UnityVulnerableEntryPoint is a tool that uses AsmResolver for assembly manipulation and for searching an entry point in your favorite game for cheating, because anti-cheats such as BattlEye have hardcoded checks for modules inside of a game, in this case, you can easily find entry point - edit this method via dnSpy or other decompiler and load your cheats in Ring3 (user mode). If you have any questions/issues please let me know there. You can install the latest version of UnityVulnerableEntryPoint here.
- More information and discussions can be found there on the unknowncheats post
Tool searches for a call/callvirt CIL instructions into the specified file (and because of that this is very important to load all references of the file, to make able to get access to the signature, etc), then takes the operand and trying to resolve method from there and make sure if method base type it's not a specified file module and if the base type is MonoBehaviour.
If you will find an entry point, be careful because you will be able to play but, it's only 5-6 minutes (tested with BE) and you need to reconnect to the server after being disconnected or find a better way to edit this method.
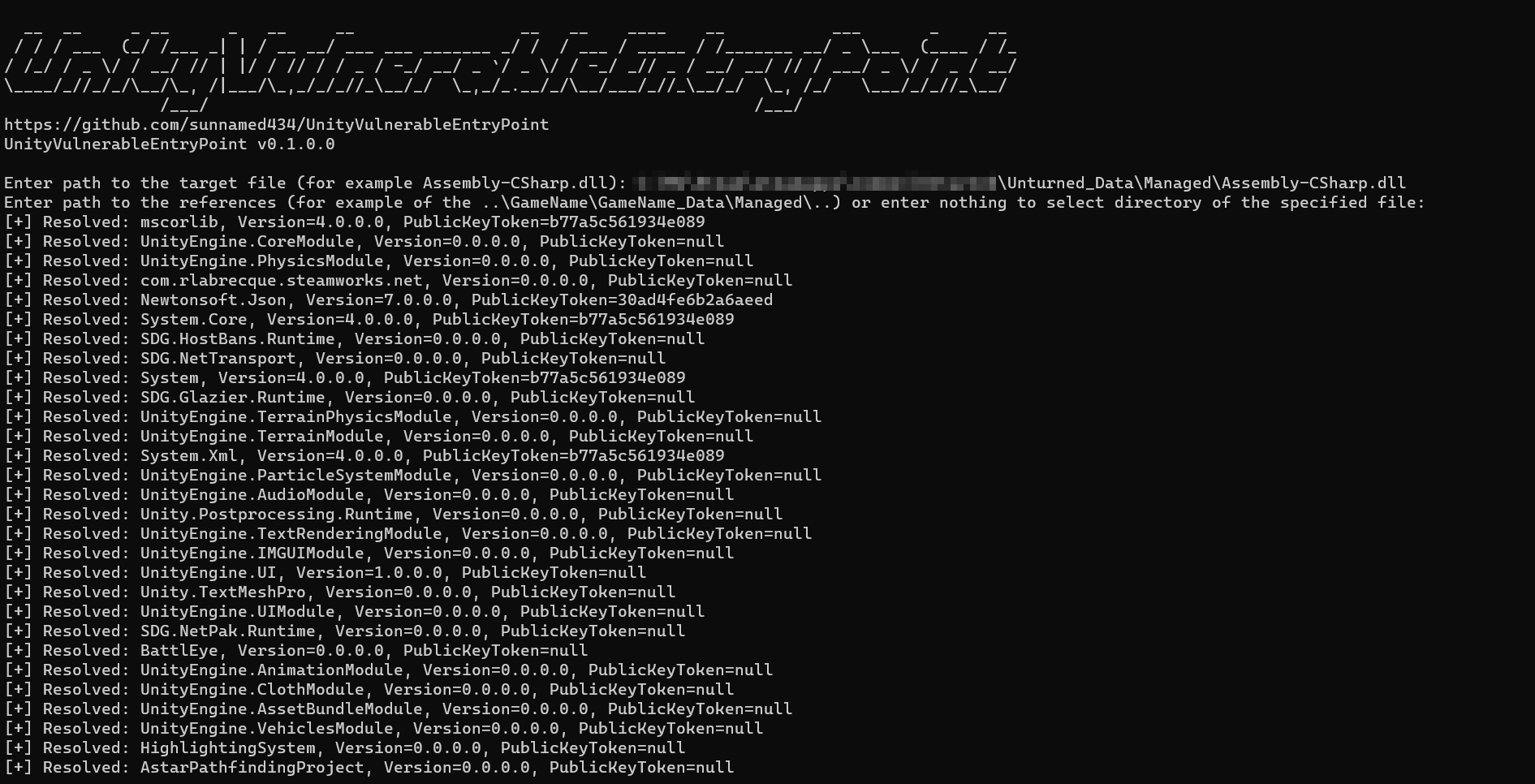
- Startup UnityVulnerableEntryPoint.CLI.exe
- Enter path to the Assembly-CSharp.dll
- Enter path to the Assembly-CSharp.dll references or just stay it empty
-f, --file Required. Set target file path.
-r, --references Set references of file, stay empty to specify the path from file path.
--help Display this help screen.
--version Display version information.
$ UnityVulnerableEntryPoint.CLI.exe -f <path to the file> -r <path to the file references>Don't specify the references if they're in the same folder as path to the file
$ UnityVulnerableEntryPoint.CLI.exe -f <path to the file>For this post by nayrde, for the knowledge and motivation of creating this magic tool