Mapping the attack surface of any target.
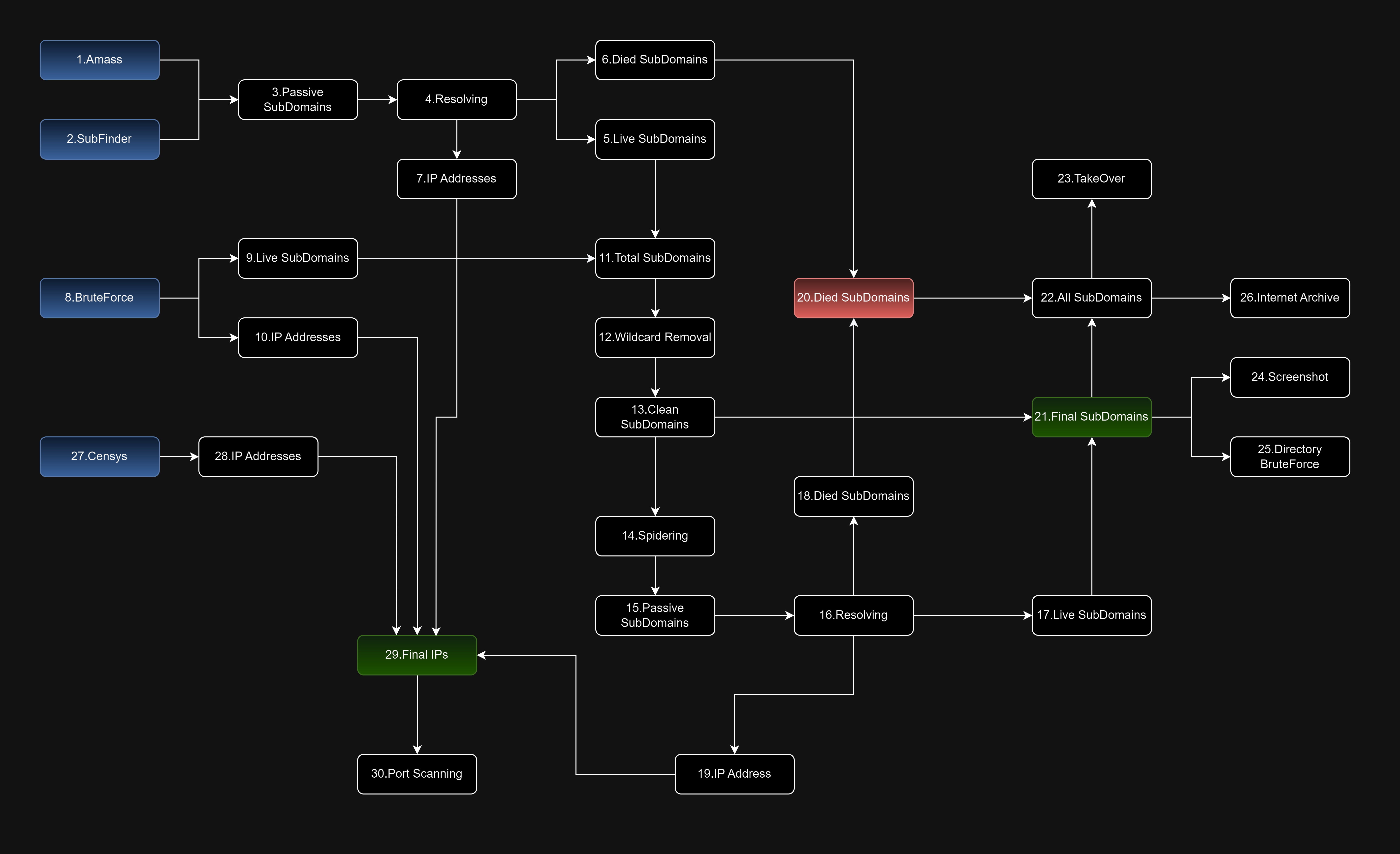
- Sub-Domains Passive Scraping
- Sub-Domains Brute Force
- Sub-Domains Wildcard Removal
- Sub-Domains Spidering
- Sub-Domains Takeover
- IPs Enumeration using Censys
- Port Scanning
- Websites' Screenshots
- Directories & Files Brute Force
- Internet Archive
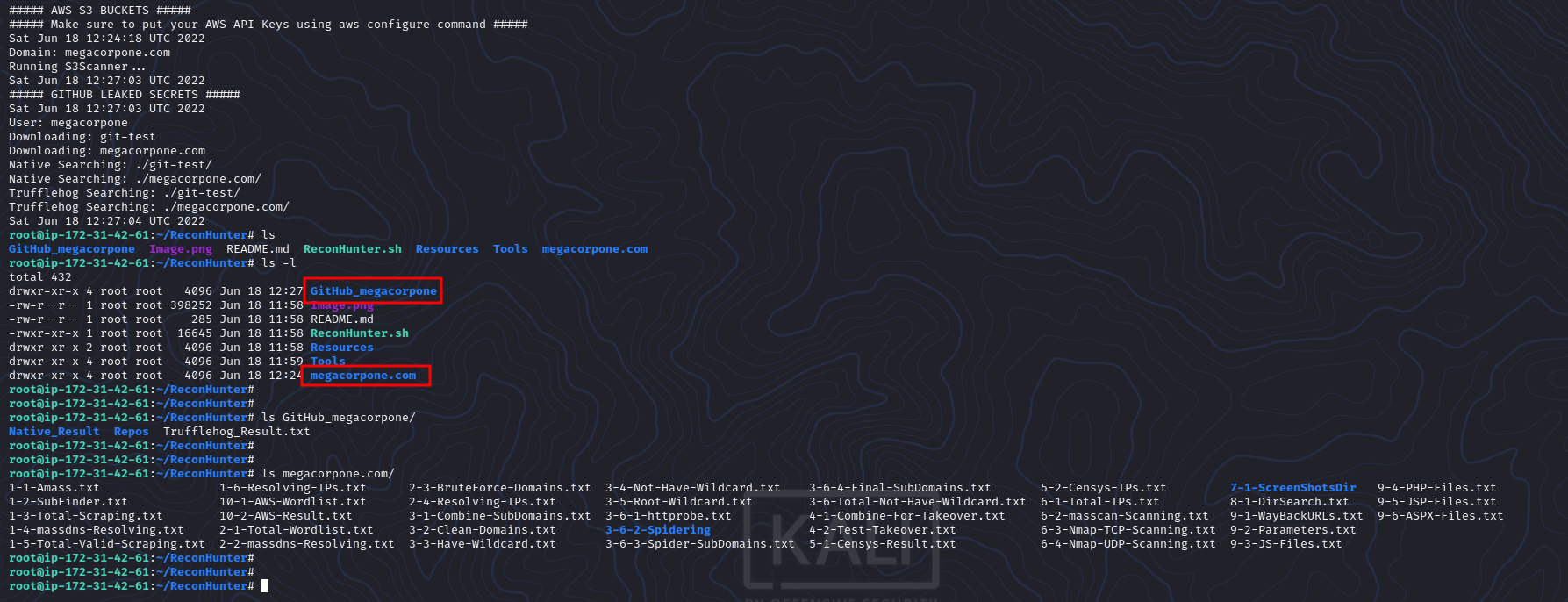
- AWS S3 Buckets
- Github Leaked Secrets
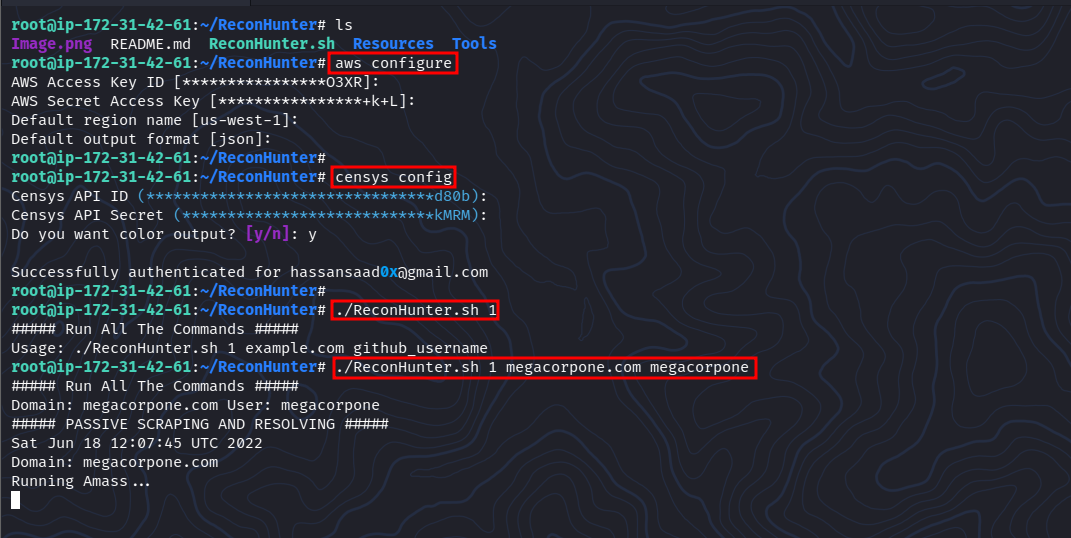
You need to insert the AWS key also the Censys Key to use all the tool features.
aws configure
censys config
# Installation
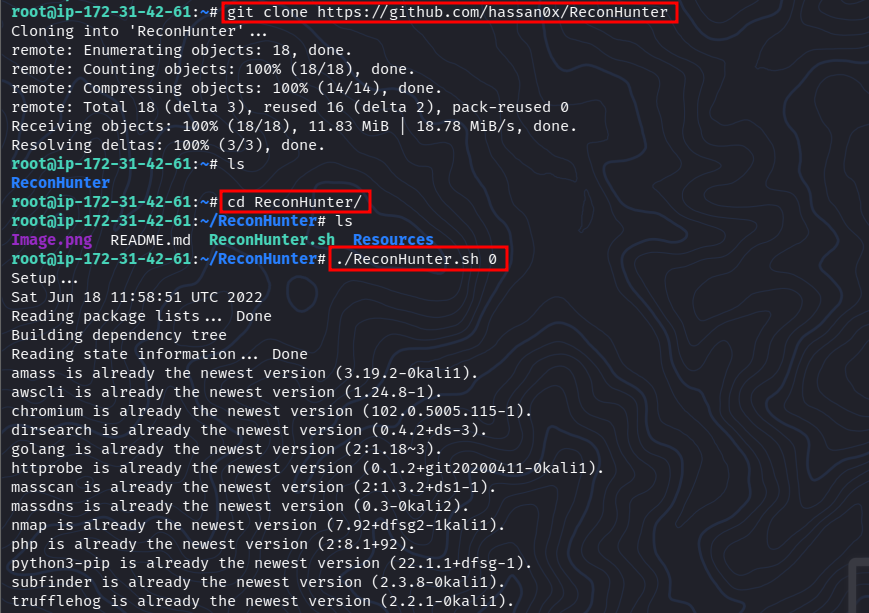
git clone https://github.com/hassan0x/ReconHunter
cd ReconHunter
./ReconHunter 0
# Help
./ReconHunter
# Run All the Commands
./ReconHunter 1 $domain_name $github_user
./ReconHunter 1 example.com user1
The tool has been tried and validated on kali linux.
- Amass
- SubFinder
- MassDNS
- GoSpider
- HTTProbe
- SubOver
- Censys
- Masscan
- Nmap
- Aquatone
- DirSearch
- WayBackUrls
- Unfurl
- S3Scanner
- AWScli
- TruffleHog
- Making a stealthy mode to reduce the noisy of the tool.