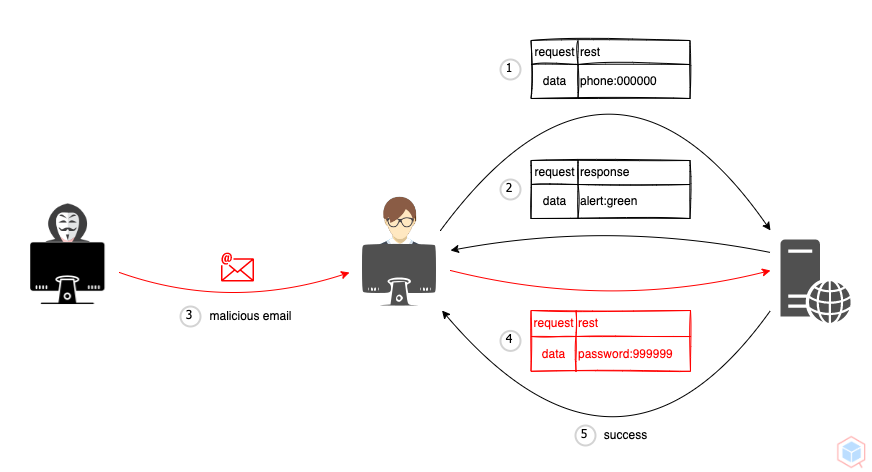
A threat actor may trick a victim into executing native template syntax on a vulnerable target (This is similar SSTI but happens on the client side)
- Threat actor crafts an exploit URL
- Bob logs in to the vulnerable website
- Threat actor tricks Bob into clicking on the exploit URL
- Bob clicks on the exploit URL, and the browser executes the exploit
<html>
<body>
<div id="alert"></d>
<script>
var url = new URL(window.location);
var alert = url.searchParams.get("alert");
document.getElementById('alert').innerHTML = alert
document.body.style.backgroundColor = alert
</script>
</body>
</html>/?alert=<img src="/" onerror=alert("test")>
alert box: test
Vary
- Command execution
- Input validation
- Logic-less
- Client Side Template Injection
- SST injection
477ac741-89fe-4d0b-b094-09d720ed9d83