-
Notifications
You must be signed in to change notification settings - Fork 5
EN_5_Namespace_policy
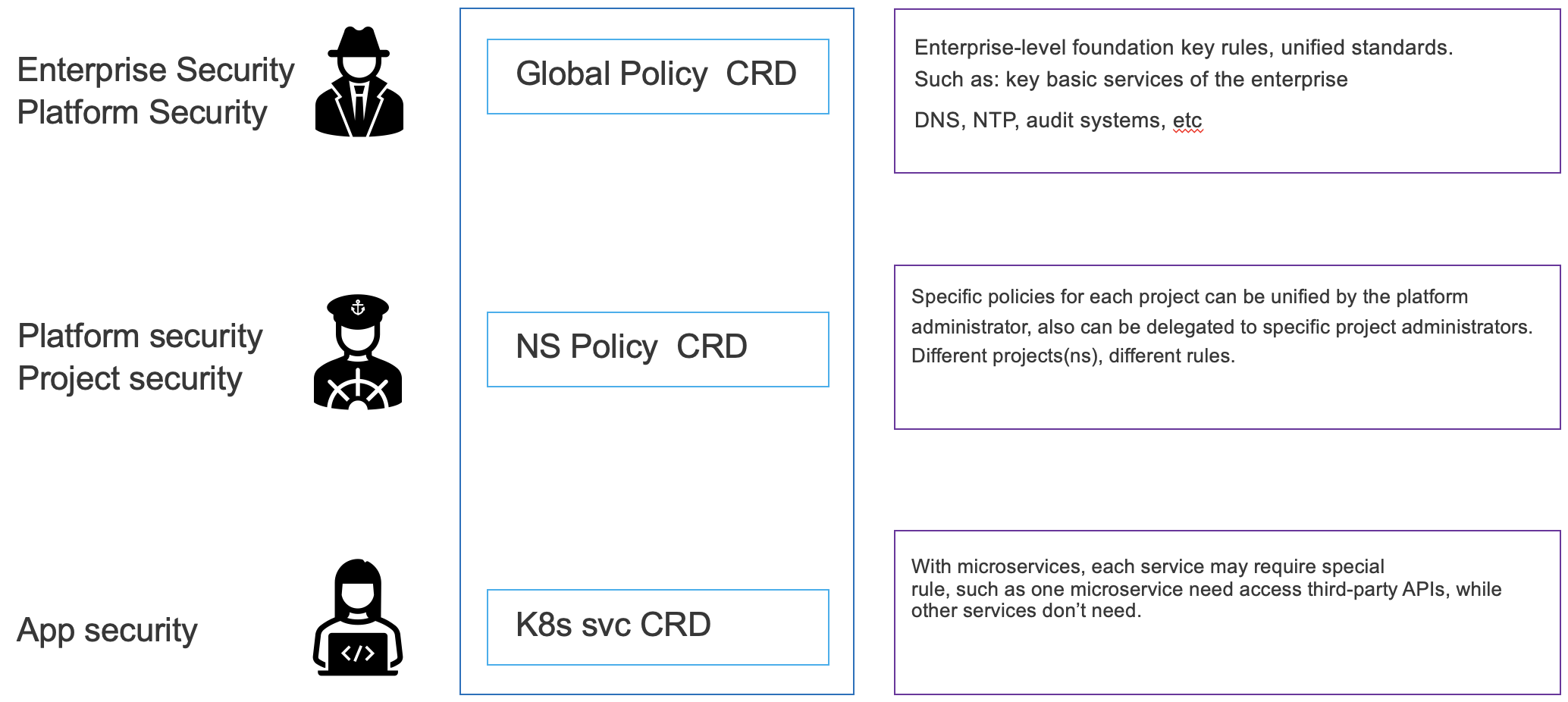
The namespace is generally used for the isolation of projects on the k8s platform, and different projects have different external service access requirements. In terms of management roles, each project is generally managed by the platform administrator or project owner. Therefore, the egress polices of different project need to belong to different namespaces.
This feature requires specific CNI support. The current CES controller supports the kube-ovn(support namespace based subnet). Plan to support Calico's namespace level network in the future.
- First create the target service to be accessed. The service must be located under the corresponding namespace. Support IP, domain name, protocol combination:
# kubectl get externalservices -A
NAMESPACE NAME ADDRESSES
ns-600 ns600-baidu-buck [www.baidu.com]
ns-600 ns600-linjing-io [linjing.io]
ns-600 ns600-nginx-api [3.125.64.247 18.193.151.235]
ns-700 ns700-icbc-api [180.169.80.5]
Dynamic bandwidth limitation can be based on different clients. The administrator who sets the policy only needs to select the appropriate bandwidth limit item from the irules list in the configmap:
# kubectl get externalservices ns600-baidu-bwc -n ns-600 -o yaml
apiVersion: kubeovn.io/v1alpha1
kind: ExternalService
metadata:
name: ns600-baidu-bwc
namespace: ns-600
spec:
addresses:
- www.baidu.com
ports:
- bandwidth: bwc-2mbps-irule
name: tcp-80
port: "80"
protocol: TCP
# kubectl get externalservices ns700-icbc-api -n ns-700 -o yaml
apiVersion: kubeovn.io/v1alpha1
kind: ExternalService
metadata:
name: ns700-icbc-api
namespace: ns-700
spec:
addresses:
- 180.169.80.5
ports:
- name: tcp-80
port: "80"
protocol: TCP
- Create
namespaceegressrulesrules that reference the above target services.namespaceegressrulesNeed to be configured under the corresponding namespace.
# kubectl get namespaceegressrules -A
NAMESPACE NAME ACTION STATUS
ns-600 ns600-allow-baidu-bwc accept-decisively Success
ns-600 ns600-allow-nginx-api accept-decisively Success
ns-700 ns700-allow-icbc-api accept-decisively Success
apiVersion: kubeovn.io/v1alpha1
kind: NamespaceEgressRule
metadata:
name: ns600-allow-baidu-bwc
namespace: ns-600
spec:
action: accept-decisively
externalServices:
- ns600-baidu-bwc
apiVersion: kubeovn.io/v1alpha1
kind: NamespaceEgressRule
metadata:
name: ns700-allow-icbc-api
namespace: ns-700
spec:
action: accept-decisively
externalServices:
- ns700-icbc-api
In the above policy setting, the ns-600namespace setting allows access to www.baiud.com. Access to www.baidu.com is not allowed in the global policy. Therefore ns-600, the service will be accessible to www.baidu.com, but other namespaces will not be accessible.
# kubectl get pod -n ns-600
NAME READY STATUS RESTARTS AGE
myapp-648bc84478-d6sv2 1/1 Running 0 18d
tmp-shell-ns600 1/1 Running 1 170d
# kubectl exec -it tmp-shell-ns600 -n ns-600 -- sh
~ # curl -I www.baidu.com
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: private, no-cache, no-store, proxy-revalidate, no-transform
Connection: keep-alive
Content-Length: 277
Content-Type: text/html
Date: Wed, 24 Nov 2021 06:55:27 GMT
Etag: "575e1f59-115"
Last-Modified: Mon, 13 Jun 2016 02:50:01 GMT
Pragma: no-cache
Server: bfe / 1.0.8.18
Namespace ns-700cannot access baidu.com:
bash-5.1# curl -I www.baidu.com
^C
And pods in ns-700 can access icbc api:
bash-5.1# curl -H "Host: open.icbc.com.cn" 180.169.80.5
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>302 Found</title>
</head><body>
<h1>Found</h1>
<p>The document has moved <a href="https://open.icbc.com.cn/">here</a>.</p>
</body></html>
Next step
k8s service level strategy