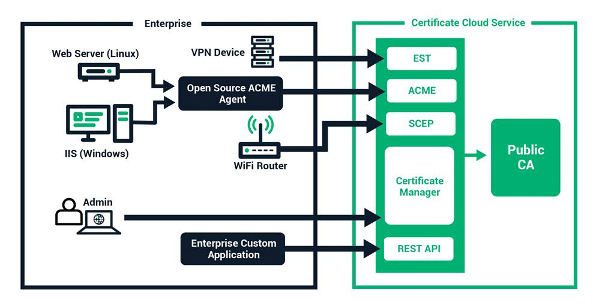
With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
 A reverse shell is a hacking vulnerability that the hacker executes .php codes or an executable file in which he gets access to the shell of the target system.
A reverse shell is a hacking vulnerability that the hacker executes .php codes or an executable file in which he gets access to the shell of the target system.
 Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
 Web application security refers to securing sites and online services against different security threats that abuse vulnerabilities in an application’s code.
Web application security refers to securing sites and online services against different security threats that abuse vulnerabilities in an application’s code.
 A curated list of bug bounty programs for bug bounty hunters to help them get first bug bounty on vulnerability report.
A curated list of bug bounty programs for bug bounty hunters to help them get first bug bounty on vulnerability report.
 What programs can safeguard your computer from malware? In today’s article, we will take a look at VPNs and what it can do to protect you from spying.
What programs can safeguard your computer from malware? In today’s article, we will take a look at VPNs and what it can do to protect you from spying.
 An ad redirecting users to browser hijacking software was recently spotted on CNN's election tracking site. Ahead of election season, it's reason for concern
An ad redirecting users to browser hijacking software was recently spotted on CNN's election tracking site. Ahead of election season, it's reason for concern
 What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
 This a short tutorial on setting up Portable Virtualbox with Kali Linux.
This a short tutorial on setting up Portable Virtualbox with Kali Linux.
 A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
 Hacking is a serious problem for nonprofits. When a hacker attacks, it's not just the nonprofit's information that they want, but donors' information
Hacking is a serious problem for nonprofits. When a hacker attacks, it's not just the nonprofit's information that they want, but donors' information
 If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
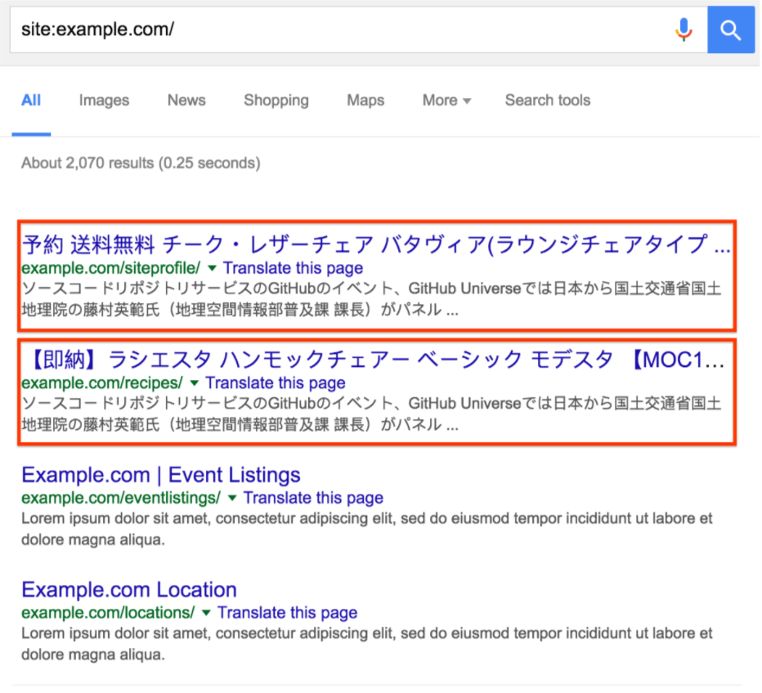 Enhancing security for a website can save it from hackers and online attackers. Read this article about website security to learn more.
Enhancing security for a website can save it from hackers and online attackers. Read this article about website security to learn more.
 Considering today's cyber threat landscape, it is undeniable to say that the internet-facing applications are at major risk due to rapid increase in vulnerability exploits and ways to penetrate applications leveraging the hidden weaknesses in them.
Considering today's cyber threat landscape, it is undeniable to say that the internet-facing applications are at major risk due to rapid increase in vulnerability exploits and ways to penetrate applications leveraging the hidden weaknesses in them.
 It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.
It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.

 Intigriti co-founder, Inti De Ceukelaire, shares their origin story, what makes him excited about his job, and the technology he is currently excited about.
Intigriti co-founder, Inti De Ceukelaire, shares their origin story, what makes him excited about his job, and the technology he is currently excited about.
 Scam advertisements across major media outlets originate from DoubleClick and Xandr/AppNexus
Scam advertisements across major media outlets originate from DoubleClick and Xandr/AppNexus
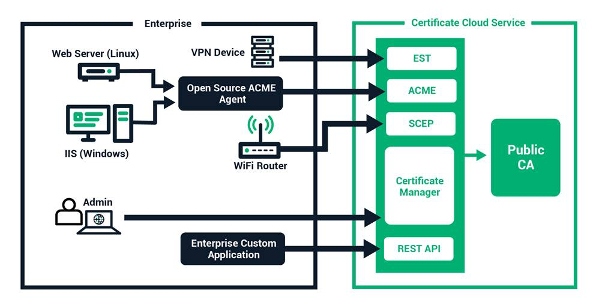 Web certificates are a foundational element of website security, enabling organizations to verify that the web address in question really does belong to them, as well as to keep users secure by encrypting their information. These certificates have become ubiquitous, and most savvy web users now know to look for the telltale indicators of a valid web certificate, which may include a closed padlock or green address bar, depending on the browser used.
Web certificates are a foundational element of website security, enabling organizations to verify that the web address in question really does belong to them, as well as to keep users secure by encrypting their information. These certificates have become ubiquitous, and most savvy web users now know to look for the telltale indicators of a valid web certificate, which may include a closed padlock or green address bar, depending on the browser used.
 What is an HTTP proxy? It is a good way to get information on the Internet while maintaining your privacy. Read my article to get more insights about HTTP proxy
What is an HTTP proxy? It is a good way to get information on the Internet while maintaining your privacy. Read my article to get more insights about HTTP proxy
 Make these mistakes and hackers will attack your web application using Cross Site Scripting, SQL Injection, Path Traversal, and other attacks to take over your website.
Make these mistakes and hackers will attack your web application using Cross Site Scripting, SQL Injection, Path Traversal, and other attacks to take over your website.
 Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
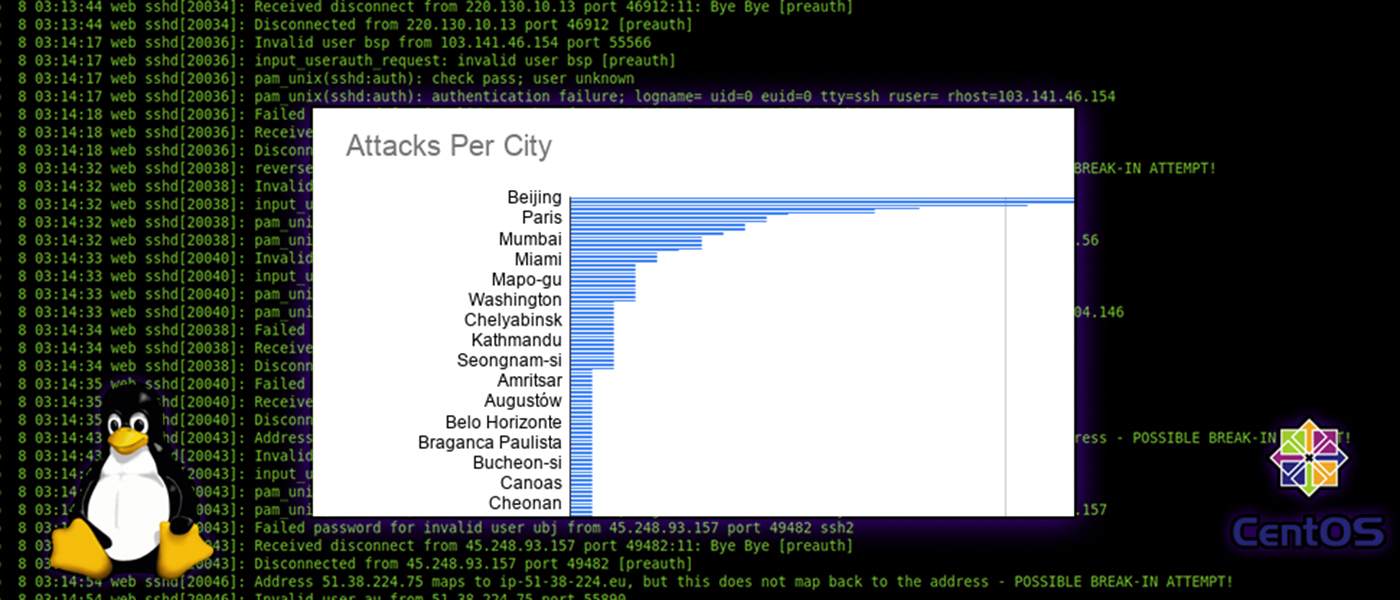 I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
 We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
 Web security is a topic that is often overlooked by frontend developers. When we assess the quality of the website, we often look at metrics like performance, SEO-friendliness, and accessibility, while the website’s capacity to withstand malicious attacks often falls under the radar. And even though the sensitive user data is stored server-side and significant measures must be taken by backend developers to protect the servers, in the end, the responsibility for securing that data is shared between both backend and frontend. While sensitive data may be safely locked in a backend warehouse, the frontend holds the keys to its front door, and stealing them is often the easiest way to gain access.
Web security is a topic that is often overlooked by frontend developers. When we assess the quality of the website, we often look at metrics like performance, SEO-friendliness, and accessibility, while the website’s capacity to withstand malicious attacks often falls under the radar. And even though the sensitive user data is stored server-side and significant measures must be taken by backend developers to protect the servers, in the end, the responsibility for securing that data is shared between both backend and frontend. While sensitive data may be safely locked in a backend warehouse, the frontend holds the keys to its front door, and stealing them is often the easiest way to gain access.
 In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
 Secrets are digital credentials used for authentication and authorization.
Secrets are digital credentials used for authentication and authorization.
 Metadata is “data that provides information about other data” (Wikipedia). In other words, Metadata is “data about data”.
Metadata is “data that provides information about other data” (Wikipedia). In other words, Metadata is “data about data”.
 It's already challenging enough to create a website that is blazing fast, adheres to all the latest best practices and offers optimal experience for various network conditions and device types.
It's already challenging enough to create a website that is blazing fast, adheres to all the latest best practices and offers optimal experience for various network conditions and device types.
As the website and its codebase evolves over time, it can become even harder to maintain the desired user experience over time. To prevent UX deterioration, it’s often a good idea to place guardrails which ensure that crucial website elements, such as images, hold to a certain criteria. In this article, we are going to look at a robust mechanism which helps to steer your website in the right direction - an HTTP header called Feature Policies.
 Every individual or organization must be mindful of securing their online data. Online security is essential for better online data privacy and security.
Every individual or organization must be mindful of securing their online data. Online security is essential for better online data privacy and security.
 JSON Web Tokens have become incredibly popular (especially in the Node.js community) and you've likely heard about them. What you may not have heard is that JWTs were originally designed for use in OAuth - which is fundamentally different to user sessions.
JSON Web Tokens have become incredibly popular (especially in the Node.js community) and you've likely heard about them. What you may not have heard is that JWTs were originally designed for use in OAuth - which is fundamentally different to user sessions.
 You already know web security is important to keeping hackers and cyber-thieves from accessing sensitive information. So, in this post we are going to check Django security vulnerabilities and how to fix them.
You already know web security is important to keeping hackers and cyber-thieves from accessing sensitive information. So, in this post we are going to check Django security vulnerabilities and how to fix them.
 In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
 Security issues of crypto exchanges and shared my thoughts on how to make trading convenient and safe - Viktor Kochetov, CEO at Kyrrex, a digital wallet and professional cryptocurrency trading.
Security issues of crypto exchanges and shared my thoughts on how to make trading convenient and safe - Viktor Kochetov, CEO at Kyrrex, a digital wallet and professional cryptocurrency trading.
 Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
 Working with the latest tech is fun. It’s fresh and exciting. As developers we
feel invigorated by being on the bleeding edge. Consider us thrill
seekers.
Working with the latest tech is fun. It’s fresh and exciting. As developers we
feel invigorated by being on the bleeding edge. Consider us thrill
seekers.
 In this article, we will go through the most common security vulnerabilities encountered in applications that use the OAuth protocol.
In this article, we will go through the most common security vulnerabilities encountered in applications that use the OAuth protocol.
 The basics of how to test and protect your application
The basics of how to test and protect your application
 This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
 How to recognize phishing? Research studies show that users of different levels have a hard time figuring out if a website is real or fake. And how about you?
How to recognize phishing? Research studies show that users of different levels have a hard time figuring out if a website is real or fake. And how about you?
 Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers
Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers
 An array of free website-building tools, many offered by ad-tech and ad-funded companies, has led to a dizzying number of trackers loading on users’ browsers.
An array of free website-building tools, many offered by ad-tech and ad-funded companies, has led to a dizzying number of trackers loading on users’ browsers.
 Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
 As a developer, when you think of security, what comes to mind? Is it clear what are different aspects that need to be handled to make a software secure? And why you need to do that?
As a developer, when you think of security, what comes to mind? Is it clear what are different aspects that need to be handled to make a software secure? And why you need to do that?
 When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.
When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.