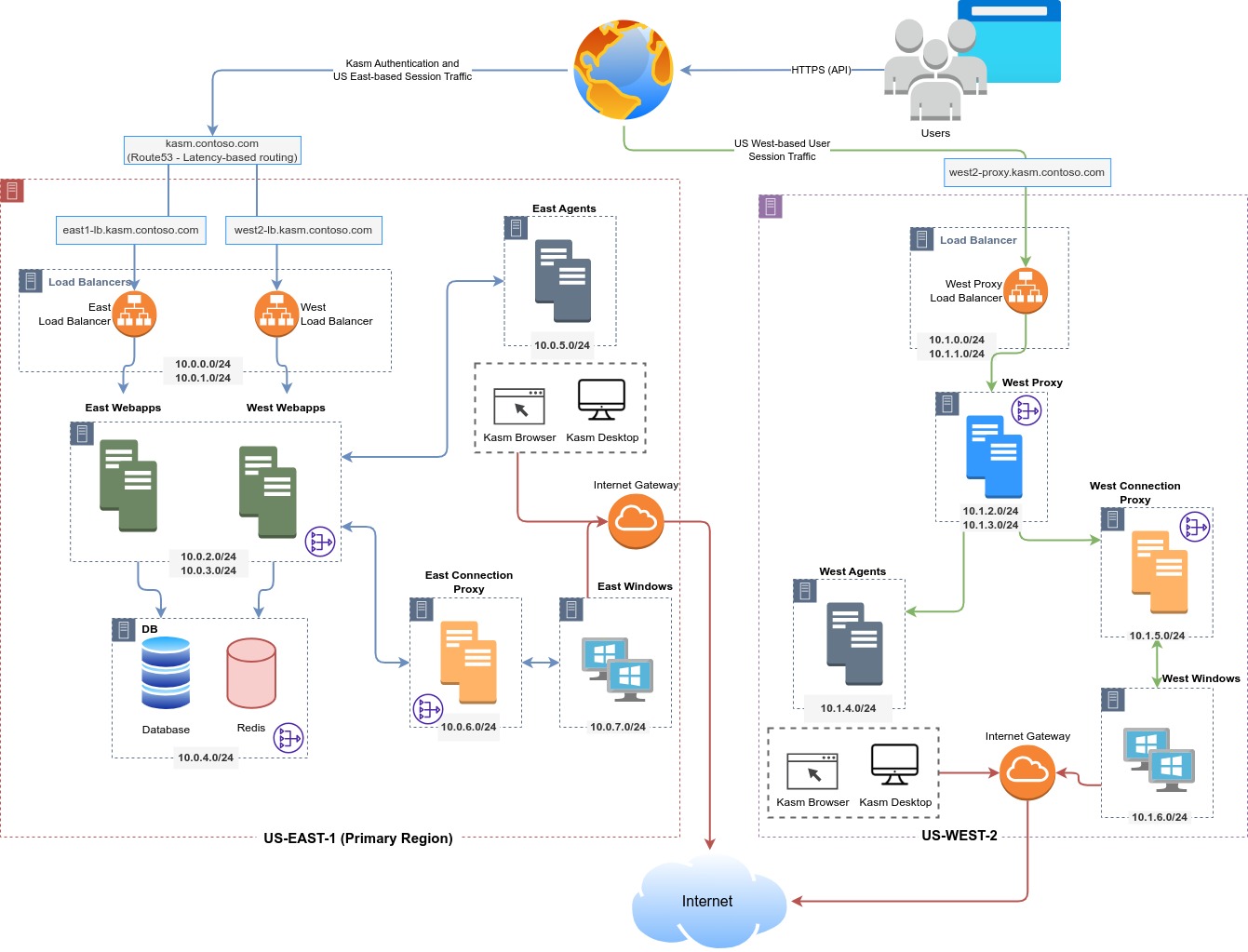
This project will deploy Kasm Workspaces within multiple AWS regions of your choice. Multiple Deployment Zones will be configured for the deployment that correspond to the desired AWS regions.
All webapp roles will be deployed in a single "Primary" region, with Agent roles deployed in any additional region(s).
Route53 latency policies are used to automatically connect users to webapp servers that represent their closest Zone/Region so that session gets created in the user's closest region by default.
It is expected that administrators will configure the Direct to Agent workflow post deployment so that session traffic does not always traverse the Primary Region and instead flows directly to the Agent in whichever region it is deployed.
Consider creating a special sub account for the Kasm deployment.
In your AWS account create a DNS Public zone that matches the desired domain name for the deployment. e.g kasm.contoso.com
In the each AWS region where you will deploy Kasm, create an aws Key pair with the same name. The key name will be value used in the aws_key_pair variable and it will be configured as the SSH key for the deployed EC2 machines.
Create a user via the IAM console that will be used for the terraform deployment. Give the user Programatic Access and attach the existing policy AdministratorAccess. Save the key and key secret.
-
Initialize the project
terraform init
-
Open
terraform.tfvarsand update the variable values. The variable definitions, descriptions, and validation expectations can be found in thevariables.tffile.
NOTE: This document assumes you are using a separate file named
secrets.tfvarsfor the AWS credentials generated in the AWS API Keys section above. The .gitignore file in this repository will ignore any files namedsecrets.tfvarssince they are expected to have sensitive values in them. This will prevent you from accidentally committing them to source control. If you would rather use Environment variables or some other AWS credential method in lieu of thesecrets.tfvarsfile, check out the AWS Terraform provider documentation for more information about configuring your environment.
-
If you are deploying more than 2 regions, you will need to modify the
provider.tf,deployment.tf, andoutputs.tffiles. There are commented sections in both files indicating how to deploy additional regions. -
Verify the configuration
terraform plan -var-file secrets.tfvars
-
Deploy
terraform apply -var-file secrets.tfvars
-
Login to the Deployment as an Admin via the domain defined; e.g.,
https://kasm.contoso.com -
Navigate to the
Infrastructure > Zonessection and update the following values according to output values from this deployment.- Upstream Auth Address
- Proxy Hostname
-
Navigate to the
Infrastructure > Agentssection and enable each Agent after it checks in. (May take a few minutes) -
Now you are ready to add Workspaces via the registry and start using Kasm!
| Name | Version |
|---|---|
| terraform | ~> 1.0 |
| aws | ~> 5.0 |
No providers.
| Name | Source | Version |
|---|---|---|
| primary_region | ./primary | n/a |
| primary_region_webapps_and_agents | ./webapps | n/a |
| region2_agents | ./agents | n/a |
| region2_webapps | ./webapps | n/a |
No resources.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| admin_password | The administrative user password. No special characters | string |
n/a | yes |
| agent_hdd_size_gb | The HDD size in GB to configure for the Kasm Agent instances | number |
n/a | yes |
| agent_instance_type | The instance type for the Agents | string |
n/a | yes |
| aws_access_key | The AWS access key used for deployment | string |
n/a | yes |
| aws_default_tags | Default tags to apply to all AWS resources for this deployment | map(any) |
{ |
no |
| aws_domain_name | The Route53 Zone used for the dns entries. This must already exist in the AWS account. (e.g dev.kasm.contoso.com). The deployment will be accessed via this zone name via https | string |
n/a | yes |
| aws_key_pair | The name of an aws keypair to use. | string |
n/a | yes |
| aws_primary_region | The AWS Region used for deployment | string |
"us-east-1" |
no |
| aws_secret_key | The AWS secret key used for deployment | string |
n/a | yes |
| aws_ssm_iam_role_name | The name of the SSM EC2 role to associate with Kasm VMs for SSH access | string |
"" |
no |
| aws_ssm_instance_profile_name | The name of the SSM EC2 Instance Profile to associate with Kasm VMs for SSH access | string |
"" |
no |
| cpx_hdd_size_gb | The HDD size in GB to configure for the Kasm Guac RDP instances | number |
n/a | yes |
| cpx_instance_type | The instance type for the Guac RDP nodes | string |
n/a | yes |
| create_aws_ssm_iam_role | Create an AWS SSM IAM role to attach to VMs for SSH/console access to VMs. | bool |
false |
no |
| database_password | The password for the database. No special characters | string |
n/a | yes |
| db_hdd_size_gb | The HDD size in GB to configure for the Kasm Database instances | number |
n/a | yes |
| db_instance_type | The instance type for the Database | string |
n/a | yes |
| kasm_build | Download URL for Kasm Workspaces | string |
n/a | yes |
| manager_token | The manager token value for Agents to authenticate to webapps. No special characters | string |
n/a | yes |
| num_agents | The number of Agent Role Servers to create in the deployment | number |
2 |
no |
| num_cpx_nodes | The number of RDP Conection Proxy Role Servers to create in the deployment. Set this to zero (0) and this Terraform will not deploy ANY Connection Proxy or Windows resoures like subnets, security groups, etc. | number |
n/a | yes |
| num_proxy_nodes | The number of Dedicated Proxy nodes to create in the deployment | number |
n/a | yes |
| num_webapps | The number of WebApp role servers to create in the deployment | number |
2 |
no |
| primary_region_ec2_ami_id | AMI Id of Kasm EC2 image in the primary region. Recommended AMI OS Version is Ubuntu 20.04 LTS. | string |
n/a | yes |
| primary_vpc_subnet_cidr | The subnet CIDR to use for the VPC | string |
"10.0.0.0/16" |
no |
| project_name | The name of the deployment (e.g dev, staging). A short single word | string |
n/a | yes |
| proxy_hdd_size_gb | The HDD size in GB to configure for the Kasm dedicated proxy instances | number |
n/a | yes |
| proxy_instance_type | The instance type for the dedicated proxy node | string |
"" |
no |
| redis_password | The password for the Redis server. No special characters | string |
n/a | yes |
| secondary_regions_settings | Map of Kasm settings for secondary regions | map(object({ |
n/a | yes |
| service_registration_token | The service registration token value for cpx RDP servers to authenticate to webapps. No special characters | string |
n/a | yes |
| ssh_access_cidrs | CIDR notation of the bastion host allowed to SSH in to the machines | list(string) |
[ |
no |
| swap_size | The amount of swap (in MB) to configure inside the compute instances | number |
n/a | yes |
| user_password | The standard (non administrator) user password. No special characters | string |
n/a | yes |
| web_access_cidrs | CIDR notation of the bastion host allowed to SSH in to the machines | list(string) |
[ |
no |
| webapp_hdd_size_gb | The HDD size in GB to configure for the Kasm WebApp instances | number |
n/a | yes |
| webapp_instance_type | The instance type for the webapps | string |
"" |
no |
| Name | Description |
|---|---|
| region1_zone_settings | Upstream Auth and Proxy settings to apply to Kasm Primary Region Zone configuration |
| region2_zone_settings | Upstream Auth and Proxy settings to apply to Kasm Agent Region 2 Zone configuration |