-
Notifications
You must be signed in to change notification settings - Fork 5
6.CES svc策略配置
myf5 edited this page Dec 5, 2021
·
5 revisions
一个namespace/project设定的策略会针对该ns/project下的所有微服务进行策略设定。而在大规模微服务的场景下,一个namespace/project会存在多个相对自治的微服务,这些微服务会有独立的egress策略规则需求,比如microservice A需要访问X API,而microservice B需要访问Y API,microsservice C则无需访问集群外部资源。在这样场景下,需要为各个不同的k8s service设定策略。
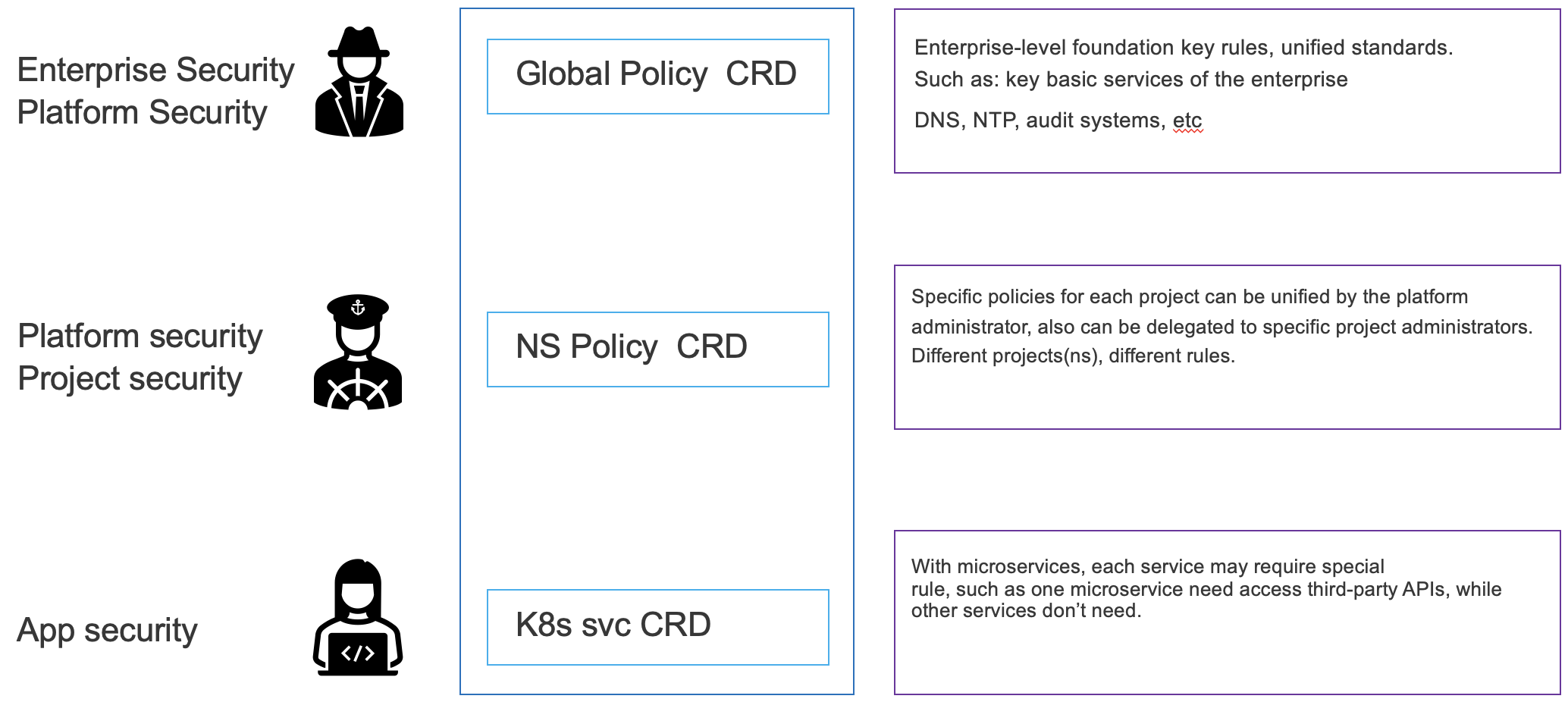
- 首先创建待访问的目标服务。该服务需位于对应的namespace下。支持IP,域名,协议组合,支持仅IP的任意协议:
kind: ExternalService
apiVersion: kubeovn.io/v1alpha1
metadata:
name: ns600-linjing-io
namespace: ns-600
spec:
addresses:
- linjing.io
ports:
- name: tcp-80
protocol: TCP
port: "80"
- 创建针对k8s svc myapp设定rule,容许其访问linjing.io。同时设定打开针对该规则的logging(全局configmap中需配置容许记录日志)
apiVersion: kubeovn.io/v1alpha1
kind: ServiceEgressRule
metadata:
name: myapp-to-linjing-io
namespace: ns-600
spec:
service: myapp
action: accept-decisively
externalServices:
- ns600-linjing-io
logging: true
当前ns-600下存在两个不同的服务:
[root@ovnmaster ~]# kubectl get pod -n ns-600
NAME READY STATUS RESTARTS AGE
myapp-648bc84478-d6sv2 1/1 Running 0 23d
tmp-shell-ns600 1/1 Running 1 176d
进入myapp的容器,可以访问linjing.io:
[root@ovnmaster ~]# kubectl exec -it myapp-648bc84478-d6sv2 -n ns-600 -- sh
~ # curl -I linjing.io
HTTP/1.1 200 OK
Date: Tue, 30 Nov 2021 01:49:04 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
last-modified: Sat, 18 Sep 2021 05:31:50 GMT
access-control-allow-origin: *
expires: Tue, 30 Nov 2021 01:59:04 GMT
cache-control: max-age=600
x-proxy-cache: MISS
x-github-request-id: 8EC0:6FAF:CC1A72:D7CD0A:61A5830F
via: 1.1 varnish
age: 0
x-served-by: cache-tyo11931-TYO
x-cache: MISS
x-cache-hits: 0
x-timer: S1638236944.975011,VS0,VE156
vary: Accept-Encoding
x-fastly-request-id: e9ccc4fdf08a4e83c6bc9bbec67515a5a4e8ce7f
CF-Cache-Status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=kfd1PJRWufdfGilSz4krnmA955bnuSJz%2FUD1rMSfbchq44BUllZLzS7H9R5l6r7Lo%2Byc158ybPJRvG4EBPApU1WI59Q1JY9%2FtVfg5fwYr9GyjefoD2%2BMRnHWyPUQ"}],"group":"cf-nel","max_age":604800}
NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
Server: cloudflare
CF-RAY: 6b606ac3cf7880bf-NRT
进入tmp-shell-ns60容器,无法访问linjing.io:
[root@ovnmaster ~]# kubectl exec -it tmp-shell-ns600 -n ns-600 -- sh
~ # curl -I linjing.io
弹性扩容myapp服务,并进入新pod myapp-648bc84478-qzjrl 进行测试,确认可以访问:
[root@ovnmaster ~]# kubectl get pod -n ns-600
NAME READY STATUS RESTARTS AGE
myapp-648bc84478-d6sv2 1/1 Running 0 23d
myapp-648bc84478-qzjrl 1/1 Running 0 6s
tmp-shell-ns600 1/1 Running 1 176d
[root@ovnmaster ~]# kubectl exec -it myapp-648bc84478-qzjrl -n ns-600 -- sh
~ # curl -I linjing.io
HTTP/1.1 200 OK
Date: Tue, 30 Nov 2021 01:54:49 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
last-modified: Sat, 18 Sep 2021 05:31:50 GMT
access-control-allow-origin: *
expires: Tue, 30 Nov 2021 01:59:04 GMT
cache-control: max-age=600
x-proxy-cache: MISS
x-github-request-id: 8EC0:6FAF:CC1A72:D7CD0A:61A5830F
via: 1.1 varnish
age: 0
x-served-by: cache-tyo11978-TYO
x-cache: MISS
x-cache-hits: 0
x-timer: S1638237289.160179,VS0,VE157
vary: Accept-Encoding
x-fastly-request-id: bb4452a1491ed4a1ed8ae199b510be4fe2e22c3e
CF-Cache-Status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=P3AkBo1nLsiNTUsDw4L%2BafxG8FzLNnN2kr91EfHKOGVRxBS2IKLq6DhcEitSBoFqc7Zr7bavzh%2Bp%2BhqfTVvgNheCJYx9vBWHZKplRPv1YOEqTonpuiQnrtSKt6A2"}],"group":"cf-nel","max_age":604800}
NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
Server: cloudflare
CF-RAY: 6b6073312a0d809b-NRT
下一步