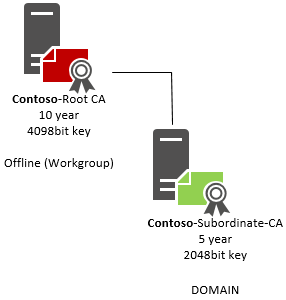
This my take on a simple yet powerful Active Directory Certificate Services (ADCS) implementation. The two PowerShell scripts provides an easy and documented process to install, configure and setup a complete two-tier PKI environment.
Root/Offline CA Configuration:
| Item | Value (Can be modified) |
|---|---|
| Customer | Contoso |
| Operating system | 2012 / 2012R2 / 2016 |
| CA Type | Standalone Root |
| CA Name | Contoso-ROOT-CA |
| Validity Period | 10 years |
| CSP | RSA #Microsoft Software Key Storage Provider |
| Hash Algorithm | SHA256 |
| Key Length | 4096 |
| Database Location | C:\PKI\Database\CertDB |
| Database Log Location | C:\PKI\Database\CertLog |
| CRL Validity Period | 1 year (No delta) |
| CDP | Only HTTP - pki.contoso.com |
| CAPolicy.inf | Automatically generated |
Enterprise/Subordinate CA Configuration:
| Item | Value (Can be modified) |
|---|---|
| Customer | Contoso |
| Operating system | 2012 / 2012R2 / 2016 |
| CA Type | Enterprise Subordinate |
| CA Name | Contoso-Subordinate-CA |
| Validity Period | 5 years |
| CSP | RSA #Microsoft Software Key Storage Provider |
| Hash Algorithm | SHA256 |
| Key Length | 2048 |
| Database Location | C:\PKI\Database\CertDB |
| Database Log Location | C:\PKI\Database\CertLog |
| CRL Validity Period | 7 days (No delta) |
| CDP | Only HTTP - pki.contoso.com |
| CAPolicy.inf | Automatically generated |
- An Active Directory Directory Service
- A Windows 2012/2012R2/2016 Server* (PowerShell 4.0) used for Root/Offline CA
- A Windows 2012/2012R2/2016 Server* (PowerShell 4.0) used for Enterprise/Subordinate CA
- Domain Administrator membership or similar privileges for installation.
- Local Administrator privileges (PowerShell.exe Runas Administrator).
*Servers can be hosted in a virtual environment.
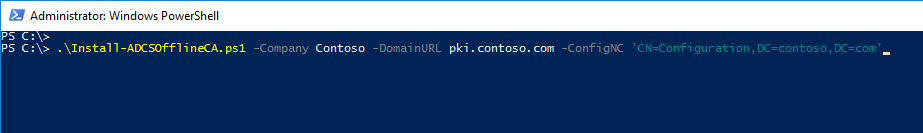
- Company: Used to populate the and AIA/CRL and CA Common names.
- DomainURL: Used for CDP and AIA publishing.
- ConfigNC: Used for publishing Root CA in the Active Directory.
-
Confirm the installation when/if prompted. The installation of the Root/Offline CA Role is now done.

-
Run "Install-ADCSSubordinateCA.ps1" on the server dedicated for the Enterprise/Subordinate CA Role.
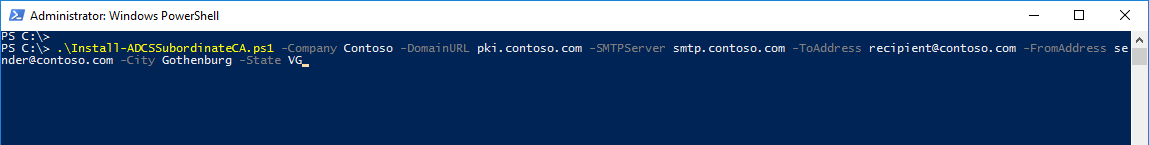
- SMTPServer: Mail server used to send the PKI maintenance/job reminder.
- ToAddress: Recipient address for the PKI maintenance/job reminder.
- FromAddress: Sender address for the PKI maintenance/job reminder.
- City: Used to populate the ADCS Web Enrollment information template.
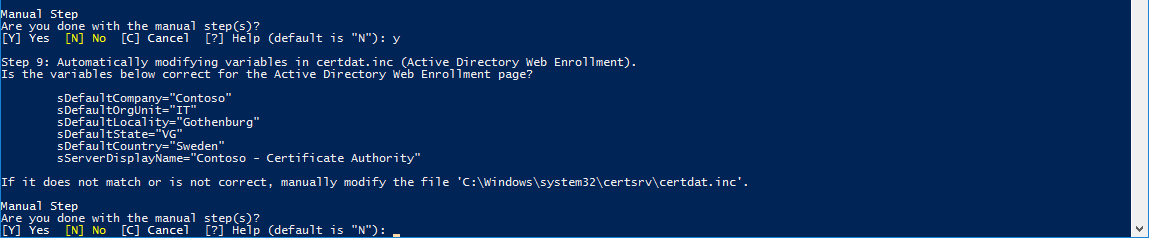
- State: Used to populate the ADCS Web Enrollment information template. *Country is not available as a parameter as of now, default is Sweden. * *ADCS Web Enrollment Template can easily be modified in the $env:WinDir\System32\certsrv\certdat.inc file. *
- Each next setup provides a prompt that encourages a manual routine / process.
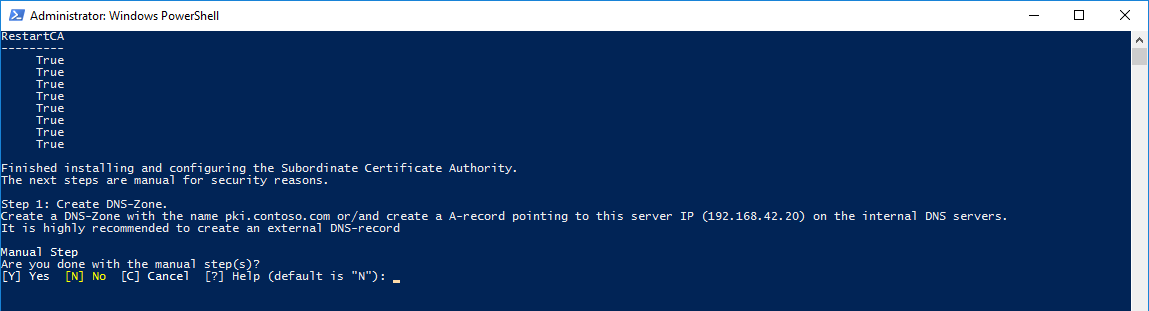
4.1. Create an Internal DNS-Zone and/or an A-record pointed to the Enterprise Subordinate CA server.
It's highly recommended to create an external publishing for the $DomainURL so the CDP is reachable from the outside.
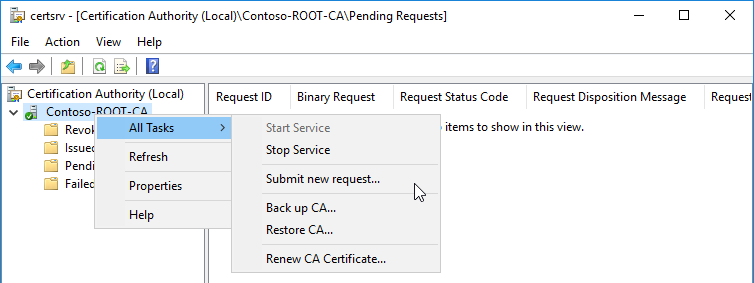
4.2 Sign/Issue the Enterprise/Subordinate CA Certificate on the Root/Offline CA server.
*It's recommended to not have a network connection on the Root/Offline CA Server when running in production. *

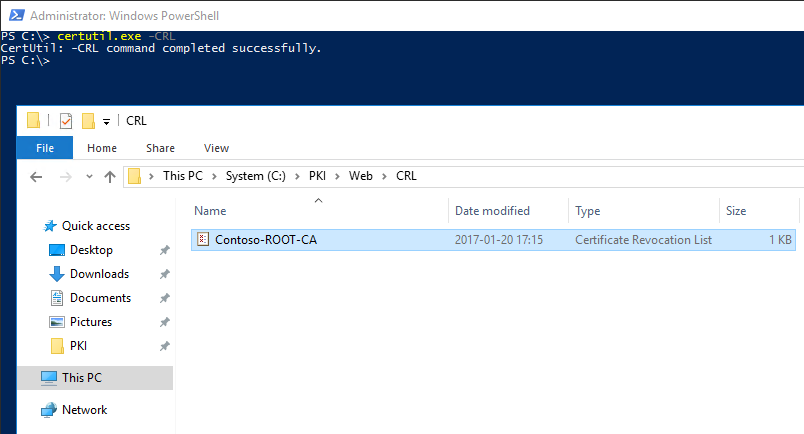
4.3 Publish a new CRL on the Root/Offline CA server.

4.4. Rename the Root/Offline CA Certificate to match the AIA location.
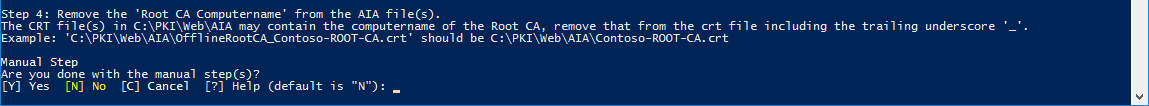
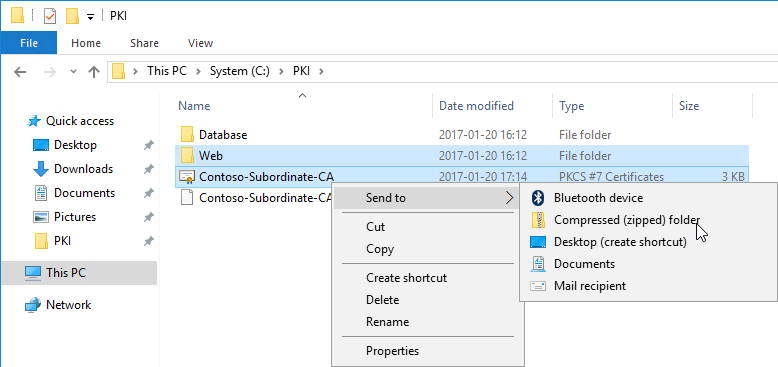
4.5. Copy the CRL and CRT files from the Root/Offline CA server to the Enterprise/Subordinate server.
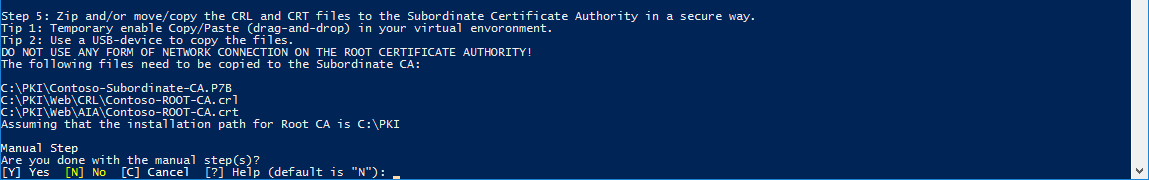
Example:
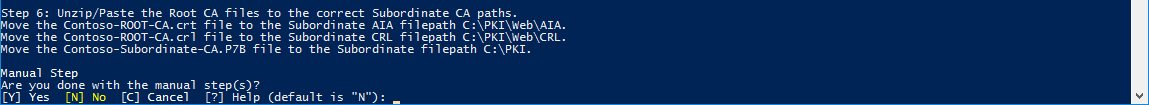
4.6. Unzip / Move the copied CRL and CRT files (Step 4.5) to the correct paths on the Enterprise/Subordinate CA Server.
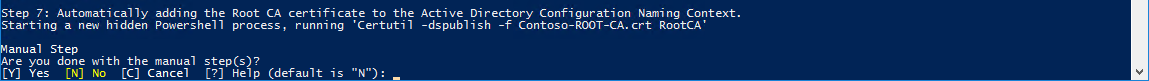
4.7 Automatically trying to add the Root/Offline CA certificate to the Active Directory Configuration.
View in adsiedit.msc after Step 7 (4.6).
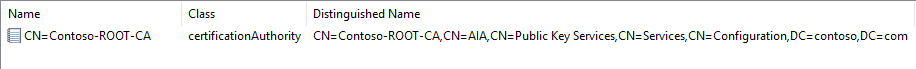
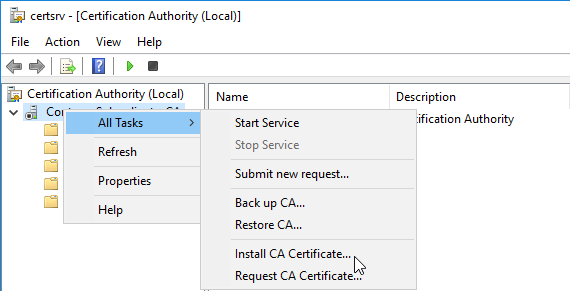
4.8. Install the Enterprise/Subordinate Certificate.
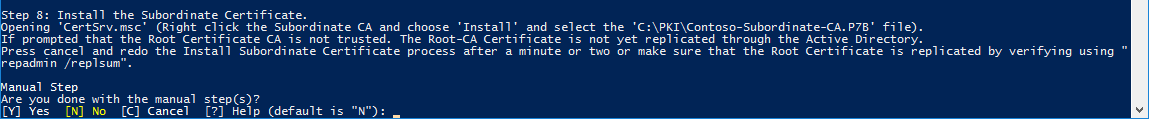
Example:
4.9. Automatically modifying "certdat.inc" file to match the Company information.
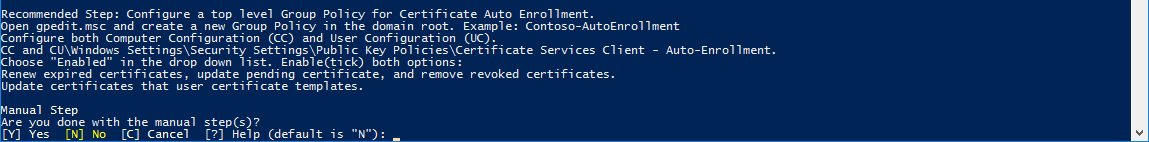
4.10. Create a Group Policy for Certificate Auto Enrollment (Only recommended).
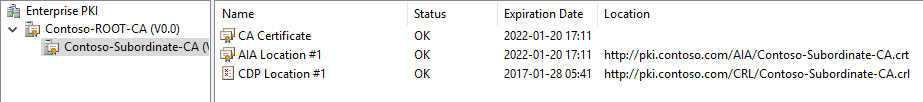
Verify the setup in pkiview.msc.
> For a more detailed installation check the [Wiki section.](https://github.com/PhilipHaglund/ADCS/wiki/Detailed-Installation-instructions)