-
Notifications
You must be signed in to change notification settings - Fork 302
Home
Moved here from Google Code.
Application Layer DoS attacks, such as slowloris, Slow HTTP POST, Slow Read attack (based on TCP persist timer exploit) by draining concurrent connections pool, as well as Apache Range Header attack by causing very significant memory and CPU usage on the server.
Slowloris and Slow HTTP POST DoS attacks rely on the fact that the HTTP protocol, by design, requires requests to be completely received by the server before they are processed. If an HTTP request is not complete, or if the transfer rate is very low, the server keeps its resources busy waiting for the rest of the data. If the server keeps too many resources busy, this creates a denial of service. This tool is sending partial HTTP requests, trying to get denial of service from target HTTP server.
Slow Read DoS attack aims the same resources as slowloris and slow POST, but instead of prolonging the request, it sends legitimate HTTP request and reads the response slowly.
Installation and usage examples
How I knocked down 30 servers using slowhttptest
Slow Read DoS attack explained
Test results of popular HTTP servers
How to protect against slow HTTP DoS attacks
Many thanks to Tigran Gevorgyan and Victor Agababov for tons of help and support. The logo is from http://openclipart.org/detail/168031/.
Some links to the media coverage, for historical purposes:
ArsTechnica The Verge TechWorld DarkReading
SlowHTTPTest version1.6 is out. Thanks to Comcast for not having Internet for two days, managed to do a lot of things. This release includes all the small bug fixes that were sitting in SVN for over a year, usability improvements and better reporting. Check it out and leave some feedback! Blog post with changes and hints
Released version 1.5 with improved CPU utilization, some bug fixes, and proxy support, which means you can direct either probe or entire traffic through a specified web proxy.
Released version 1.4 with poll() support, which means slowhttptest is not limited to 1024 connections anymore. Added man page, fixed several bugs, including build issues on FreeBSD and cygwin.
Released version 1.3 with Slow Read Denial of Service attack support.
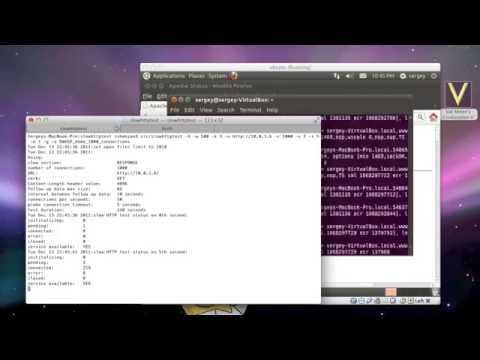
Check out the video with demonstration of the attack:
Released version 1.2. The major new feature is the indicator of HTTP server's availability. Instead of refreshing the page in the browser to figure out if the web server is down, let slowhttptest to request the target web page every second and track the status in log messages and statistics files. Installation and usage examples page is updated with detailed description of how probe connection should be configured and used.
Charts now show intervals when server was not available:
Released version 1.1 that includes test mode for Apache Range header handling DoS vulnerability test
First version of slowhttptest is released.