| copyright | lastupdated | keywords | subcollection | ||
|---|---|---|---|---|---|
|
2019-07-19 |
kubernetes, iks |
containers |
{:new_window: target="_blank"} {:shortdesc: .shortdesc} {:screen: .screen} {:pre: .pre} {:table: .aria-labeledby="caption"} {:codeblock: .codeblock} {:tip: .tip} {:note: .note} {:important: .important} {:deprecated: .deprecated} {:download: .download} {:preview: .preview}
{: #tutorials-ov}
<style> </style>{: #tutorials-create-cluster-deploy-app}
Create a Kubernetes cluster on managed {{site.data.keyword.containerlong_notm}} with Classic infrastructure worker nodes that run an Ubuntu operating system.

Create a classic cluster in your Virtual Private Cloud (VPC).

Create an {{site.data.keyword.containerlong_notm}} cluster with worker nodes that come installed with the OpenShift container orchestration platform software.

{: #tutorials-deploy-app}
Scaffold a web app, deploy it to a cluster, and learn how to scale your app and monitor its health.

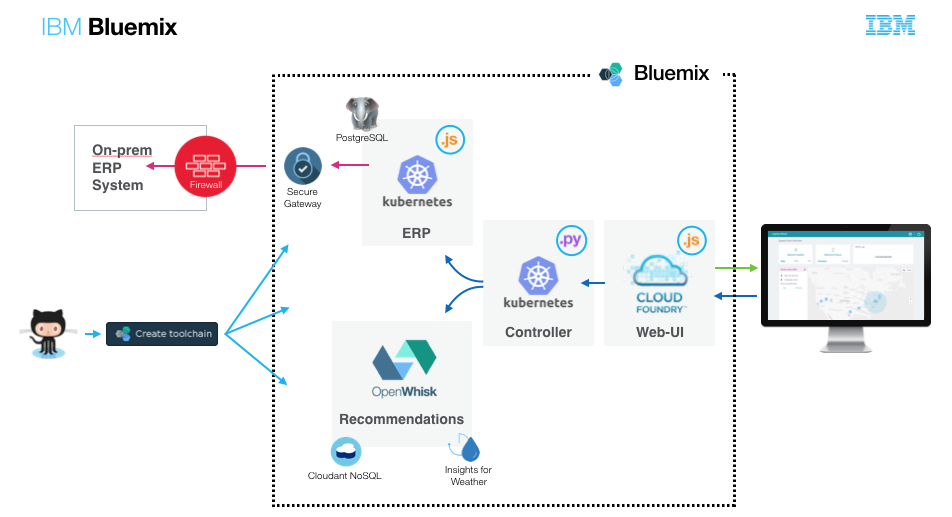
Create a Logistics Wizard deployment where the ERP and Controller services are deployed in Kubernetes, and the web user interface stays deployed as a Cloud Foundry app.
Use an Apache Kafka-based messaging service to orchestrate long running workloads to apps that run in a Kubernetes cluster.

Create a containerized app from an {{site.data.keyword.cloud_notm}} starter kit and deploy your app by using a DevOps toolchain.

{: #tutorials-ov-ha-network-security}
Integrate Cloud Internet Services with Kubernetes clusters to deliver a resilient and secure solution across multiple {{site.data.keyword.cloud_notm}} regions.

Learn what to consider when creating resilient apps in the cloud and what {{site.data.keyword.cloud_notm}} services you can use.

Learn how to use Calico policies to whitelist or blacklist network traffic from and to certain IP addresses.

Explore the intelligent routing and monitoring capability of Istio to control and secure your microservices in the cloud.

Learn how to use authentication and encryption to protect your app, and how to monitor and audit cluster activities.

Set up cluster access for users and teams and learn how to replicate this setup across environments.

{: #tutorials-ov-app-cluster-deployments}
Create modern, source-centric, containerized, and serverless apps on top of your Kubernetes cluster.

Set up a DevOps pipeline for containerized apps that run in Kubernetes and add integrations such as security scanner, Slack notifications, and analytics.

Automate, manage, and visualize the deployment of Kubernetes resources across clusters, environments, and cloud providers with Razee.

{: #tutorials-ov-monitor-log}
Configure a logging agent in your cluster and monitor different log sources with {{site.data.keyword.la_full_notm}}.

Set up a Sysdig metrics agent in your cluster and explore how you can monitor your cluster's health.

{: #tutorials-ov-migrate-apps}
Learn how to create a Docker image from a Python Cloud Foundry app, push this image to {{site.data.keyword.registryshort_notm}}, and deploy your app to a Kubernetes cluster.

Prepare your app code, containerize your VM-based app, and deploy this app to a Kubernetes cluster.

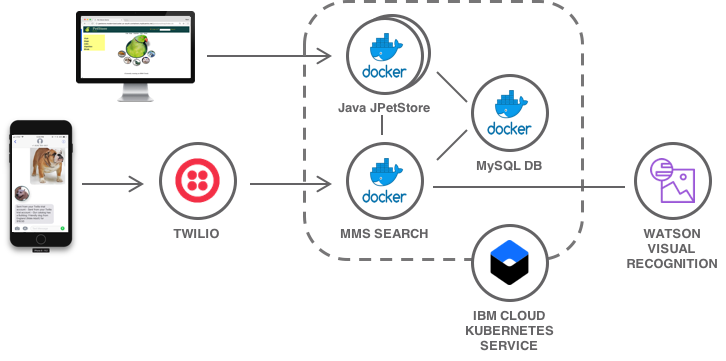
Containerize the JPetStore app and extend it with Watson Visual Recognition and Twilio text messaging.