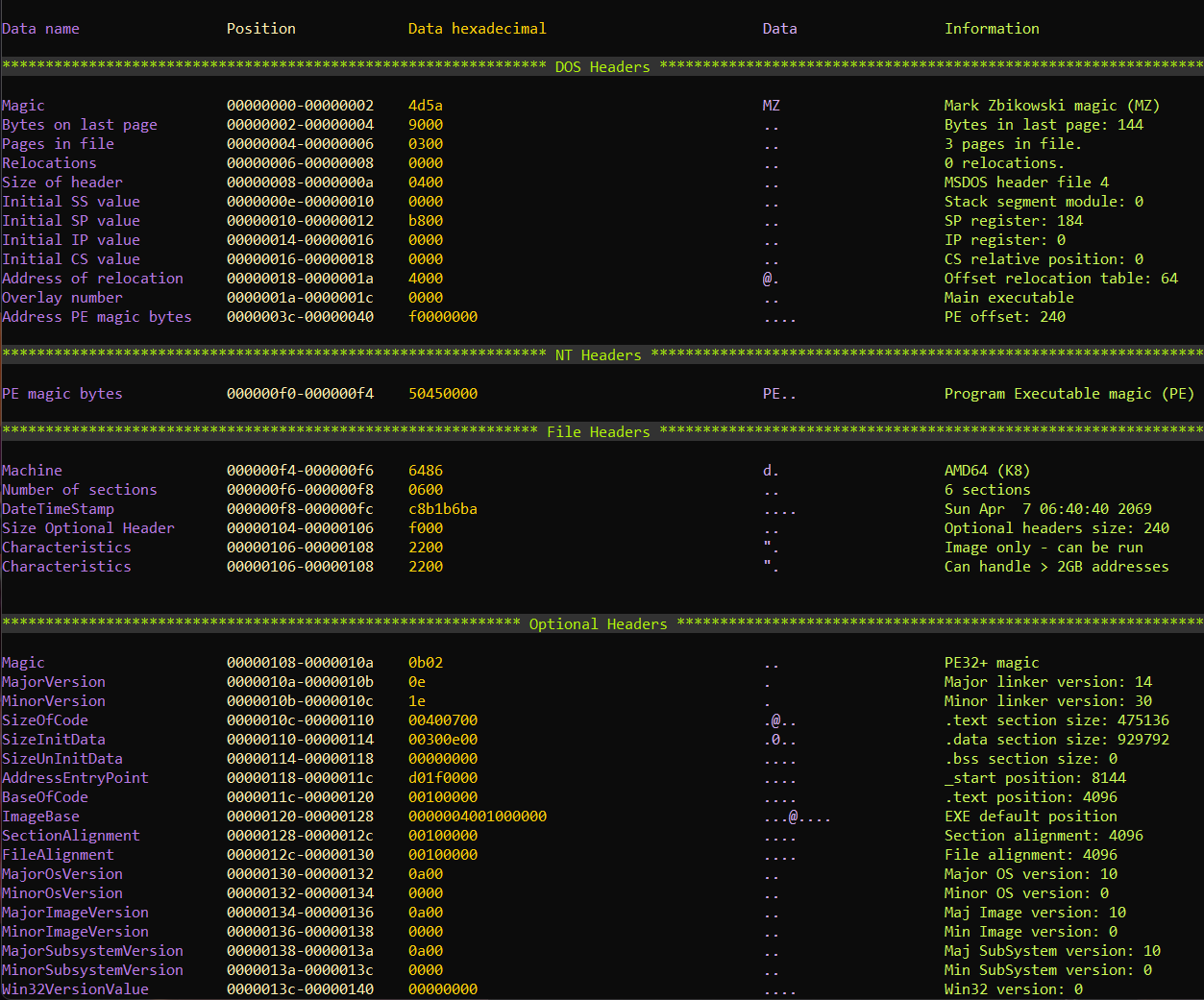
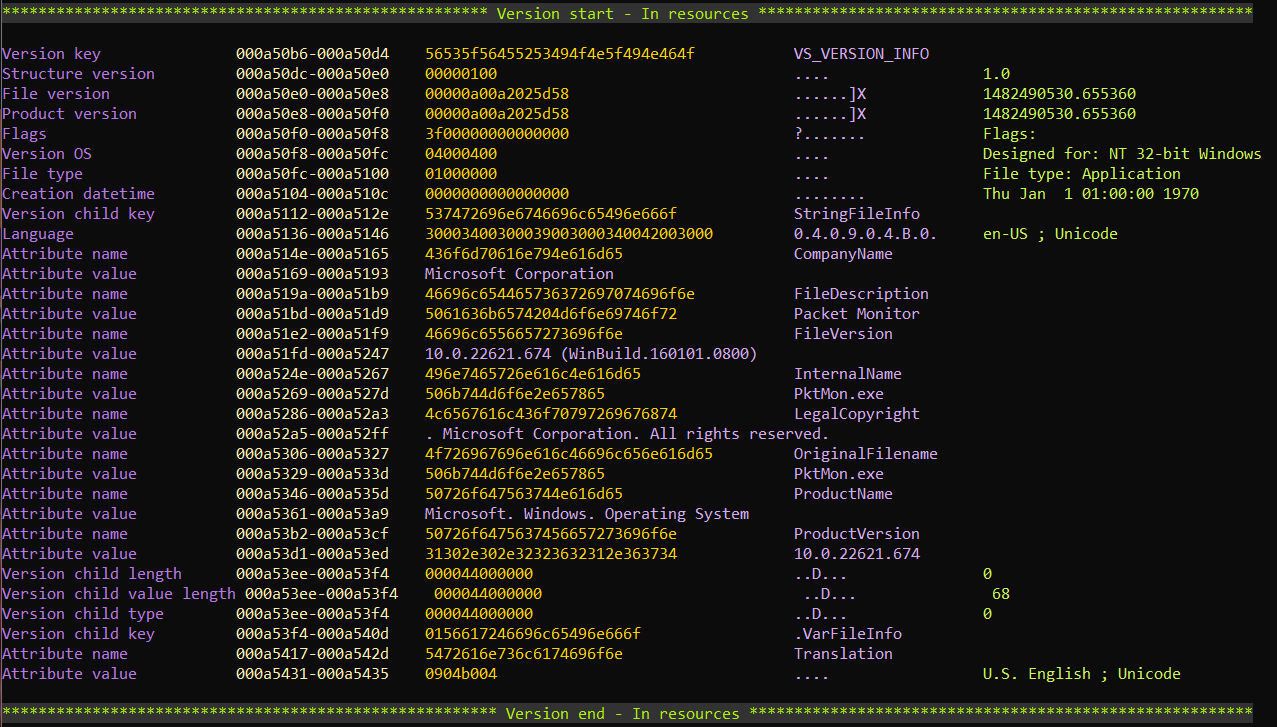
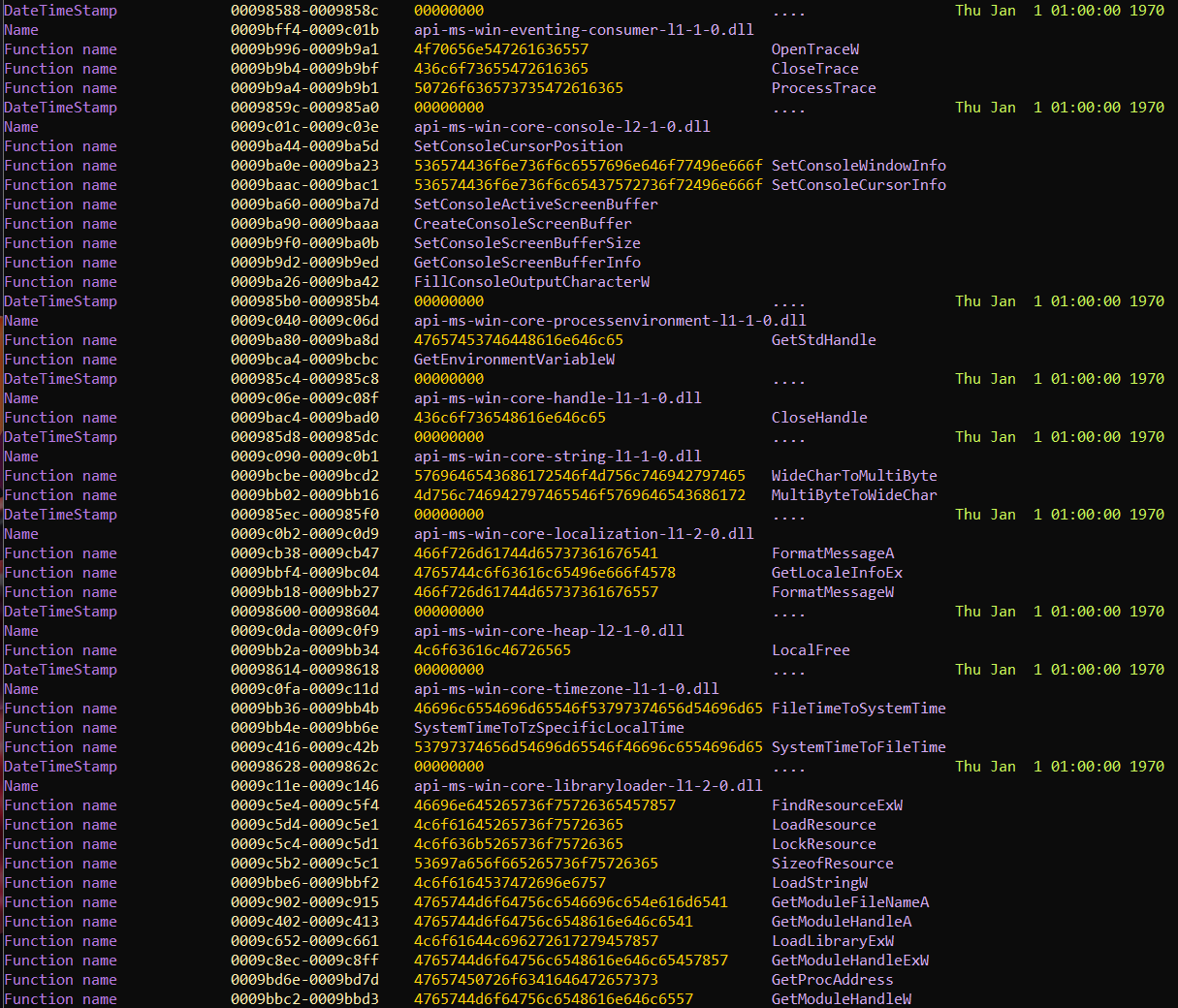
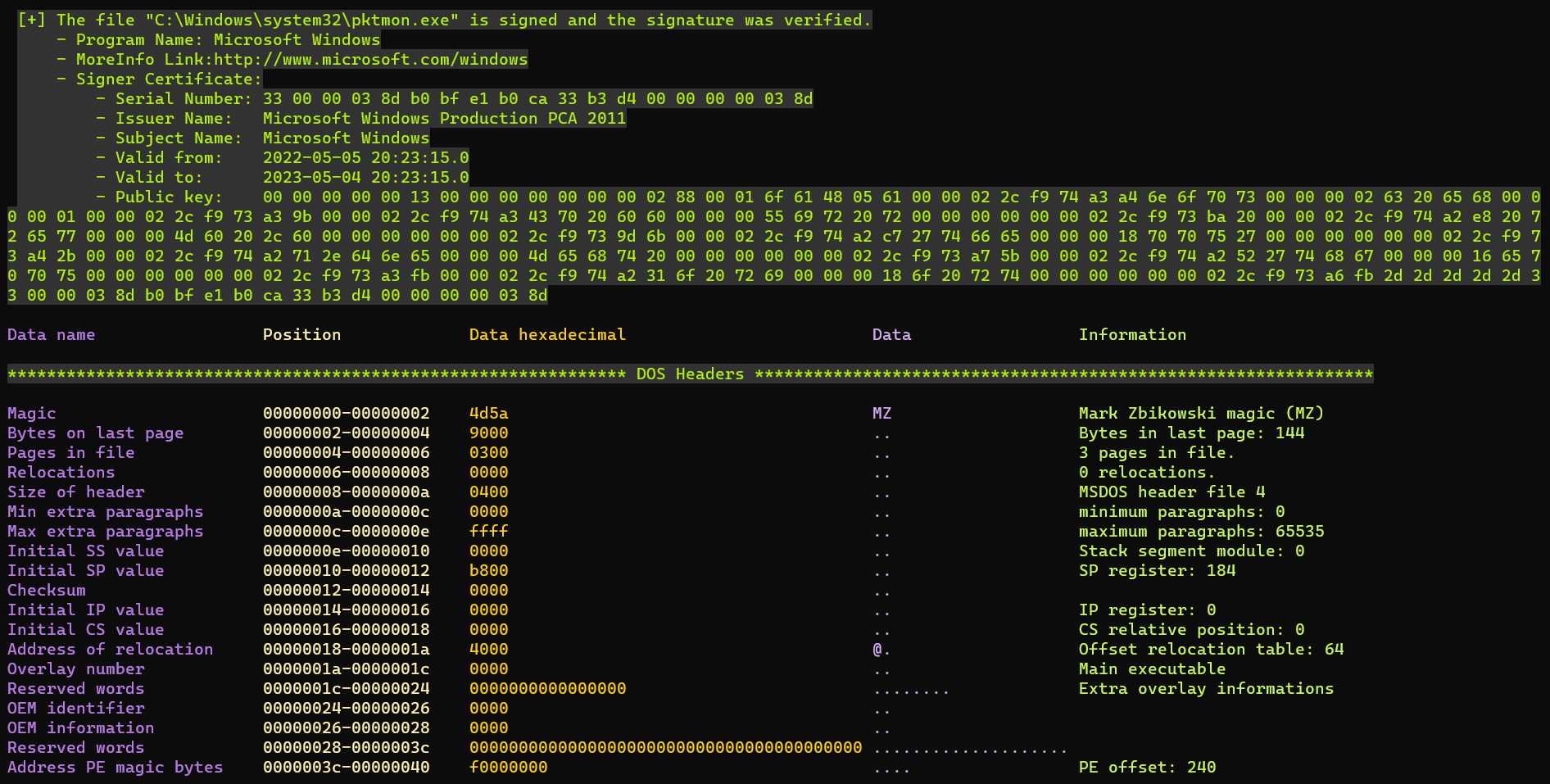
This script analyzes MZ-PE (MS-DOS) executable file.
This tool is useful for malware analysis or debug/understand compiled dependencies.
- Verify signature and print informations about signature and trust
- Analyze DLLs and imported functions name
- Analyze exported functions name
- Get executable filename at the compiled time
- Get encodings and languages used for compilation
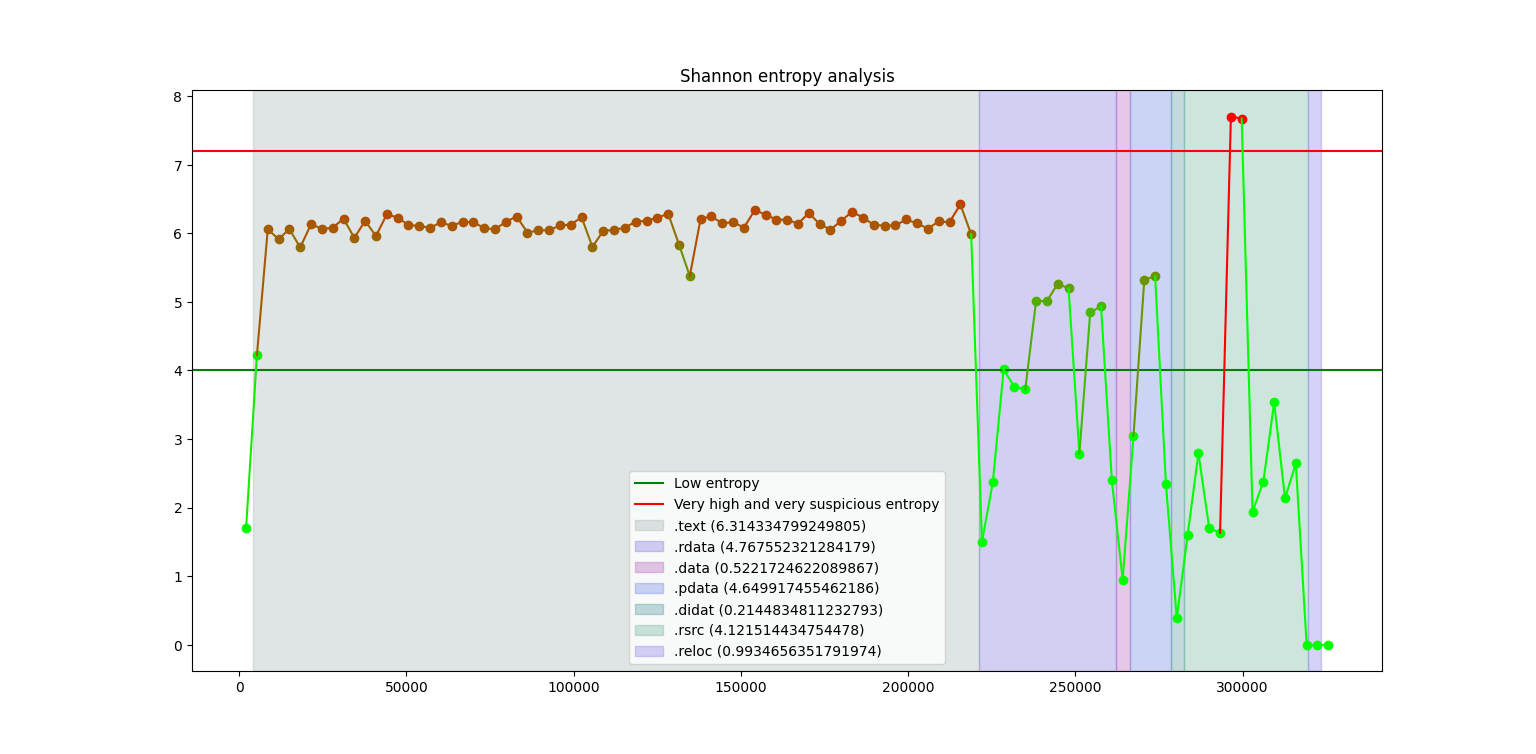
- Print informations about rich headers
- Get timestamps saved in executable
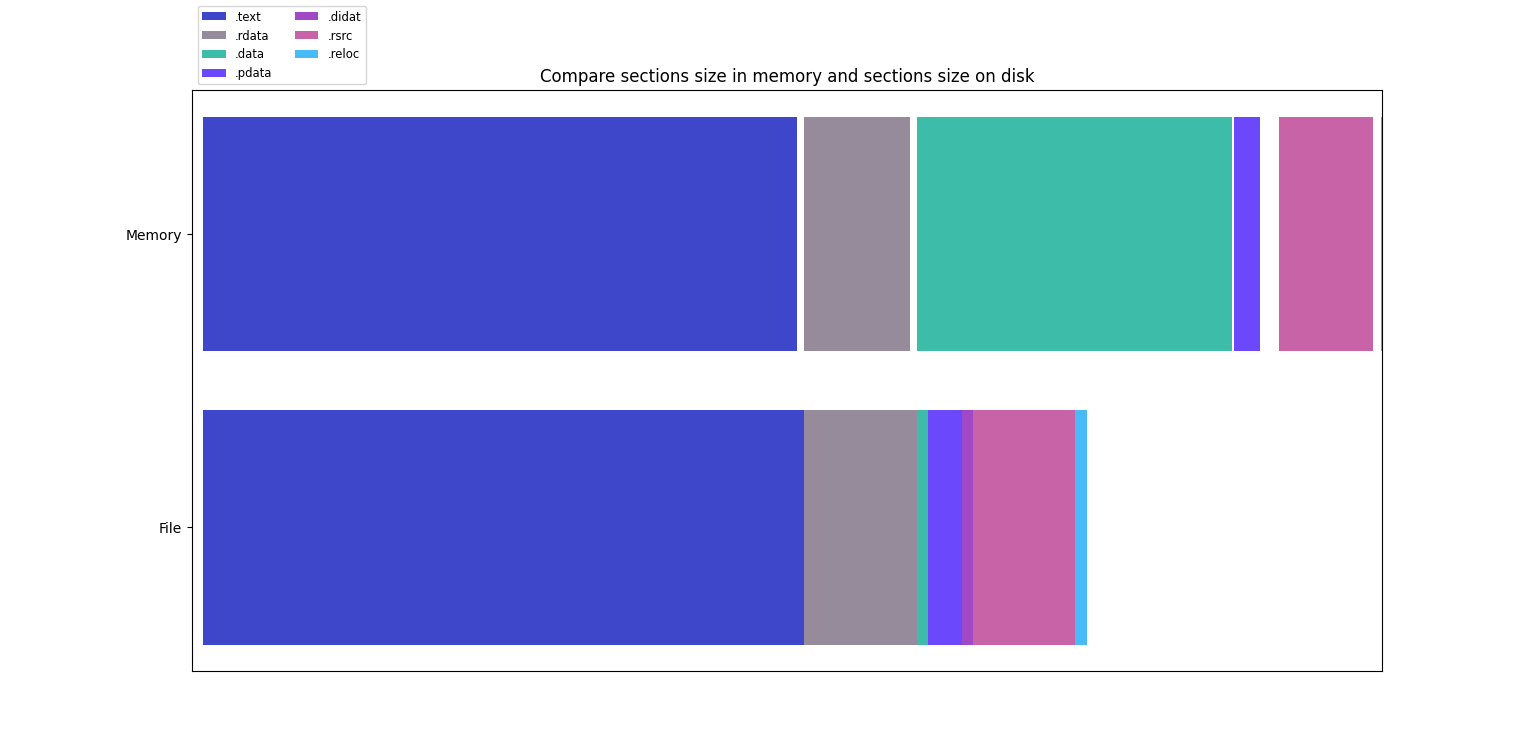
- Print informations about sections and characteristics (permissions, ect...)
- Print the entry point position and section
- Get architecture, system version, resources (Version file, Manifest)
- Get company name, product name, product version, copyright
- Sections names, sizes, addresses and characteristics
- Analyze MS-DOS and NT headers
- When matplotlib is installed, generate charts to compare sections on the disk and in the memory
- When matplotlib and EntropyAnalysis are installed, generate charts for entropy analysis (with sections)
- Extract overlay
TODO: analyze results to detect language and score the risk.
- python3
- Python 3 Standard library
- matplotlib
- EntropyAnalysis
Matplotlib and EntropyAnalysis are not installed by ProgramExecutableAnalyzer because this package can be installed on server without GUI.
You can install optinal required packages with the following command:
python3 -m pip install matplotlib EntropyAnalysis
pip install ProgramExecutableAnalyzerpython3 ProgramExecutableAnalyzer.py -h
python3 ProgramExecutableAnalyzer.py executable.exe
python3 ProgramExecutableAnalyzer.py -c executable.exe # No color
python3 ProgramExecutableAnalyzer.py -v executable.exe # Verbose modeLicensed under the GPL, version 3.