-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
8 changed files
with
114 additions
and
35 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,57 @@ | ||
| --- | ||
| layout: post | ||
| categories: original | ||
| title: "记录阿里云OSS第一次受到流量攻击" | ||
| author: 立泉 | ||
| mention: 博客 对象存储 | ||
| date: 2024-11-25 +0800 | ||
| description: 昨天中午突然收到阿里云的报警短信,意识到预想中的情况发生了,拿出手机打开博客果然无法访问。倒是长舒一口气,看来提前配置的监控策略已经成功关闭OSS对外服务。 | ||
| cover: | ||
| tags: Code Blog 云计算 阿里云 OSS 对象存储 函数计算 网络攻击 | ||
| --- | ||
|
|
||
| 自今年3月起静态博客开始托管在阿里云的`OSS`对象存储上,香港节点无需`ICP备案`而且速度尚可,从大陆访问比`GitHub Pages`稳定很多。主站因为备案要求不能放在大陆,字体、图片之类的资源文件不使用自定义域名则无此限制,所以为提升国内访问速度都被托管在阿里云杭州节点的`OSS`上。 | ||
|
|
||
| `OSS`的流量费用并不廉价,为规避可能的账单风险提前[用云监控设置过访问规则]({% link _posts/original/2024-03-07-解决阿里云OSS无CDN时的流量风险.md %}){: target="_blank" },当每分钟流量超过200MB时触发报警,自动调用`函数计算`关闭`OSS`对外服务。我这样的小站点,监控用量、临时关站是应对低成本流量攻击最适合的策略。 | ||
|
|
||
| ## 报警 | ||
|
|
||
| 昨天中午突然收到阿里云的报警短信: | ||
|
|
||
| 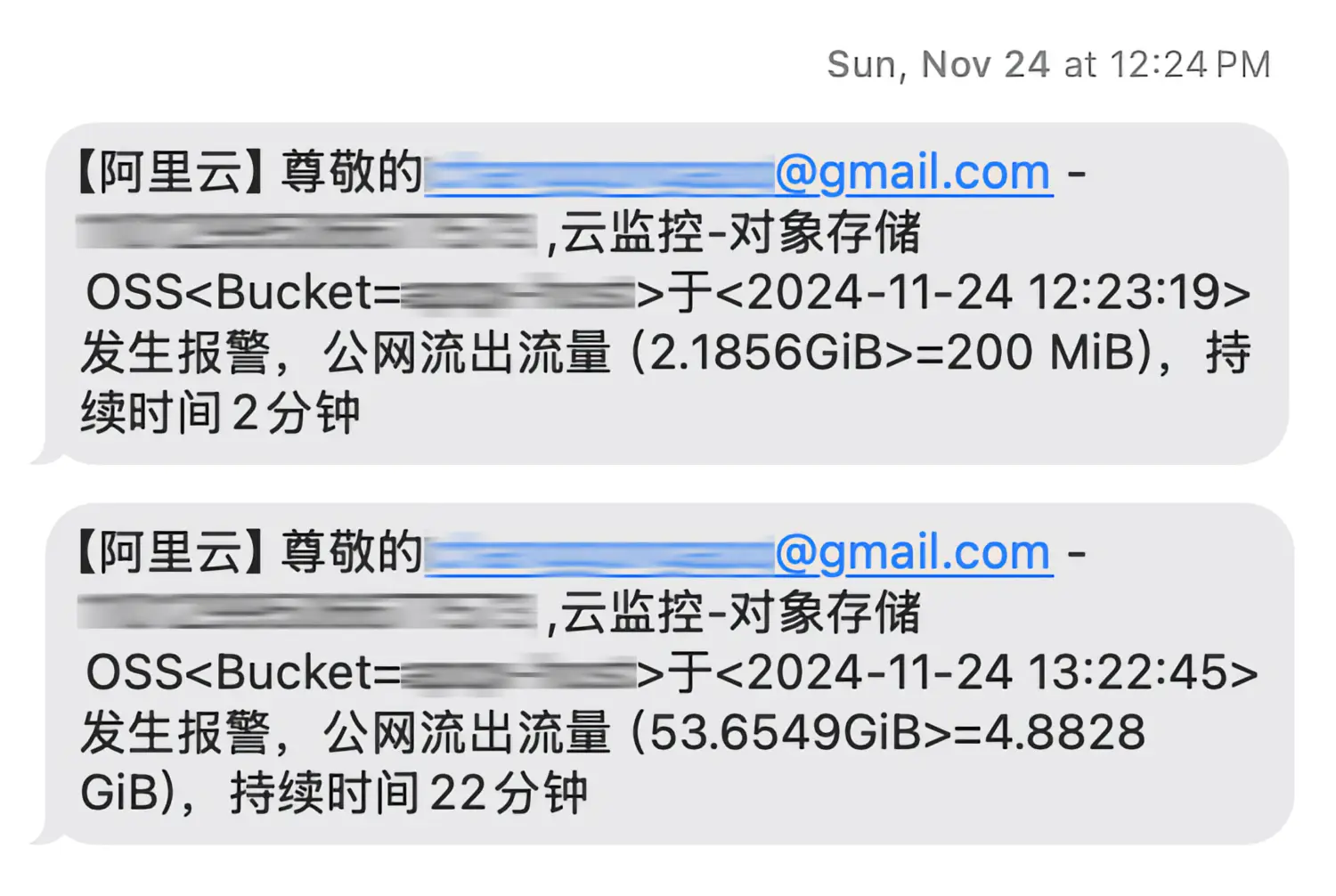{: loading="lazy" class="clickable clickShowOriginalImg" alt="Aliyun warning sms" } | ||
|
|
||
| 意识到预想中的情况发生了,拿出手机打开博客果然无法访问,倒是长舒一口气,看来提前配置的监控策略已经成功关闭`OSS`对外服务。 | ||
|
|
||
| ## 解析 | ||
|
|
||
| 去阿里云控制台翻看日志,发现在`12:29`~`12:25`的6分钟内对同一个字体文件有62万次请求: | ||
|
|
||
| 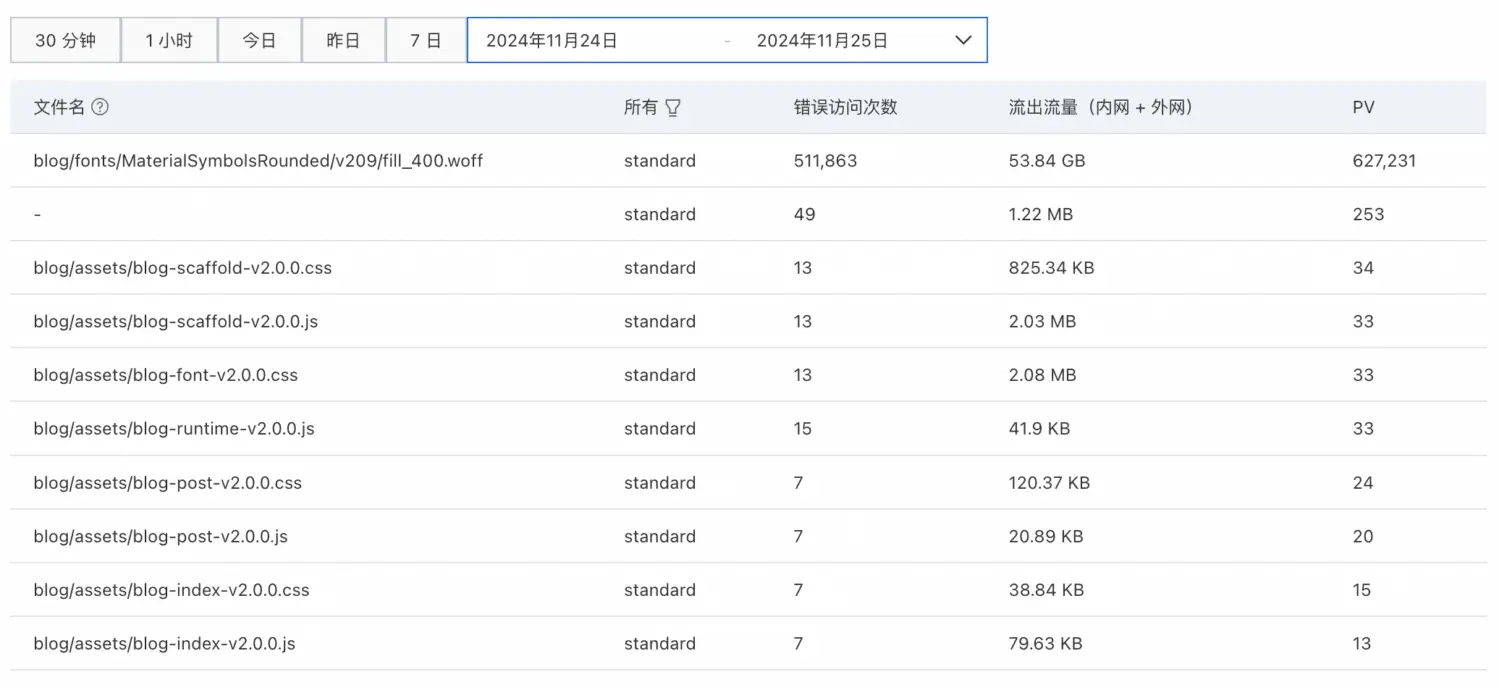{: loading="lazy" class="clickable clickShowOriginalImg" alt="Aliyun most requested resource" } | ||
|
|
||
| 主要来自4个北美/德国的`IP`地址: | ||
|
|
||
| 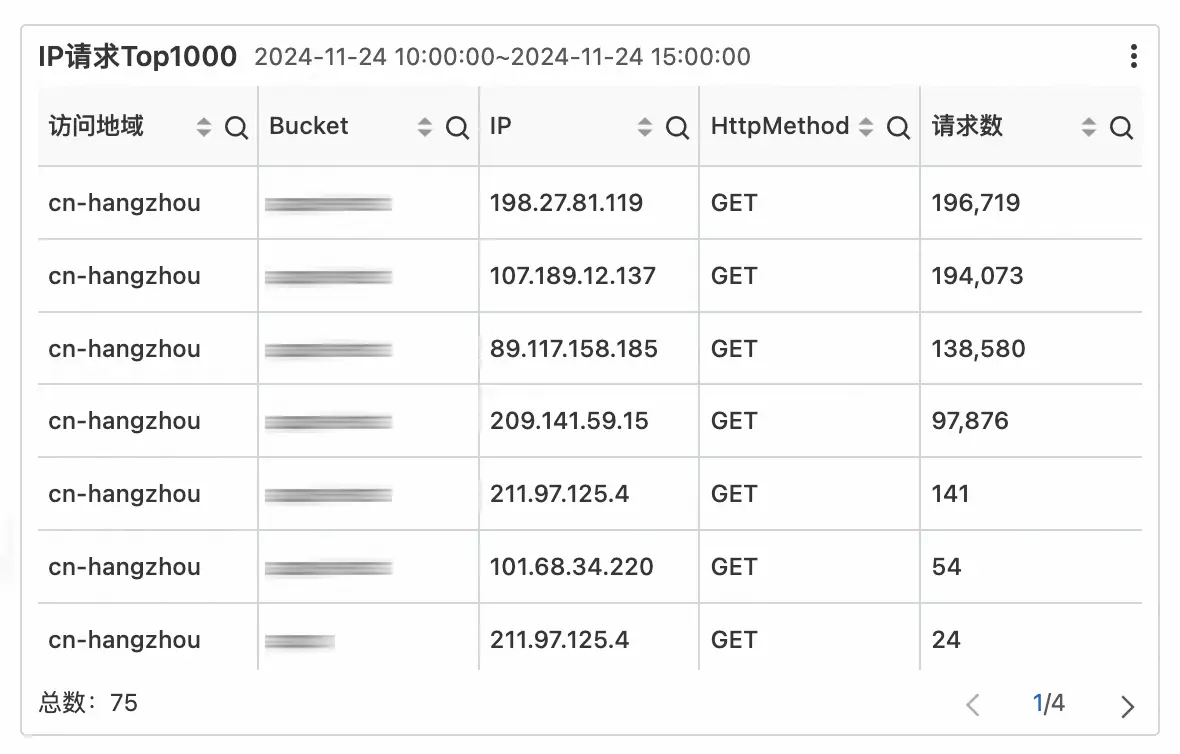{: loading="lazy" class="clickable clickShowOriginalImg" alt="Aliyun top client ip" } | ||
|
|
||
| 橘红色代表成功请求,绿色代表失败请求,可以看到在一个时间点后失败陡增,即`OSS`开始关闭对外服务: | ||
|
|
||
| 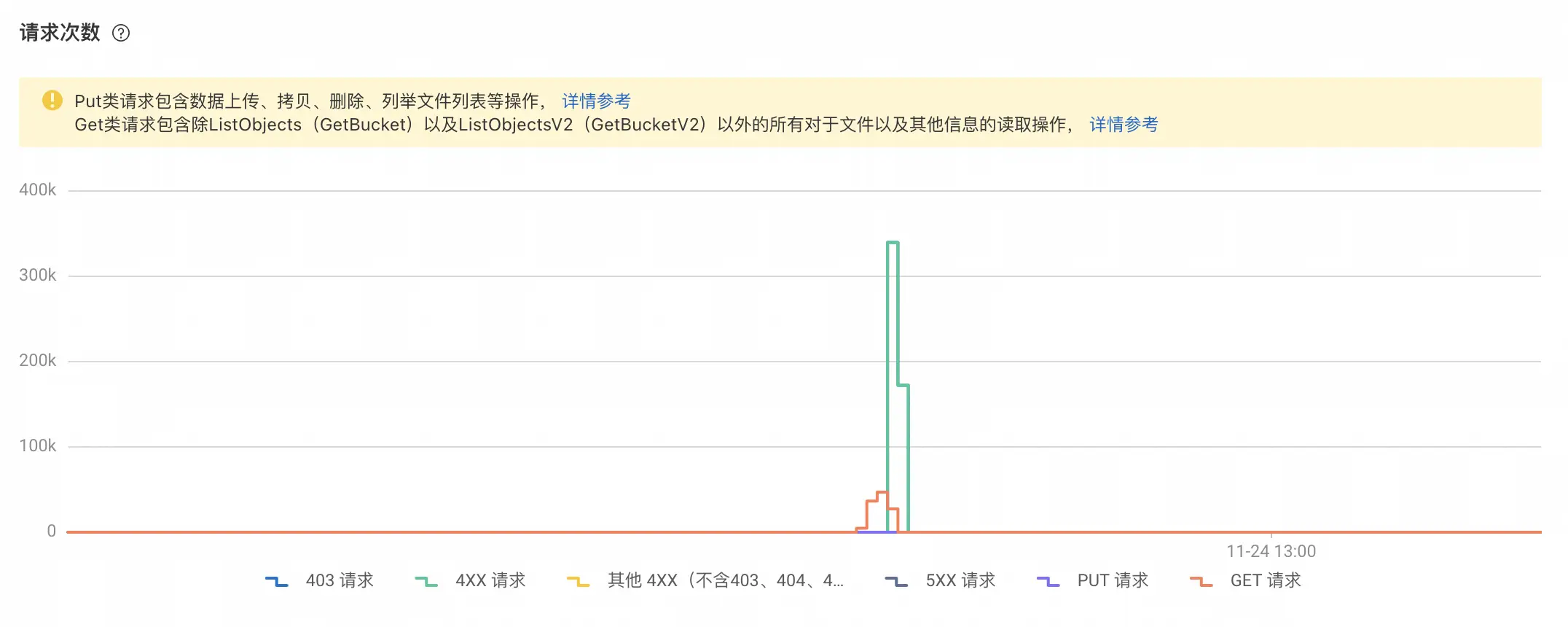{: loading="lazy" class="clickable clickShowOriginalImg" alt="Aliyun request timeline" } | ||
|
|
||
| 结合阿里云给出的访问数据整理出以分钟为单位的时间线: | ||
|
|
||
|
|
||
| | 时间 | 成功请求数 | 失败请求数 | 公网流出流量 | | ||
| |-----------------|------------|------------|--------------| | ||
| | 12:19~12:20 | 89 | 0 | 5.3MB | | ||
| | **12:20~12:21** | 4700 | 0 | **2.2GB** | | ||
| | 12:21~12:22 | 36455 | 0 | 17.0GB | | ||
| | 12:22~12:23 | 46944 | 7 | 21.8GB | | ||
| | **12:23~12:24** | 27255 | **339730** | 12.7GB | | ||
| | 12:24~12:25 | 2 | 172155 | 0.4MB | | ||
| | 12:25~12:25 | 4 | 2 | 0MB | | ||
| {: .should-wrap-table} | ||
|
|
||
| 从表格看,`12:20`~`12:21`公网流出流量超出预警值,但直到`12:23`~`12:24`才出现大量失败请求,与短信显示的报警时间`12:23:19`吻合。查询触发的`函数计算`日志,是在`12:23:26`执行关闭`OSS`对外服务。 | ||
|
|
||
| 显然,报警时间晚了2分钟。我在`云监控`中设置的粒度单位是分钟,应该在`12:21`~`12:22`触发报警才对,事实证明`云监控`也并非实时,耸肩。 | ||
|
|
||
| 总结起来,攻击持续5分钟,前3分钟畅通无阻,共62万次请求,其中11万次成功,消耗53GB流量和对应的25元账单。这种家庭带宽就能轻易发起的流量攻击对普通博主的成本伤害是挺大的,商业带宽并不廉价,接入网络需要谨慎配置监控策略,小心成为“一晚上被盗刷一套房”的都市传说主角🙄。 |
Large diffs are not rendered by default.
Oops, something went wrong.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters