Summary
Cross site scripting (XSS) potentially exposing cookies / sessions / localStorage, fixed by sidekiq-unique-jobs v8.0.7.
Specifically, this is a Reflected (Server-Side), Non-Self, Cross Site Scripting vulnerability, considered a P3 on the BugCrowd taxonomy with the following categorization:
Cross-Site Scripting (XSS) > Reflected > Non-Self
It was initially thought there was a second vulnerability (RCE), but it was a false alarm. Injection is impossible with Redis:
String escaping and NoSQL injection
The Redis protocol has no concept of string escaping, so injection is impossible under normal circumstances using a normal client library. The protocol uses prefixed-length strings and is completely binary safe.
Ref: https://redis.io/docs/management/security/
XSS Vulnerability
Specially crafted GET request parameters handled by any of the following endpoints of sidekiq-unique-jobs' "admin" web UI, allow a super-user attacker, or an unwitting, but authorized, victim, who has received a disguised / crafted link, to successfully execute malicious code, which could potentially steal cookies, session data, or local storage data from the app the sidekiq-unique-jobs web UI is mounted in.
/changelogs/locks/expiring_locks
This means if your sidekiq-unique-jobs web UI is mounted at /sidekiq, the vulnerable paths are:
/sidekiq/changelogs/sidekiq/locks/sidekiq/expiring_locks
XSS vulnerability is an instance of CAPEC-32: XSS Through HTTP Query Strings, which is related to CWE-80. In certain cases where it results in a server error with status 500, it could be considered a vector for uncontrolled resource consumption, given that errors can be much more resource intensive that normal requests, and thus CWE-400 & CWE-754 may also be relevant.
Details
Fix for the XSS vulnerability was released in sidekiq-unique-jobs v8.0.7.
This is an analogous attack vector to that which affected sidekiq gem from version v7.0.4 to v7.0.7, and was given identifiers GHSA-h3r8-h5qw-4r35 & CVE-2023-1892.
The vulnerability in sidekiq-unique-jobs' was not fixed by sidekiq v7.0.8, nor the more recent sidekiq v7.2.0 releases; they are similar but unrelated, distinct vulnerabilities in adjacent projects.
Note #1: The admin web UI for sidekiq-unique-jobs is not protected by any authorization constraint in the default configuration. Auth constraints must be configured by the programmer. It is recommended and expected that users will configure authorization constrains on the "admin" UI. This is not specifically related to the vulnerability but may make users who fail to constrain their "admin" UI even more vulnerable.
Note #2: Most users of the library will not have configured the UI on a sandboxed subdomain, making all their cookies, localStorage data and session secrets vulnerable to exposure. The purpose of a sandboxed subdomain is expressly to prevent leaking sensitive data through XSS attacks.
XSS Fix PR: mhenrixon/sidekiq-unique-jobs#829
PoC
XSS
Use a string like:
%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
as the value for one of the parameters that are handled without escaping.
Reference: https://liveoverflow.com/do-not-use-alert-1-in-xss/
- Visit /sidekiq/changelogs - with a crafted query string like one of the following:
a. Screenshot: 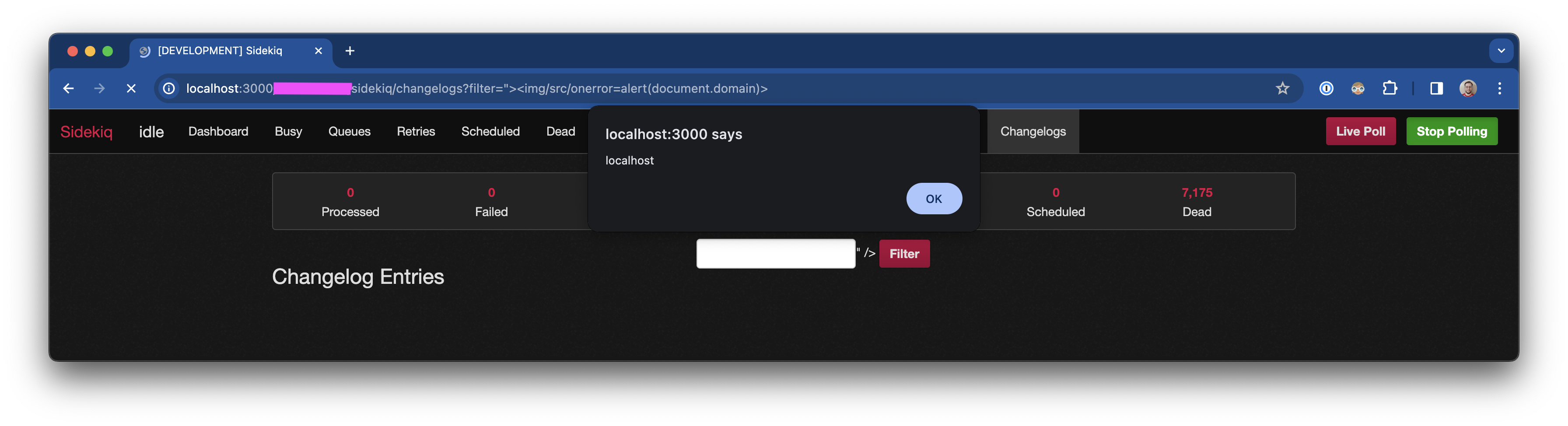
b. filter is XSS vulnerable: ?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
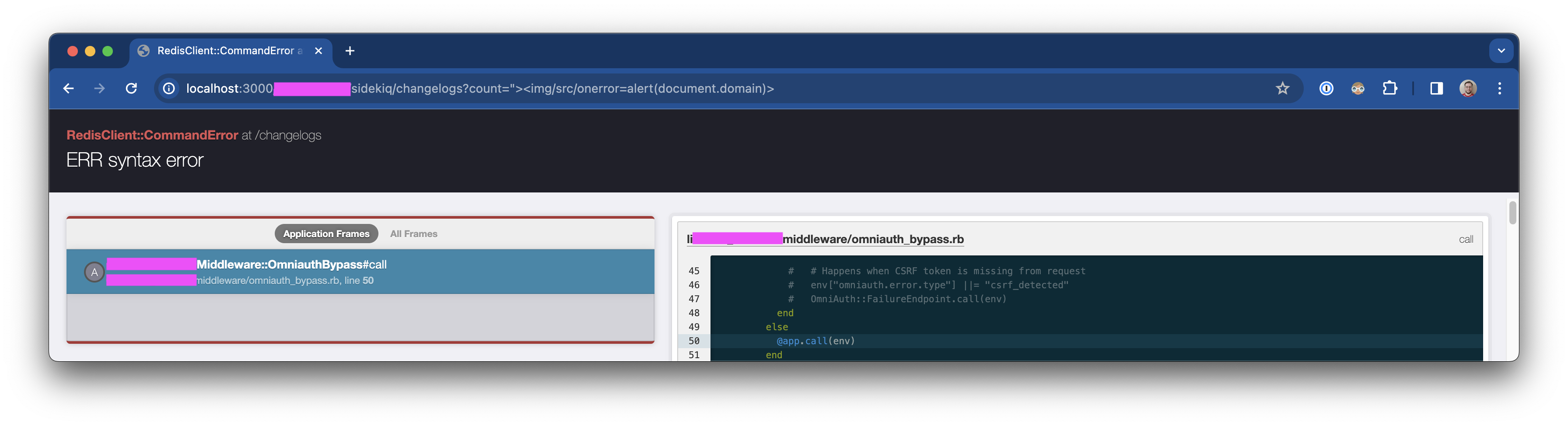
c. count is vulnerable to triggering an application error (status 500), potentially allowing resource exhaustion ?count=%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
- Screenshot:
- Visit /sidekiq/locks - with a crafted query string like one of the following:
a. Screenshot: 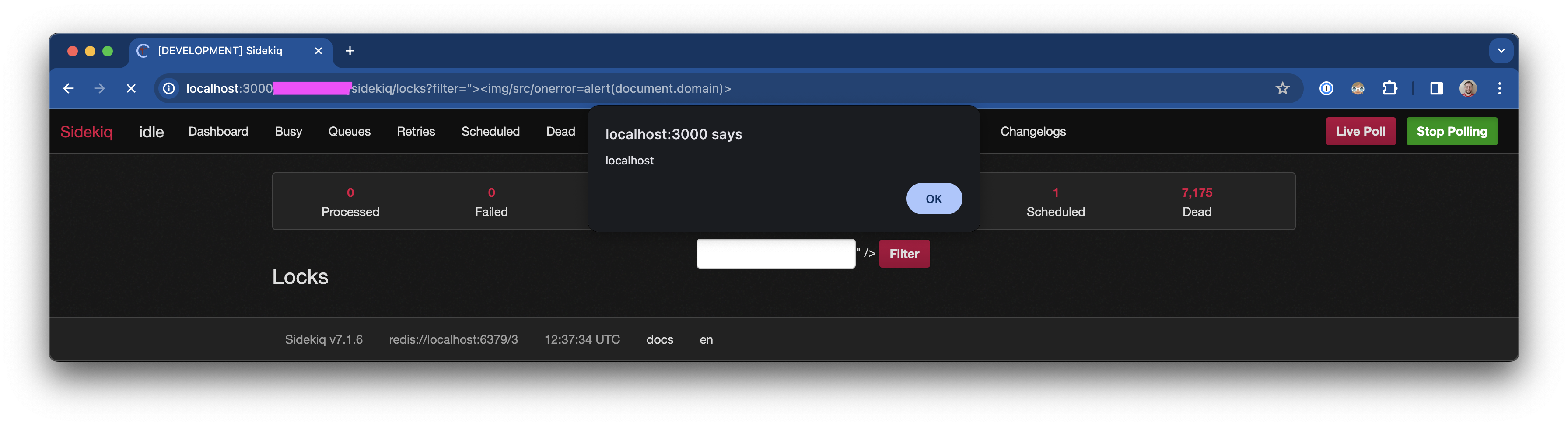
b. filter is XSS vulnerable: ?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
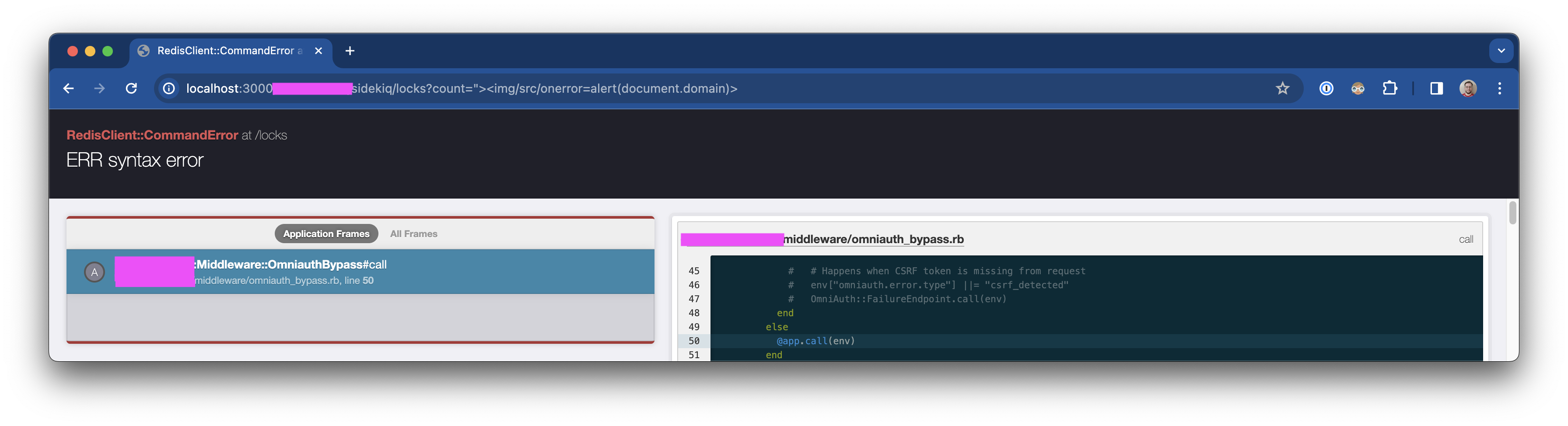
c. count is vulnerable to triggering an application error (status 500), potentially allowing resource exhaustion ?count=%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
- Screenshot:
- Visit /sidekiq/expiring_locks - with a crafted query string like one of the following:
a. Screenshot: 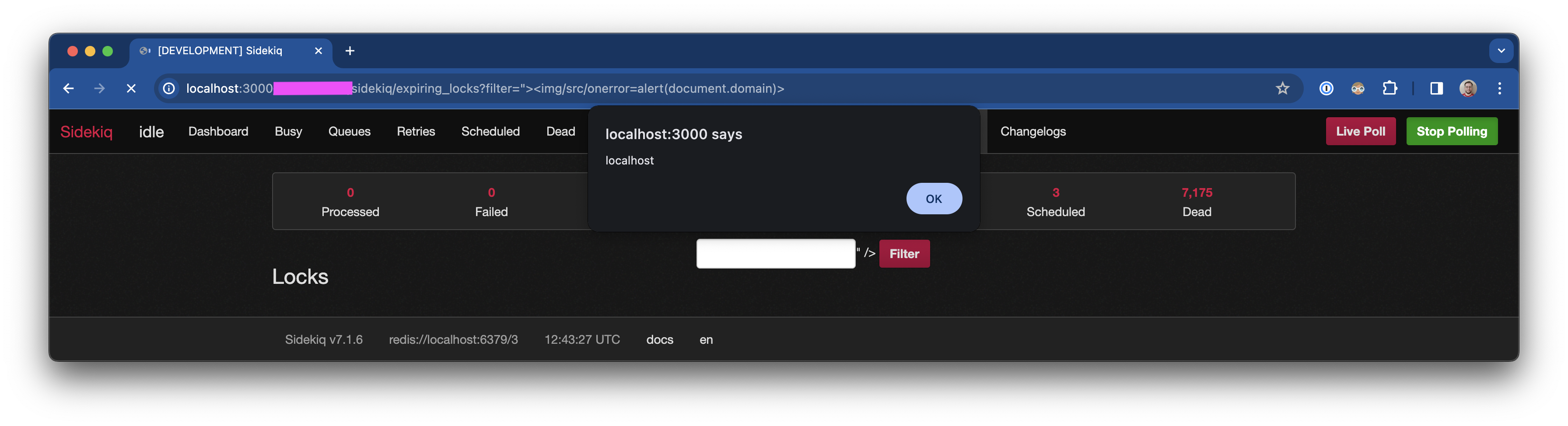
b. filter is XSS vulnerable: ?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3E
Impact
This is a vulnerability of critical severity, which impacts many thousands of sites, since sidekiq-unique-jobs is widely deployed across the industry, with multiple attack vectors.
References
Summary
Cross site scripting (XSS) potentially exposing cookies / sessions / localStorage, fixed by
sidekiq-unique-jobsv8.0.7.Specifically, this is a Reflected (Server-Side), Non-Self, Cross Site Scripting vulnerability, considered a P3 on the BugCrowd taxonomy with the following categorization:
Cross-Site Scripting (XSS) > Reflected > Non-Self
It was initially thought there was a second vulnerability (RCE), but it was a false alarm. Injection is impossible with Redis:
Ref: https://redis.io/docs/management/security/
XSS Vulnerability
Specially crafted
GETrequest parameters handled by any of the following endpoints ofsidekiq-unique-jobs' "admin" web UI, allow a super-user attacker, or an unwitting, but authorized, victim, who has received a disguised / crafted link, to successfully execute malicious code, which could potentially steal cookies, session data, or local storage data from the app thesidekiq-unique-jobsweb UI is mounted in./changelogs/locks/expiring_locksThis means if your
sidekiq-unique-jobsweb UI is mounted at/sidekiq, the vulnerable paths are:/sidekiq/changelogs/sidekiq/locks/sidekiq/expiring_locksXSS vulnerability is an instance of CAPEC-32: XSS Through HTTP Query Strings, which is related to CWE-80. In certain cases where it results in a server error with status 500, it could be considered a vector for uncontrolled resource consumption, given that errors can be much more resource intensive that normal requests, and thus CWE-400 & CWE-754 may also be relevant.
Details
Fix for the XSS vulnerability was released in
sidekiq-unique-jobsv8.0.7.This is an analogous attack vector to that which affected
sidekiqgem from version v7.0.4 to v7.0.7, and was given identifiers GHSA-h3r8-h5qw-4r35 & CVE-2023-1892.The vulnerability in
sidekiq-unique-jobs' was not fixed bysidekiqv7.0.8, nor the more recentsidekiqv7.2.0 releases; they are similar but unrelated, distinct vulnerabilities in adjacent projects.Note #1: The admin web UI for
sidekiq-unique-jobsis not protected by any authorization constraint in the default configuration. Auth constraints must be configured by the programmer. It is recommended and expected that users will configure authorization constrains on the "admin" UI. This is not specifically related to the vulnerability but may make users who fail to constrain their "admin" UI even more vulnerable.Note #2: Most users of the library will not have configured the UI on a sandboxed subdomain, making all their cookies, localStorage data and session secrets vulnerable to exposure. The purpose of a sandboxed subdomain is expressly to prevent leaking sensitive data through XSS attacks.
XSS Fix PR: mhenrixon/sidekiq-unique-jobs#829
PoC
XSS
Use a string like:
as the value for one of the parameters that are handled without escaping.
Reference: https://liveoverflow.com/do-not-use-alert-1-in-xss/
a. Screenshot:
b.
filteris XSS vulnerable:?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3Ec.
countis vulnerable to triggering an application error (status 500), potentially allowing resource exhaustion?count=%22%3E%3Cimg/src/onerror=alert(document.domain)%3Ea. Screenshot:
b.
filteris XSS vulnerable:?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3Ec.
countis vulnerable to triggering an application error (status 500), potentially allowing resource exhaustion?count=%22%3E%3Cimg/src/onerror=alert(document.domain)%3Ea. Screenshot:
b.
filteris XSS vulnerable:?filter=%22%3E%3Cimg/src/onerror=alert(document.domain)%3EImpact
This is a vulnerability of critical severity, which impacts many thousands of sites, since
sidekiq-unique-jobsis widely deployed across the industry, with multiple attack vectors.References