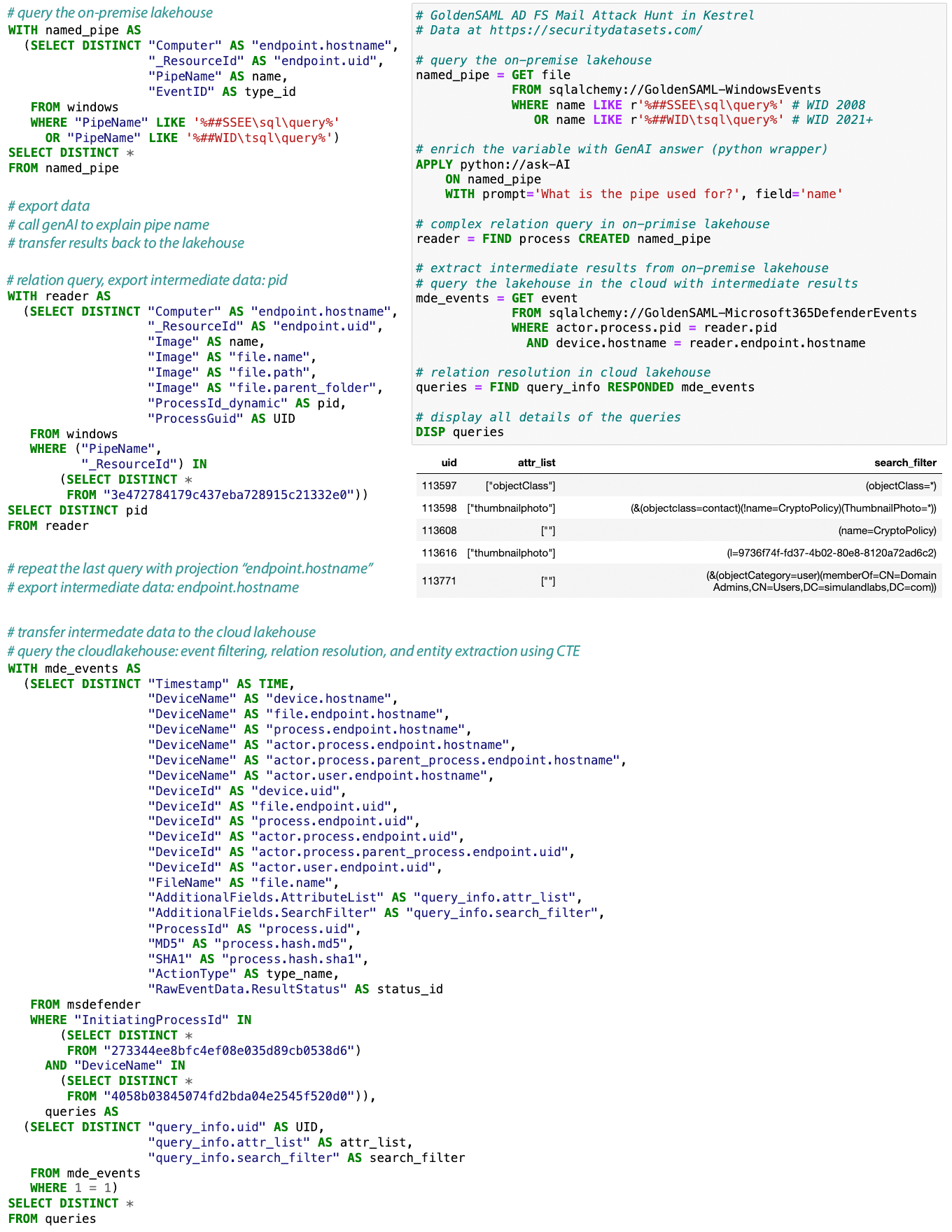
*An end-to-end cyber threat hunt usually requires execution across multiple datasources/environments plus enrichment/ML/visualization steps anywhere in the huntflow.
Kestrel is a threat hunting language aiming to make cyber threat hunting fast by providing a layer of abstraction to build reusable, composable, and shareable hunt-flow. Starting with:
- Black Hat USA 2024 Kestrel hunting lab
- Black Hat USA 2022 Kestrel hunting lab
- Black Hat USA 2022 session recording
- Register Black Hat USA 2024 to hunt with Kestrel
- Kestrel and AI talk at CNCF Secure AI Summit 2024
- Learn scalable Kestrel deployment at Red Hat Research Quarterly (RHRQ)
Software developers write Python or Swift than machine code to quickly turn business logic into applications. Threat hunters write Kestrel to quickly turn threat hypotheses into hunt-flow. We see threat hunting as an interactive procedure to create customized intrusion detection systems on the fly, and hunt-flow is to hunts as control-flow is to ordinary programs.
- Kestrel language: a threat hunting language for a human to express what to
hunt.
- expressing the knowledge of what in patterns, analytics, and hunt flows.
- composing reusable hunting flows from individual hunting steps.
- reasoning with human-friendly entity-based data representation abstraction.
- thinking across heterogeneous data and threat intelligence sources.
- applying existing public and proprietary detection logic as analytic hunt steps.
- reusing and sharing individual hunting steps, hunt-flow, and entire huntbooks.
- Kestrel runtime: a machine interpreter that deals with how to hunt.
- compiling the what against specific hunting platform instructions.
- executing the compiled code locally and remotely.
- assembling raw logs and records into entities for entity-based reasoning.
- caching intermediate data and related records for fast response.
- prefetching related logs and records for link construction between entities.
- defining extensible interfaces for data sources and analytics execution.
Visit Kestrel documentation to learn Kestrel:
- Learn concepts and syntax:
- Hunt in your environment:
Kestrel 2 debuts at Black Hat USA 2024. While maintaining the language syntax from Kestrel 1, we entirely redesign Kestrel 2 runtime to achieve better performance and more flexible syntax regarding entity, attribute, and relation representations.
Key features of Kestrel 2:
- Just-in-time compilation instead of interpretation
- Lazy evaluation and the new
EXPLAINcommand - Data Lakehouse optimization with deeply nested query
- OCSF and OpenTelemetry entity/attribute support besides STIX
Kestrel 2 is currently in beta, learn more at Kestrel runtime installation.
- Kestrel huntbook: community-contributed Kestrel huntbooks
- Kestrel analytics: community-contributed Kestrel analytics
- Building a Huntbook to Discover Persistent Threats from Scheduled Windows Tasks
- Practicing Backward And Forward Tracking Hunts on A Windows Host
- Building Your Own Kestrel Analytics and Sharing With the Community
- Setting Up The Open Hunting Stack in Hybrid Cloud With Kestrel and SysFlow
- Try Kestrel in a Cloud Sandbox
- Fun with securitydatasets.com and the Kestrel PowerShell Deobfuscator
- Kestrel Data Retrieval Explained
Talk summary (visit Kestrel documentation on talks to learn details):
- 2024/08 Black Hat USA 2024
- 2024/06 CNCF Secure AI Summit 2024
- 2023/08 Black Hat USA 2023
- 2022/12 Infosec Jupyterthon 2022 [IJ'22 live hunt recording]
- 2022/08 Black Hat USA 2022 [BH'22 recording | BH'22 hunting lab]
- 2022/06 Cybersecurity Automation Workshop
- 2022/04 SC eSummit on Threat Hunting & Offense Security (free to register/playback)
- 2021/12 Infosec Jupyterthon 2021 [IJ'21 live hunt recording]
- 2021/11 BlackHat Europe 2021
- 2021/10 SANS Threat Hunting Summit 2021: [SANS'21 session recording]
- 2021/05 RSA Conference 2021: [RSA'21 session recording]
Join Kestrel slack channel:
Get a slack invitation to join Open Cybersecurity Alliance workspace
Join the kestrel channel to ask questions and connect with other hunters
Contribute to the language development (Apache License 2.0):
- Create a GitHub Issue to report bugs and suggest new features
- Follow the contributing guideline to submit your pull request
- Refer to the governance documentation regarding PR merge, release, and vulnerability disclosure
Share your huntbook and analytics: