherwise has absolutely no idea how computers work.
The encryption debate ends now. As a society we simply can’t allow backdoors in encryption. Anyone who tells you otherwise has absolutely no idea how computers work.
 On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
 In Part 3 of their series on encryption, Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache discuss end-to-end encryption in practice.
In Part 3 of their series on encryption, Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache discuss end-to-end encryption in practice.
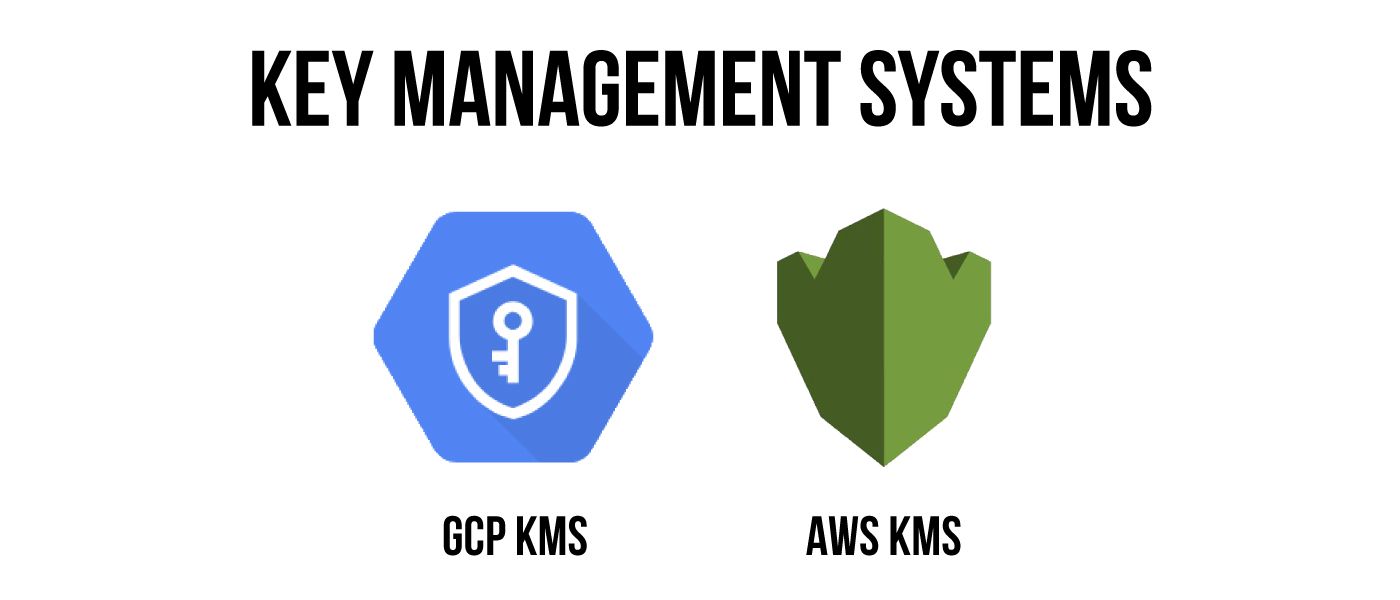
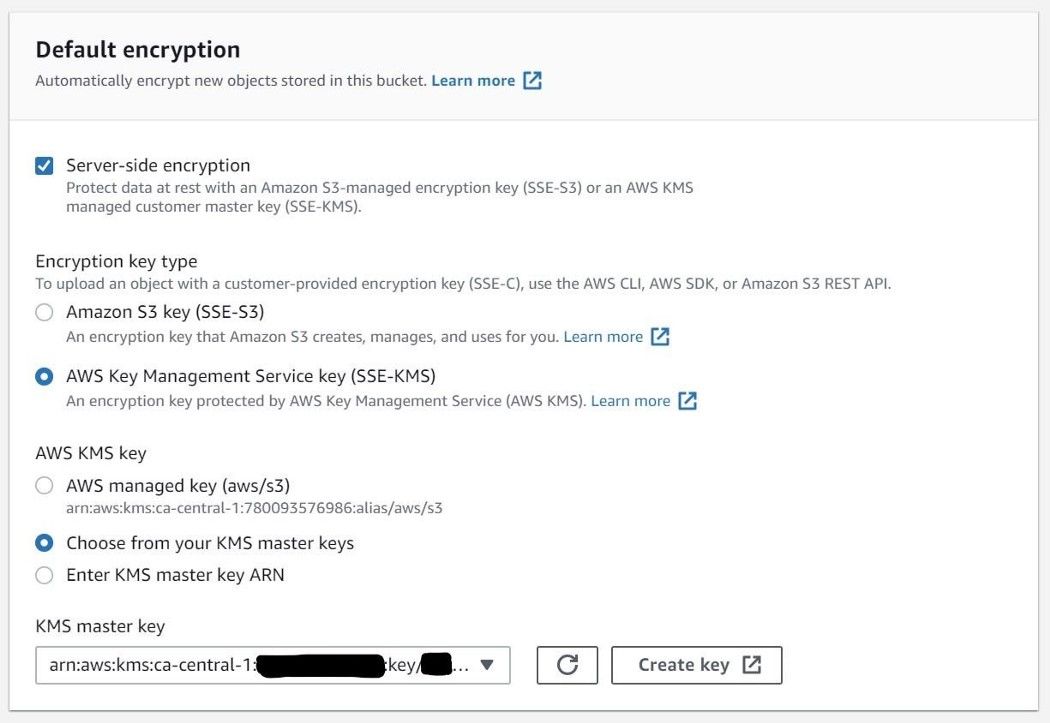 Before we dive into the fun part of getting keys shared amongst cloud providers, there are a variety of tools required to get this tutorial working.
Before we dive into the fun part of getting keys shared amongst cloud providers, there are a variety of tools required to get this tutorial working.
 Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache continue their series on encryption to discuss transport layer security (TLS) in practice.
Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache continue their series on encryption to discuss transport layer security (TLS) in practice.
 This article was first published on our open-source platform, SimpleAsWater.com. If you are interested in IPFS, Libp2p, Ethereum, Zero-knowledge Proofs, DeFi, CryptoEconomics, IPLD, Multiformats, and other Web 3.0 projects, concepts and interactive tutorials, then be sure to check out SimpleAsWater.
This article was first published on our open-source platform, SimpleAsWater.com. If you are interested in IPFS, Libp2p, Ethereum, Zero-knowledge Proofs, DeFi, CryptoEconomics, IPLD, Multiformats, and other Web 3.0 projects, concepts and interactive tutorials, then be sure to check out SimpleAsWater.
 Why You Should Care About Encryption
Why You Should Care About Encryption

 In case you missed the previous article (Part 1), I gave a very brief introduction on Homomorphic Encryption (HE), talked about Microsoft SEAL’s library, and outlined some of the pain points of learning to use it.
In case you missed the previous article (Part 1), I gave a very brief introduction on Homomorphic Encryption (HE), talked about Microsoft SEAL’s library, and outlined some of the pain points of learning to use it.
 In the context of public key cryptography, certificates are a way to prove the identity of the owner of a public key.
In the context of public key cryptography, certificates are a way to prove the identity of the owner of a public key.