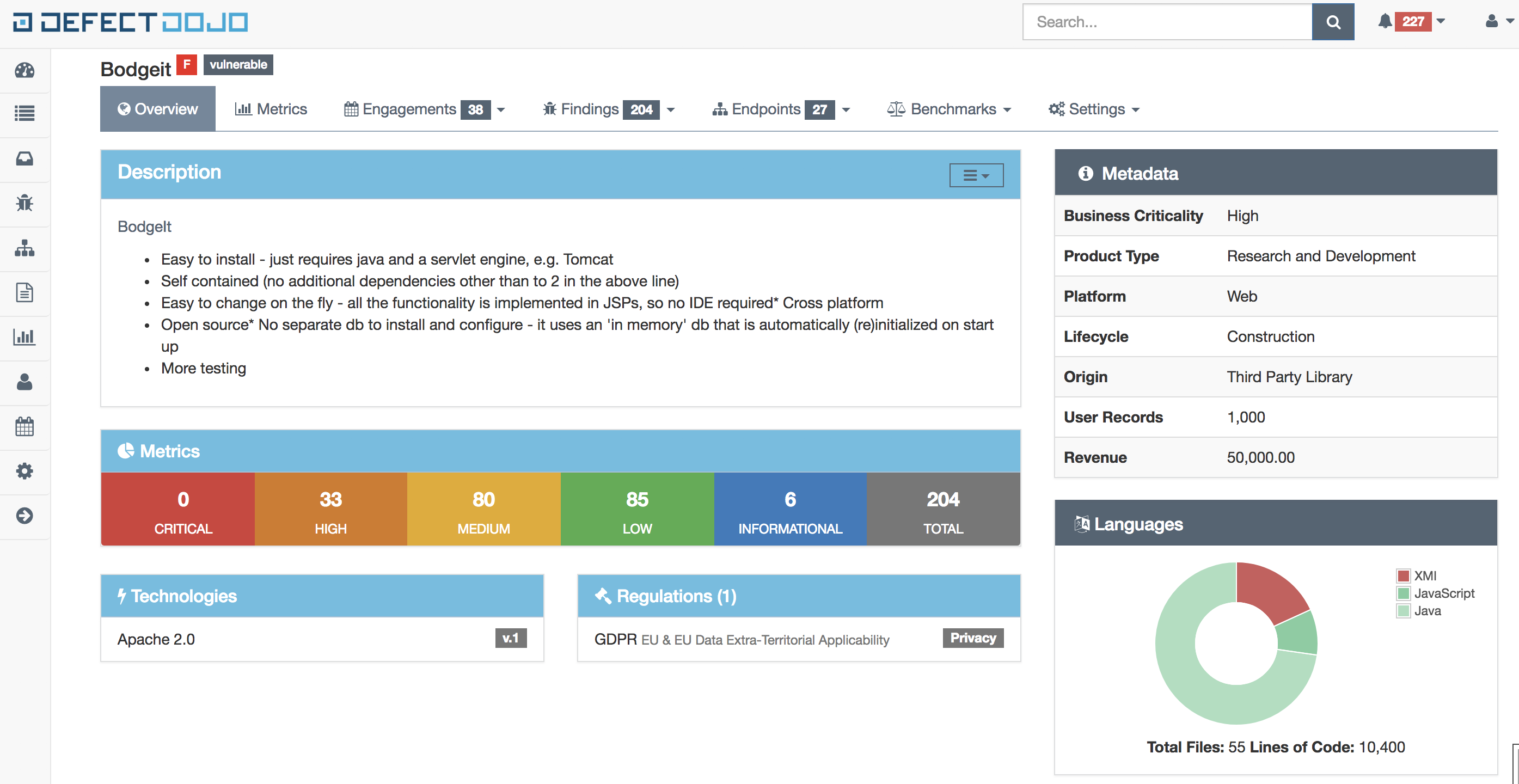
DefectDojo is a security orchestration and vulnerability management platform. DefectDojo allows you to manage your application security program, maintain product and application information, triage vulnerabilities and push findings to systems like JIRA and Slack. DefectDojo enriches and refines vulnerability data using a number of heuristic algrothims that improve with the more you use the platform.
Try out the demo sever at demo.defectdojo.org
Log in with admin / defectdojo@demo#appsec. Please note that the demo is pubicly accessable and regularly reset. Do not put sensitive data in the demo.
git clone https://github.com/DefectDojo/django-DefectDojo
cd django-DefectDojo
# building
docker-compose build
# running
docker-compose up
# obtain admin credentials. the initializer can take up to 3 minutes to run
# use docker-compose logs -f initializer to track progress
docker-compose logs initializer | grep "Admin password:"Navigate to http://localhost:8080.
Join the slack community and discussion! Realtime discussion is done in the OWASP Slack Channel, #defectdojo. Follow DefectDojo on Twitter, Linkedin, and YouTube for project updates!
Commercial support and training is availaible through 10Security.
10Security was founded by the creators of DefectDojo. For information please email info@10security.com or visit our site.
DefectDojo is maintained by:
Project Moderators can help you with pull requests or feedback on dev ideas.
- Alex Dracea
- Valentijn Scholten (sponsor | linkedin)
- Jannik Jürgens
- Fred Blaise
- Cody Maffucci
- Pascal Trovatelli / Sopra Steria
- Damien Carol
- Stefan Fleckenstein
- Charles Neill (@ccneill) – Charles served as a DefectDojo Maintainer for years and wrote some of Dojo's core functionality.
- Jay Paz (@jjpaz) – Jay was a DefectDojo maintainer for years. He performed Dojo's first UI overhaul, optimized code structure/features, and added numerous enhancements.
DefectDojo is licensed under the BSD Simplified license