-
Notifications
You must be signed in to change notification settings - Fork 5
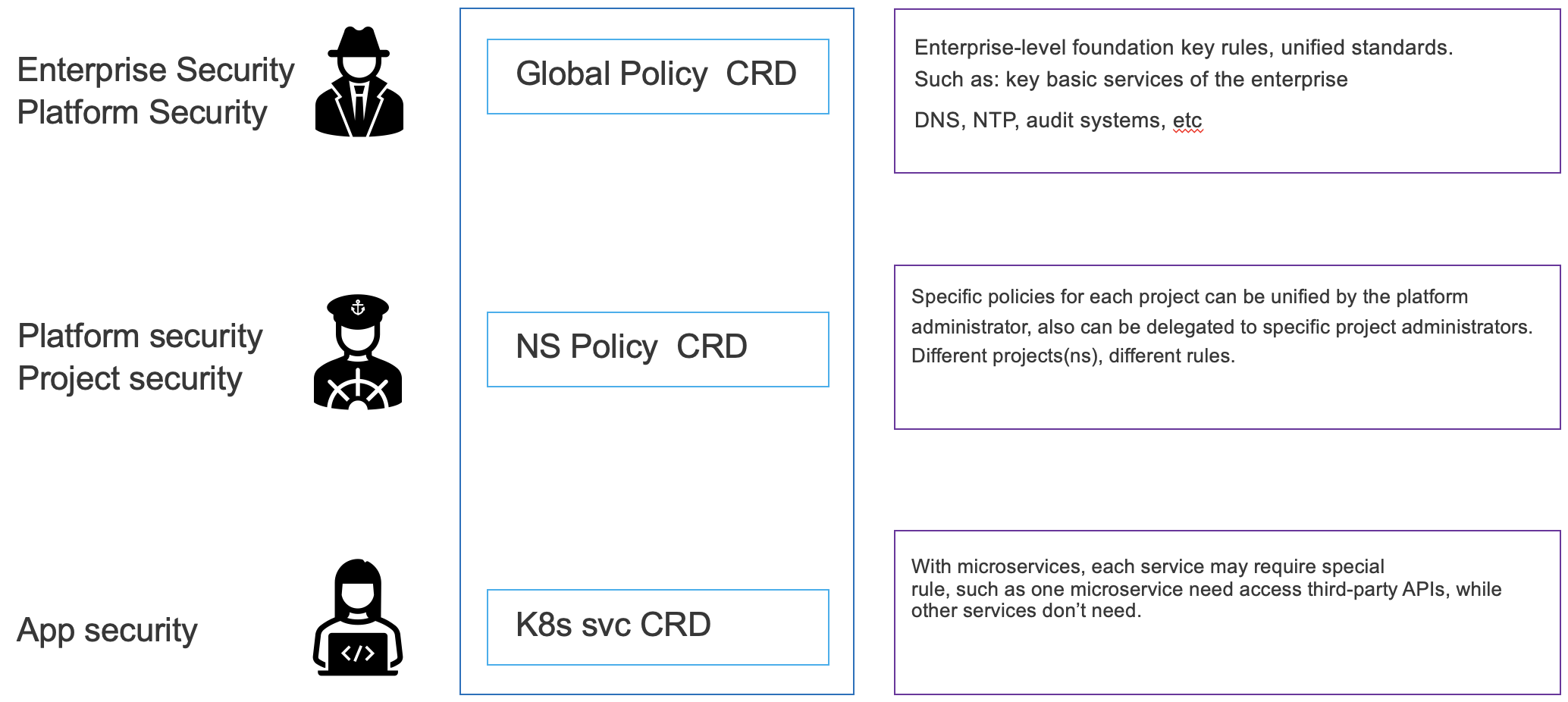
EN_4_CES_Global_policy
This policy scenario is used to control the egress traffic of the entire k8s cluster. Generally speaking, each cluster needs to access some basic external services, and these are required by all services in the entire cluster. The overall polices adopts the whitelist model, and the services that need to be accessed need to be set expilictly. Otherwise it will be rejected.
-
First create the target service to be accessed. The service needs to be located under the namespace where the CES control is running. Support IP, domain name, protocol combination, support any protocol only IP:
Note: If you would like to use FQDN in the externalservice, then pls config the FQDN resolver first in F5. You need
- Create DNS resolver in F5--Network-DNS Resolvers
- Reference the above DNS resolver in the F5--Security--Network Firewall options
kind: ExternalService apiVersion: kubeovn.io/v1alpha1 metadata: name: globalextsvcdns namespace: kube-system spec: addresses: - 8.8.8.8 - 114.114.114.114 ports: - name: tcp-53 protocol: TCP port: "53" - name: udp-53 protocol: UDP port: "53"apiVersion: kubeovn.io/v1alpha1 kind: ExternalService metadata: name: globalextsvchttp namespace: kube-system spec: addresses: - www.myf5.net - 60.28.100.46 ports: - name: tcp-80 port: "80" protocol: TCP - name: tcp-443 port: "443" protocol: TCPapiVersion: kubeovn.io/v1alpha1 kind: ExternalService metadata: name: test6extsvc-ip namespace: kube-system spec: addresses: - 17.171.117.17 - 18.18.18.18# kubectl get externalservices.kubeovn.io -n kube-system NAME ADDRESSES globalextsvcdns [8.8.8.8 114.114.114.114] globalextsvchttp [www.myf5.net 60.28.100.46] test6extsvc-ip [17.171.117.17 18.18.18.18] -
Create
clusteregressrulesresources. This resource has no namespace concept.# kubectl get clusteregressrules.kubeovn.io -A NAME ACTION STATUS global-policy-dns accept-decisively Success global-policy-http accept-decisively Success global-rule6-ip accept-decisively SuccessapiVersion: kubeovn.io/v1alpha1 kind: ClusterEgressRule metadata: name: global-policy-dns spec: action: accept-decisively externalServices: - globalextsvcdnsapiVersion: kubeovn.io/v1alpha1 kind: ClusterEgressRule metadata: name: global-policy-http spec: action: accept-decisively externalServices: - globalextsvchttpapiVersion: kubeovn.io/v1alpha1 kind: ClusterEgressRule metadata: name: global-rule6-ip spec: action: accept-decisively externalServices: - test6extsvc-ip status: phase: Success
Use 8.8.8.8 to do DNS resolution,it works
~ # dig @8.8.8.8 www.f5se.io +short
f5se.io.
185.199.109.153
185.199.110.153
185.199.111.153
185.199.108.153
But using 223.5.5.5, it fails:
~ # dig @223.5.5.5 www.f5se.io +short
; <<>> DiG 9.16.19 <<>> @223.5.5.5 www.f5se.io +short
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached
Visit www.myf5.net to access:
~ # curl www.myf5.net
<html>
<head><title>301 Moved Permanently</title></head>
<body bgcolor="white">
<center><h1>301 Moved Permanently</h1></center>
<hr><center>nginx</center>
</body>
</html>~ # curl www.myf5.net
<html>
<head><title>301 Moved Permanently</title></head>
<body bgcolor="white">
<center><h1>301 Moved Permanently</h1></center>
<hr><center>nginx</center>
</body>
</html>
Unable to access www.baidu.com:
~ # curl www.baidu.com
^C
Next step: