-
Notifications
You must be signed in to change notification settings - Fork 280
4.3.0 What's New
Mirth Connect 4.3.0 includes new features such as Setup Wizard enhancements as well as changes, updates, and improvements. Mirth Connect 32-bit Windows executable and zip files will not be supported after December 31, 2023. If you are running Mirth Connect using 32-bit for Windows, make plans to use Mirth Connect 64-bit for Windows in the future.
-
Core Mirth Connect
- New Features
-
Fixed Defects
- The TCP Listener Now Correctly Binds to the Specified Local Address
- Null Pointer Exception When Using Custom Extensions
- Previous Message Shows in Message View When Messages Have Been Filtered Out
- Prevent Overwriting the log4j2.properties File during an Upgrade
- The Ports in Use List Is Empty if Any Port Contains a Variable
- Fixed NullPointerException in Client if Clipboard is Empty During Login
- Prevent Username from Disappearing From the Bottom of the Screen
- Strict Parser Adding Namespace in the Wrong Spot
- User with Channel Permissions May Get an Error Message When Creating a New Channel
- Security Improvements
- Commercial Extension Improvements
- Docker Images
- Administrator Launcher
You can find the list of completed issues for this release here.
We added new features to the Mirth Connect Setup Wizard that include, but are not limited to, the following:
- We added more information on the screens with links to the What's New, Upgrade Guide, and documentation. This helps users understand what options to enter on the screens.
- We added the ability to install your extensions at the time Mirth Connect is installed or upgraded. This simplifies the process so that users no longer have to install extensions manually and restart the service.
- We added the ability to enter your license key for extensions. This will default to the
license.keyvalue from yourmirth.propertiesfile during an upgrade. - We added our new logo and a list of each dialog screen so that users know exactly where they are in the process.
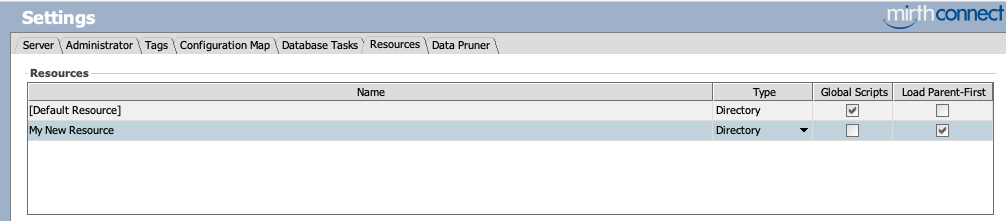
Added the Ability for Resource and Channel-Specific Classloaders to Load Child-First or Parent-First
We've added the ability to specify whether resources should load classes "child-first" or "parent-first". Previously, all resource classloaders loaded "parent-first". This meant that when a user attempted to use a class that is already included with Mirth Connect, such as a PostgreSQL driver, the class was loaded from the parent classloader instead of loading the custom version that the user wanted. The user can now achieve the desired behavior using a "child-first" classloader. We have also made "child-first" the default option. (Community Issue)
We merged a GitHub pull request to add a default implementation of the getObjectsForSwaggerExamples() method in the ServicePlugin class. This makes it easier for extension developers by not requiring them to implement this method in subclasses of ServicePlugin. (Community Issue)
A correction was made to the TCP Listener to bind to the localhost as entered in the "Local Address - Specific interface" field. Previously, the TCP Listener would bind to all interfaces (0.0.0.0). (Community Issue)
We fixed a null pointer exception that occurred when using a custom extension that extends the ChannelColumnPlugin abstract class. (Community Issue]
We fixed an issue where a message that should have no contents would display the contents from a previously viewed message. (Community Issue)
We fixed the issue where the log4j2.properties file were being overwritten during an upgrade, so any customizations will now be retained. (Community Issue)
We fixed the issue where the ports list would error if the channel contained a string variable instead of an integer value. The port's property has been changed to a string to remedy this. We also are passing the ports list through the TemplateReplacer method to render the mapped variables as their context values. (Community Issue)
We merged the GitHub pull request to fixed an issue where Mirth Connect can potentially throw a NullPointerException if the clipboard is empty during login. (Community Issue)
We corrected an issue where the Username that appears at the bottom of the screen would disappear when clicking Save in the Settings screen. (Community Issue)
We made a correction so that the Strict Parser adds the namespace to the XML header in the correct position. (Community Issue)
We fixed an issue where an error message displays when a user that has channel-related permissions but does not have the permission to view system settings attempts to create a new channel. (Community Issue)
The default encryption algorithm has been updated from AES to AES/CBC/PKCS5Padding. In addition, before being encrypted, strings will be encoded using UTF-8 instead of the JVM default charset. (Community Issue)
-
If you did not have
encryption.algorithmalready overridden in mirth.properties, then no action is required. Any newly encrypted data will just use the new default algorithm, and old encrypted data will still be able to be decrypted (using the old default algorithm). -
If you had
encryption.algorithmoverridden and set toAES, then you should consider updating that, for example toAES/CBC/PKCS5PaddingorAES/GCM/NoPadding. Mirth Connect will warn you on startup with this message as well. Support forAES(without any mode/padding specified) will be removed in a future version.
The mirth-crypto library is now included in the open-source Mirth Connect core codebase to allow users to distribute Connect. (Community Issue)
In 4.3.0, the following weak cipher suites have been disabled by default:
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA
For more information on TLS Cipher Suite changes see the 4.3.0 Upgrade Guide. (Community Issue)
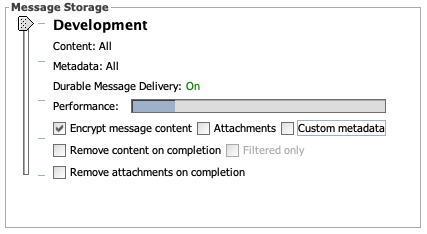
We've added options to encrypt message attachments and custom metadata when storing them in the database. This is configurable on a per-channel basis in the Message Storage settings. Encrypted attachments and custom metadata are still viewable through the Message Browser just like encrypted message content. Note that only STRING type custom metadata columns will be encrypted, and they won't be searchable via the Message Browser. (Community Issue)
The OpenJDK and AdoptOpenJDK base images have been deprecated, so the official Mirth Connect Docker images that were previously built with those base images are now built with the eclipse-temurin image.
We merged the GitHub pull request. The Mirth Connect server ID can now be set with the Docker environment variable SERVER_ID. See the Docker Hub Page for additional details. (Community Issue)
We've released a new version of the Mirth Connect Administrator Launcher that includes new code signing certificates. Mirth Connect 4.3.0 is signed with an updated certificate, so you will need to update the Administrator Launcher to avoid seeing security warnings.
- Home
- Frequently Asked Questions
- Source Code Contribution
- Java Licensing
- How to Contribute to the Wiki
- Administrator Launcher (MCAL)
-
Mirth Connect
-
Release Notes
- 4.5.0 - What's New
- 4.4.0 - What's New
- 4.3.0 - What's New
- 4.2.0 - What's New
- 4.1.0 - What's New
- 4.0.0 - What's New
- 3.12.0 - What's New
- 3.11.0 - What's New
- 3.10.0 - What's New
- 3.9.0 - What's New
- 3.8.0 - What's New
- 3.7.0 - What's New
- 3.6.0 - What's New
- 3.5.0 - What's New
- 3.4.0 - What's New
- 3.3.0 - What's New
- 3.2.0 - What's New
- 3.1.0 - What's New
- 3.0.0 - What's New
- Upgrading
-
Release Notes
- User Guide
- Commercial Extensions
- Examples and Tutorials