[Draft] Trust Policy and Trust Store Configuration #98
Replies: 9 comments 10 replies
-
This goes back to the artifact and location of the artifact are decoupled. Can we tie this back to the root of trust conversation?
There was a break-glass scenario, where a deployer can choose to continue using an artifact that has been revoked as the revocation/denial of the artifact being used can be more destructive to a users environment. This is a choice of the deployer, so it is an explicit choice.
If we're going to limit a scope to a registry, we should limit to a registry/namespace as different registries are shared across companies (docker hub) while multiple teams may share a common company registry |
Beta Was this translation helpful? Give feedback.
-
No, consider public registries like |
Beta Was this translation helpful? Give feedback.
-
|
If these files are at all expected to be human-written, the field names feel rather unergonomic — |
Beta Was this translation helpful? Give feedback.
-
|
I don’t think the separation of |
Beta Was this translation helpful? Give feedback.
-
That’s going to create ambiguities and hard-to-reason behavior ( |
Beta Was this translation helpful? Give feedback.
-
|
For gradual deployment, it is very necessary to allow partial signature enforcement — e.g. enforce signatures on my registry, but impose no requirements at all on |
Beta Was this translation helpful? Give feedback.
-
|
I wonder if we can split the necessary parts (ie you must validate signatures correctly) from more generic policy choices and allow those to be determined by a more generic policy engine (eg OPA)? |
Beta Was this translation helpful? Give feedback.
-
|
I posted my version over at #100. The big changes I'm suggesting:
I've added a few more questions in mine, mostly around the developer experience:
Note that I see a lot of this as lower priority. If the signing and server side is working, different vendors can make different Notation clients that handle all of these use cases and more. Having a Notation client that becomes the reference implementation that many can use without forking would be a nice to have. |
Beta Was this translation helpful? Give feedback.
-
|
For the signature evaluation process, we should verify the signing identity first and then the actual artifact signature. |
Beta Was this translation helpful? Give feedback.
-
Out of scope
Requirements
Trust Store Requirements
Deployer who consumes and executes the signed artifact from a registry needs a mechanism to specify the trusted producers. This is where deployer will use Trust Store.
Trust Policy Requirements
Deployer who consumes and executes the signed artifact from a registry needs a mechanism to specify how the artifacts should be evaluated for trust. This is where deployer will use Trust Policy.
Design
Trust Store
trustStore: Parent node containing trust store information.identities: The identities that deployer trusts.x5c: The PEM representation of signing certificate.tsaX5c: The PEM representation of timestamp certificate.key: The Base64 encoded verification key.keyId: The ASCII representation of keyId.scope: Adding this field as sibling ofidentities, scopes down the identities that would be trusted for the artifact matching the scope. Scope supports wildcard(*).trustStorecan have overlappingscope.trustStorewithoutscopenode.Evaluation
scope, then only the identities associated with scope are trusted for that artifact. e.g., Forwabbit-networks2.ioregistry onlyrootCertificate3is trusted.scope, then the identities without anyscopenode are trusted for that artifact. e.g., Forwabbit-networks999.ioregistry onlyrootCertificate5, rootCertificate5, exampleKey1...are trusted.Trust Policy
Compact mode
Artifact Integrity Validation
trustPolicy.Artifact Expiry Validation
Revoked Artifact Validation
Since revocation requires network call, the trustPolicy should provide option to either fail-open or fail-close in case the revocation URLs are not reachable.
trueWithFailOpenmode and revocation URL is unreachable, the system continues to allow the artifact.trueWithFailClosemode and revocation URL is unreachable, the system MUST rejects the artifact.Extensibility
TBD
Evaluation
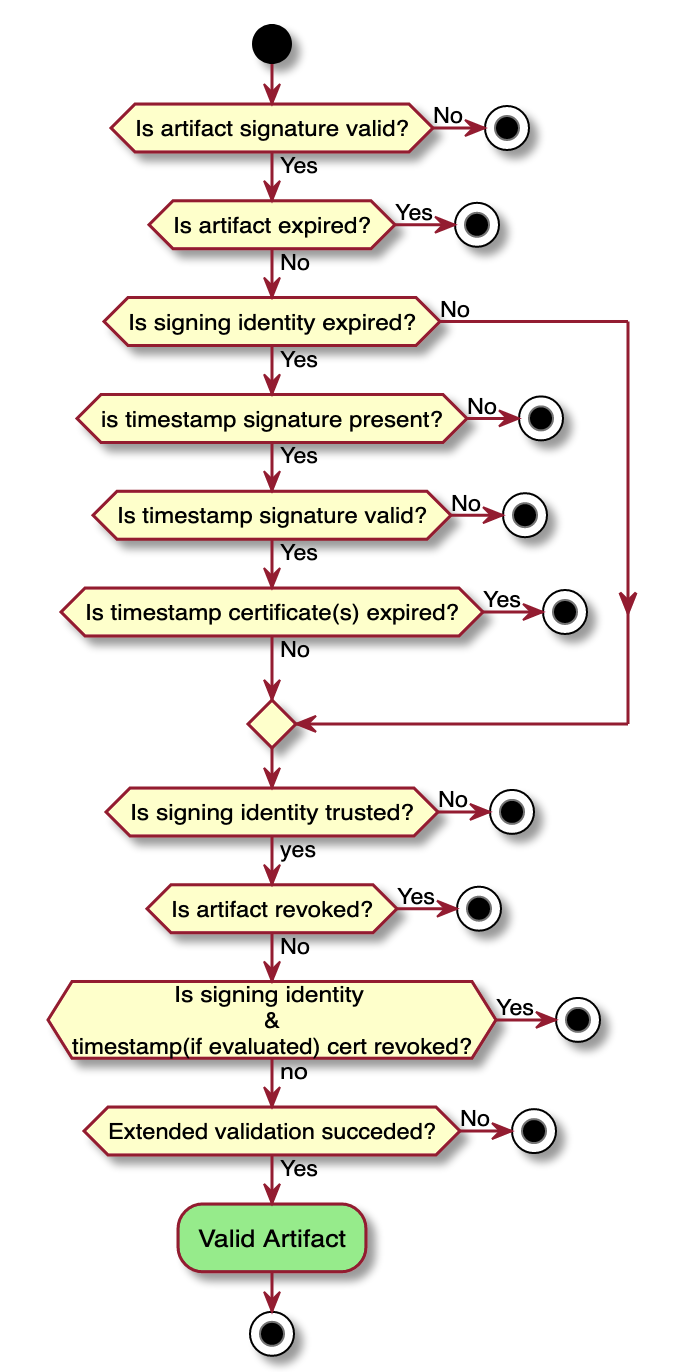
* Revocation calls SHOULD be non-blocking.Signature evaluation steps(in-progress)
Open Questions
scopewe should support? Isregistrysufficient?Glossary
HackMD Doc: https://hackmd.io/s2mrFDOLQuWrV8Ib7ad7Ag
Beta Was this translation helpful? Give feedback.
All reactions